In a PART 1 of this blog, I wrote about Monitoring Windows Defender status for Intune MDM enrolled devices. In this part I’ll be focusing on Reporting and Monitoring Windows update for Intune MDM enrolled devices. Please read part 1 for a complete understanding.
Reporting and Monitoring Windows Update status
To enable monitoring and reporting for Intune MDM enrolled devices, you’ll have to setup an OMS workspace and deploy the Microsoft Monitoring Agent as discussed in part 1 of this blog. Monitoring Windows Update status required a separate OMS console in the past but now this data is available in the same Azure portal and you get information back from the devices out in the field. One console for all your monitoring data.
Microsoft has an article about Update Compliance. This solution uses the Windows diagnostic data that comes with Windows 10. It collects system data, and then sends this data privately to a secure cloud for analysis and usage within the Update Compliance solution.
This blog will guide you through the following steps that must be configured for Update Compliance to work;
- Add Update compliance to OMS
- Retrieve your commercial ID
- Enable Windows Telemetry
- Deploy commercial ID to devices
Add the Update Compliance to OMS
You can monitor Windows update compliance status in Intune or by using a solution in OMS called Update Compliance. By now you should know how to add a solutions to your OMS workspace. If not then please read part 1 of this blog. Go ahead and add the Update Compliance solution. You should also consider adding the Upgrade Readiness and Device Health solutions as well.
Commercial ID
