In the ever-evolving battleground of endpoint security, Microsoft Defender for Endpoint stands as a vigilant guardian against the rising tide of cyber threats. But even the best guardians can sometimes be a bit… forgetful. What happens when your Microsoft Defender PUA Policy settings start changing mysteriously on your macOS devices? In my previous post we […]

How I Accidentally Fort Knox’d myself: A macOS Security Hardening Tale
The Road to Better Security Is Paved with Infinite Login Loops If you’re reading this, you probably care about macOS security hardening. And like me, you might be interested in hardening your macOS devices according to industry standards. But let me tell you a cautionary tale about implementing security measures without proper testing, or as […]
Advanced macOS Protection with Microsoft Intune – Beyond the Basics
Advanced macOS Protection with Microsoft Intune: The Security Sequel You Didn’t Know You Needed!🚀 Hey there, security enthusiasts and Mac wranglers! Remember when we thought CIS Level 1 was the cool kid on the block? Well, grab your Terminal windows and hold onto your MDM profiles, because Level 2 is here to rock your config. […]

Book Review: Mastering Windows 365
Mastering Windows 365 by Christiaan Brinkhoff, Sandeep Patnaik, and Morten Pedholt Introduction After days of exploring Mastering Windows 365, I can confidently say this book offers more than technical guidance alone. It’s a complete roadmap to mastering Windows 365. Christiaan Brinkhoff, Sandeep Patnaik, and Morten Pedholt deliver practical knowledge, real-world experience, and step-by-step strategies that […]
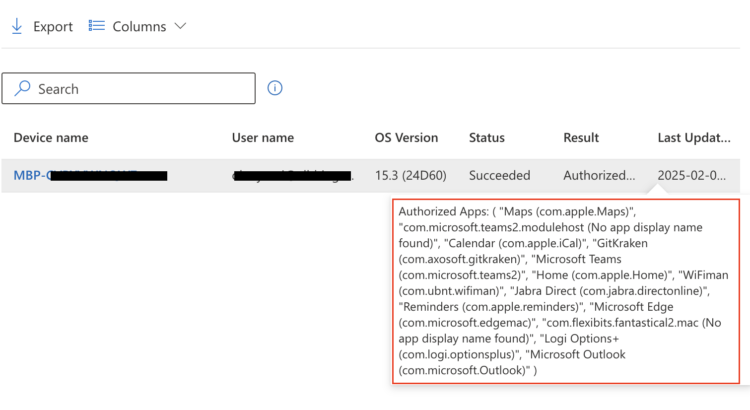
Who’s Watching? Auditing macOS Location Services with Intune.
In my ongoing mission to strengthen macOS device security with Microsoft Intune, today I’m focusing on macOS Location Services, and 2 recommendations from the CIS Level 2 benchmarks for macOS devices. We’ll explore recommendation 2.6.1.2 Ensure ‘Show Location Icon in Control Center when System Services Request Your Location’ Is Enabled and recommendation 2.