Before you can actually use Update Compliance to collect data and monitor Windows updates, you will need to deploy the commercial ID, to you MDM enrolled devices. I can’t find the commercial ID in the Azure portal so I’ll point you to the classic OMS portal. If you did find it in the Azure portal than please share the knowledge.
- Navigate to >Azure Portal> Log Analytics
- In your list of Log Analytics workspaces, select your workspace (read part 1 for more info)
- Click on OMS Portal
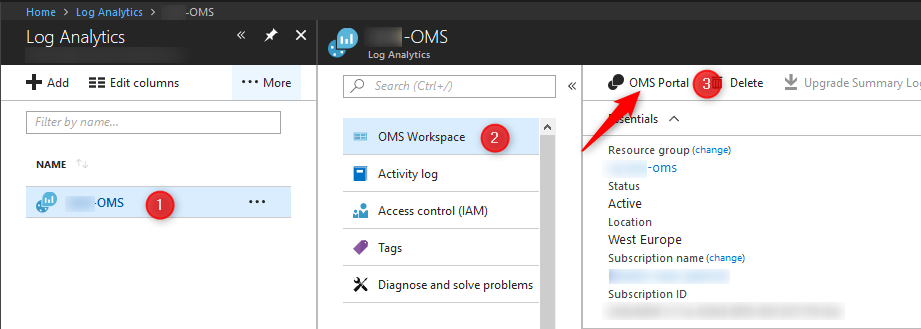
- The classic OMS portal will open
- Go to the settings page
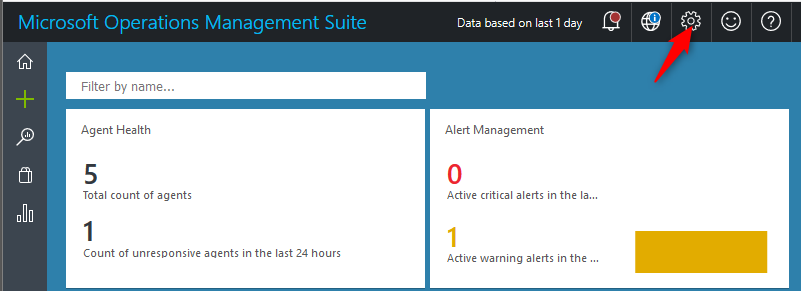
- Select Connected Sources and then select Windows Telemetry
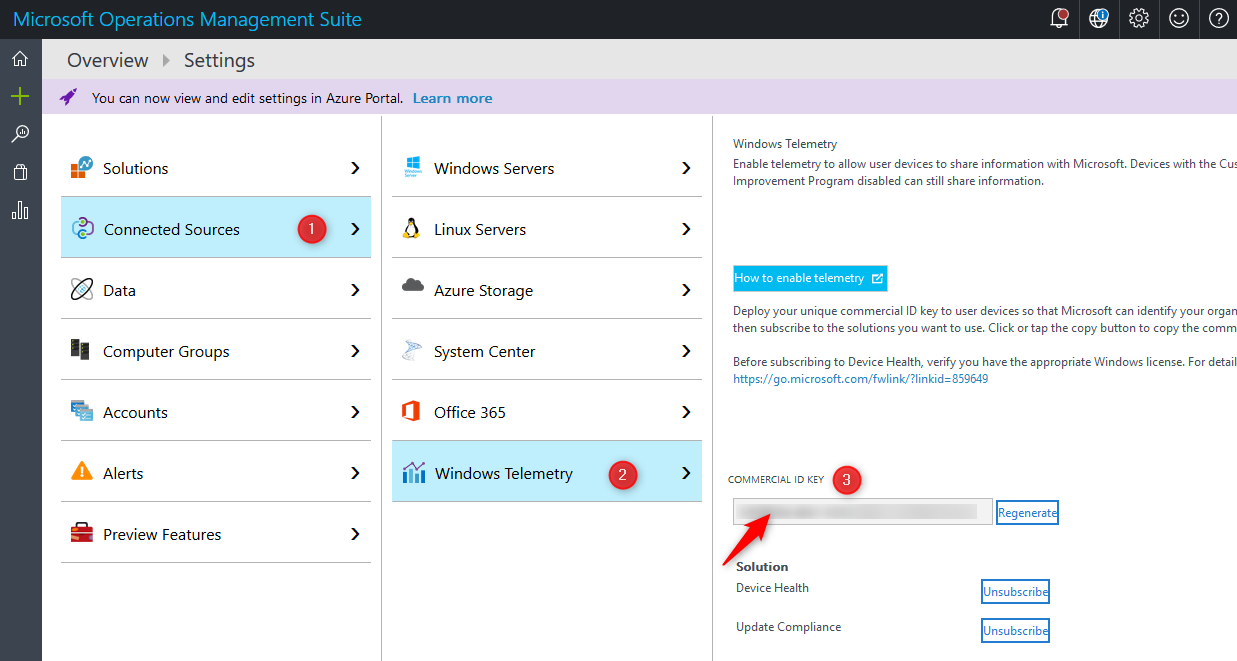
- Copy your Commercial ID key to notepad for later use
Note:
Regenerating your Commercial ID will reset collected data in your OMS workspace. You’ll need to deploy the new key to your devices
Enable Windows telemetry
Windows telemetry must be enabled and you’ll need Basic, Enhanced or Full diagnostic data level, for this to work. In this blog, I’ll be using MDM to configure and deploy the diagnostic data level setting, but you can also use Group Policy.
Use the appropriate value in the table below to set your diagnostic data level
| Level | Data gathered | Value |
| Security | Security data only. | 0 |
| Basic | Security data, basic system and quality data. | 1 |
| Enhanced | The above + enhanced insights & advanced reliability data | 2 |
| Full | The above and full diagnostics data | 3 |
You will need to create a device configuration profile. The Device Restriction profile type contains the settings for Reporting and Telemetry. Please read the Microsoft documentation if you need additional information or drop a comment below. I’ll walk you through the basics here to get you going. Perhaps a topic for another blog.
- Navigate to >Azure Portal> Intune> Device Configuration
- Select Profiles
- Click on Create profile
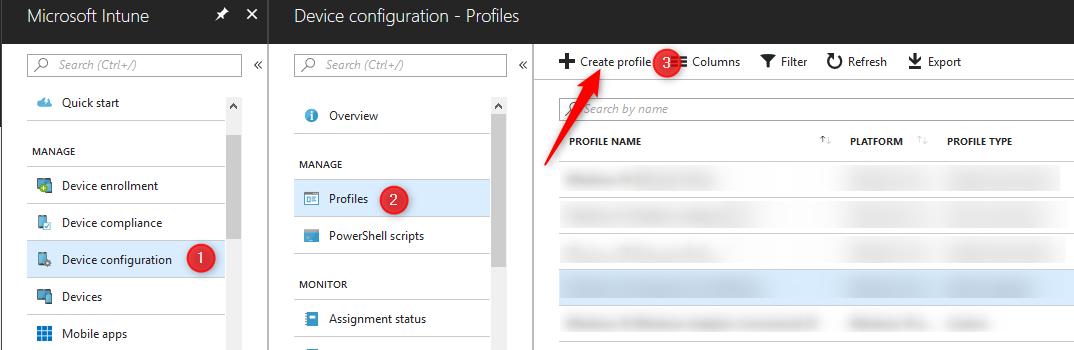
- Give your policy a name and a description
- Select Windows 10 and later as platform
- Select Device restriction as your Profile type
- Click Settings
- In the settings blade, scroll down to Reporting and Telemetry
- Select Basic, Enhanced or Full diagnostic data level
- Click OK and then click OK again
- Click Create to finally create your device configuration profile
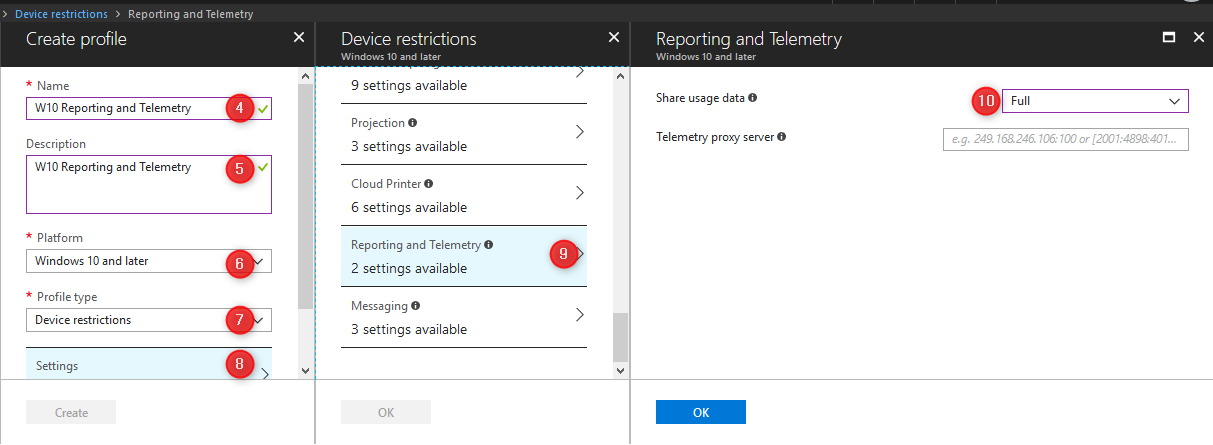
Note: Your Device configuration profile has been created but not assigned yet!
Assigning Device Configuration Profiles
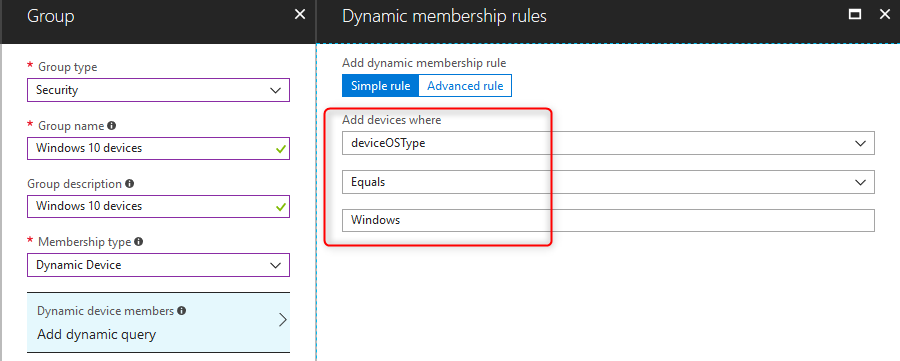
For this example I’ve created a dynamic security group that will contain all my Windows devices.
- Navigate to >Azure Portal> Intune> Groups> All groups
- Click on +New group
- Create your security group. Use the screenshot as an example
When the security group is created it will start of as an empty group. Give it some time to find your Windows devices. After a while you can look up your security group and have a look at the properties. The group is now populated with 26 Windows 10 devices.
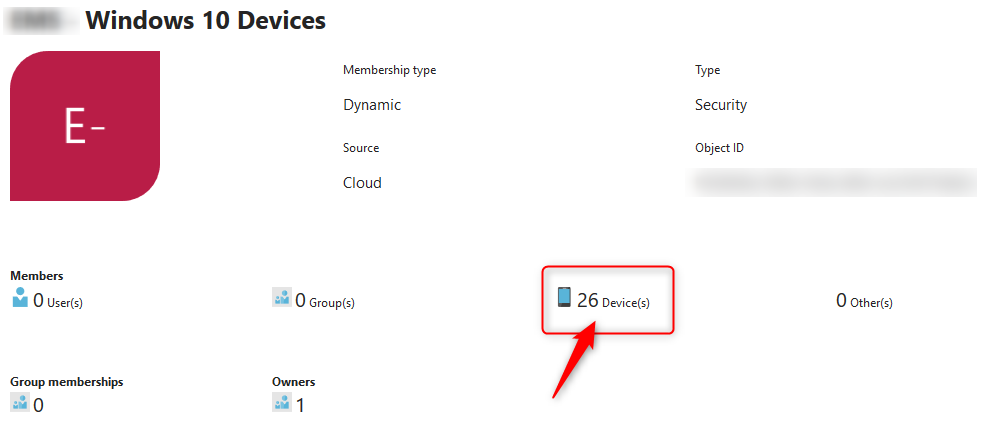
Read more about creating groups and dynamic groups if this is the first time you are creating groups in Azure.
When your security group is populated with devices, assign it to your device configuration profile.
- Navigate to >Azure Portal> Intune> Device Configuration> Profiles
- Select your profile in the list
- Click Assignments
- Click on Select groups to include
- Search for the security group you created and select it
- Finally don’t forget to click on Save to complete the assignment
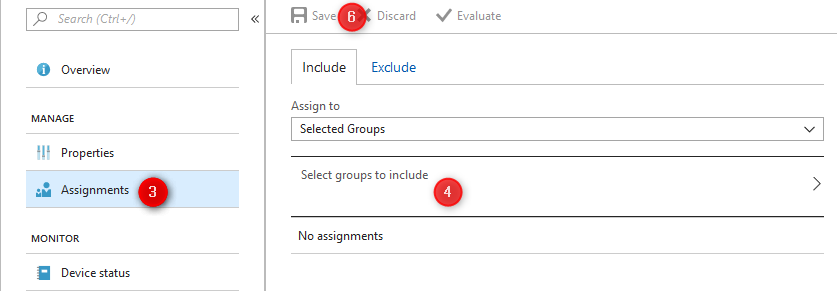
When your devices sync with Intune, they will receive this policy and the diagnostic data level will be set to Full.
Deploy Commercial ID to Windows devices
Besides enabling Windows Telemetry, you will also need to configure the Commercial ID on all your Windows devices. For this we will use the following OMA-URI (Open Mobile Alliance Uniform Resource Identifier) configuration:
| Setting Name | Windows Analytics Commercial ID |
| Setting Description | Configuring commercial ID for Windows Analytics solutions |
| OMA-URI | ./Vendor/MSFT/DMClient/Provider/MS DM Server/CommercialID |
| Data Type | String |
| Value | <your commercial ID> |
Note: OMA-URI is case sensitive!
We will deploy this setting (policy) by creating another Device Configuration Profile, just like you did for Windows Telemetry, but now we are going to create a custom profile.
- Navigate to >Azure Portal> Intune> Device Configuration> Profiles
- Click on Create Profile
- Select Windows 10 and later as platform
- Select Custom as your Profile type
- Click on Configure
- Click on Add
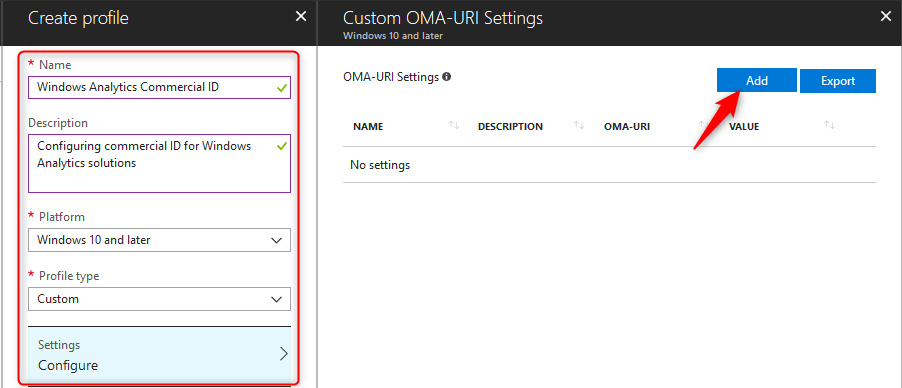
- Now fill in the blanks for your OMA-URI configuration
- Click OK and then click OK again
- Click Create to finally create your device configuration profile
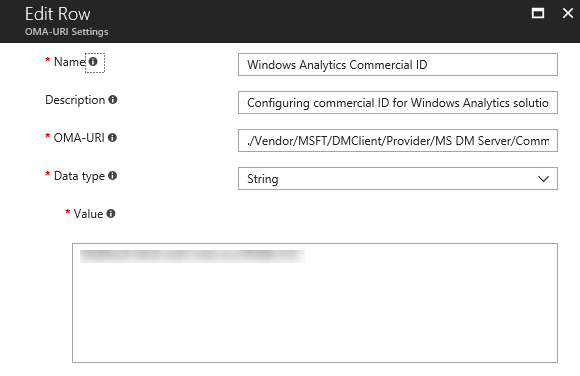
Just like with Windows Telemetry, you will need to assign this policy to a security group. After a while your devices will sync with Intune and configuration changes will be applied automatically.
Recap on what we did:
- We’ve Add Update compliance to OMS
- Retrieved our commercial ID
- Enabled Windows Telemetry on Windows devices
- Deployed the commercial ID to Windows devices
Using Update Compliance to Monitor Windows update
It might take up to 48 hours for information to appear in the OMS portal. Finally, when your devices start reporting, they do so with the Commercial ID associated to your OMS workspace. For this to work, Windows diagnostic data and data sharing also need to be enabled.
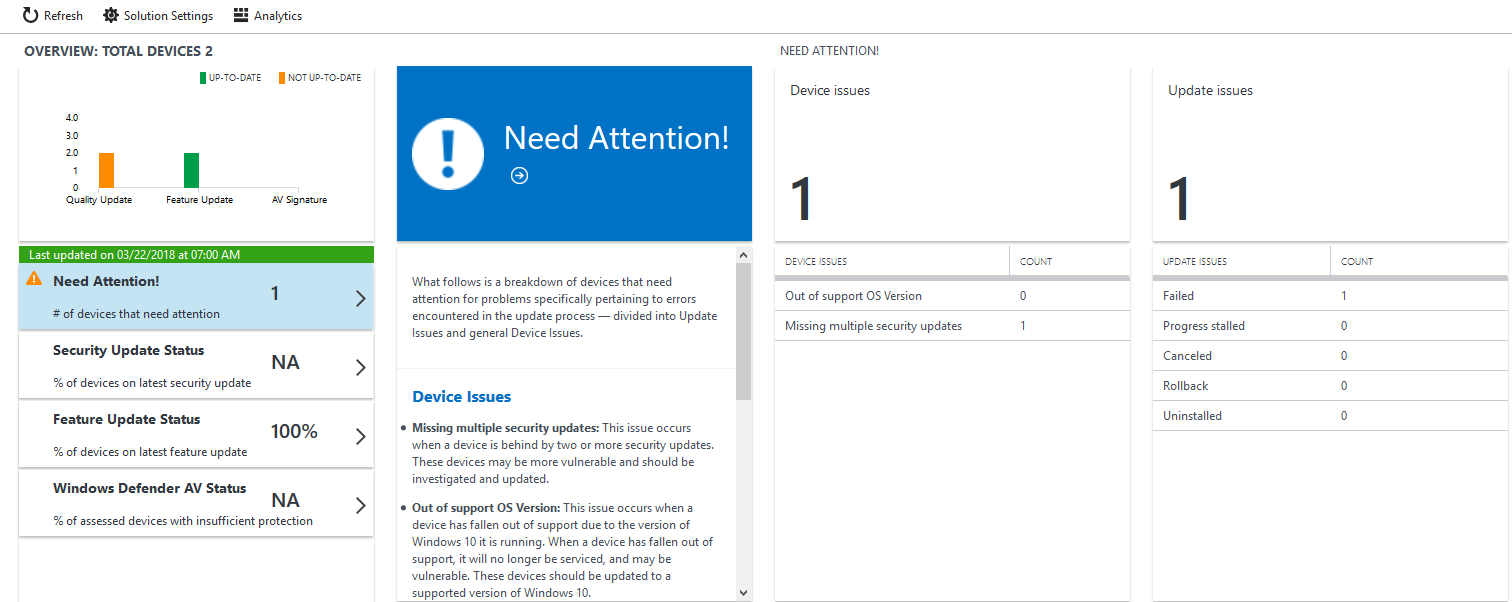
You can find the Update compliance solution in the overview of the OMS portal. Upon clicking the tile, you will be redirected to the Update Compliance workspace. The Overview Blade provides a hub from which to navigate to different reports of your device’s data. You can now use Update Compliance to monitor your device’s.
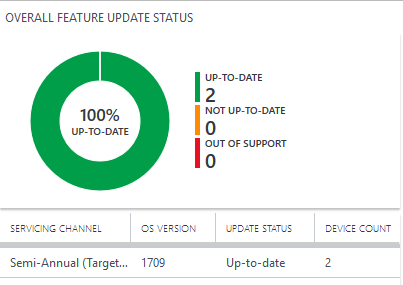 Overall feature update status
Overall feature update status
Windows 10 devices is up to date on feature updates whenever it has the latest applicable feature update installed. Feature updates are delivered more frequently than with previous Windows releases. Both Office 365 ProPlus and Windows 10 updates will deliver their major updates semi-annually, around April and September.
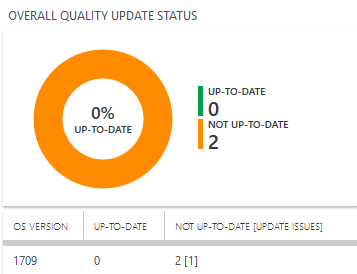
Overall quality update status
There is only one cumulative monthly update that supersedes the previous month’s update, containing both security and non-security fixes. This approach makes patching simpler and reduces unexpected issues resulting from patching.
In a previous blog I wrote about Configuring Windows Update for Business using Microsoft Intune, and Microsoft has a very comprehensive guide on using Update Compliance.
Troubleshooting
The Microsoft documentation is confusing and I’ll try to explain to the best of my knowledge. Also read the comments below the Microsoft article. The article writes, and I quote:
The OMA-URI (case sensitive) path for configuring the commercial ID is: ./Vendor/MSFT/DMClient/Provider/ProviderID/CommercialID
For example, you can use the following values in Add or edit OMA-URI Setting:
- Setting Name: Windows Analytics Commercial ID
- Setting Description: Configuring commercial ID for Windows Analytics solutions
- OMA-URI (case sensitive): ./Vendor/MSFT/DMClient/Provider/ProviderID/CommercialID
- Data Type: String
- Value: <Use the GUID shown on the Windows Telemetry tab in your OMS workspace>
When you configure the OMA-URI as suggested in the Microsoft article, you will receive an error in Intune, showing a conflict. There is no other information or error codes to work with.
Update on Microsoft documentation:
The Microsoft documentation has been updated/corrected. I’m leaving this section here because I’ve seen other blogs and article’s still using the configuration above. I can imagine not everyone will or can update their articles as quick as Microsoft does and hope by leaving it here, it may still help someone troubleshoot this problem.
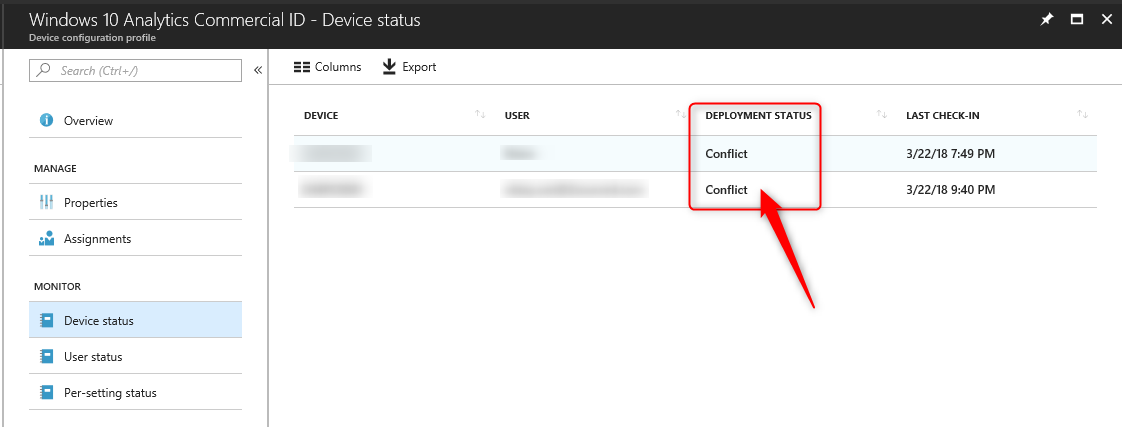
The Official DMClient CSP documentation contains the solution here:
Provider/ProviderID
Required. This node contains the URI-encoded value of the bootstrapped device management account’s Provider ID. Scope is dynamic. This value is set and controlled by the MDM server. As a best practice, use text that doesn’t require XML/URI escaping.
For Intune, use MS DM Server for Windows desktop or SCConfigMgr for Windows mobile for the ProviderID.
Therefore I used the following OMA-URI setting:
- OMA-URI: ./Vendor/MSFT/DMClient/Provider/MS DM Server/CommercialID
Consequently, when the policy is applied to your Windows 10 devices, Intune will report ‘succeeded’
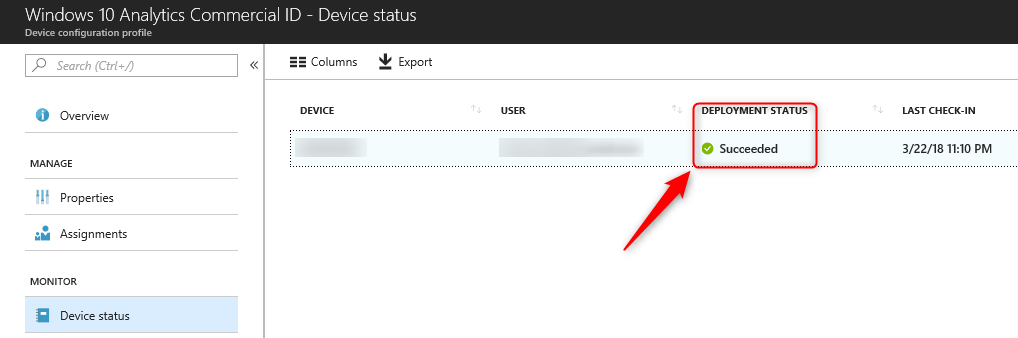
On the device, you can confirm everything is working by checking your settings and registry
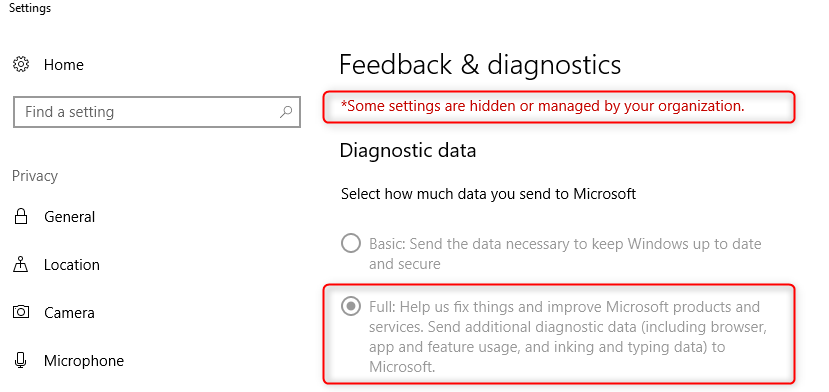
Your Commercial ID will be stored at:
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\DataCollection\CommercialID
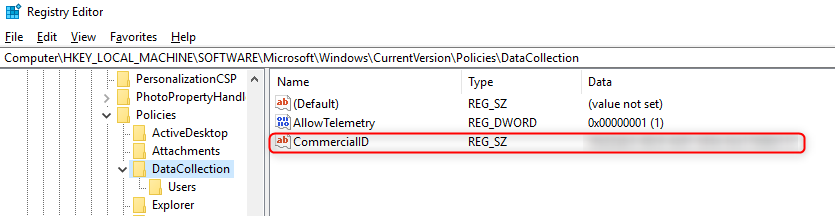
Your Windows Telemetry diagnostics data level is stored at:
HKLM\SOFTWARE\Policies\Microsoft\Windows\DataCollection\CommercialID
This concludes the second part of this blog. Finally you have a complete reporting portal while your devices are MDM enrolled to Azure Intune.
Additional Information
- Manage software updates
- Enrolling devices in Windows Analytics
- Monitor Windows Updates and Windows Defender Antivirus with Update Compliance
- Configure Windows diagnostic data in your organization
- Use Update Compliance
- Add groups to organize users and devices
- Create attribute-based rules for dynamic group membership in Azure Active Directory
- Configuration service provider reference
- Policy CSP
- DMClient CSP
- Microsoft Intune custom device settings for devices running Windows 10
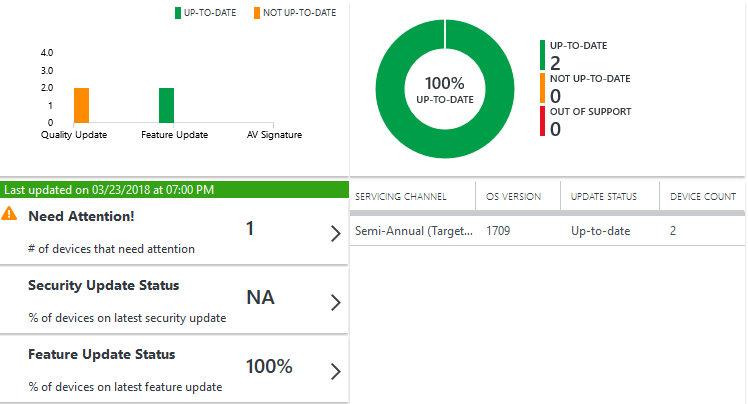
The commercial ID can be found in the “Device Health Settings” tab of the DeviceHealthProd solution for a Log Analytics workspace once it has been added.
Hi Max, Thx for your feedback! I’ll be writing an update on this post soon. 🙂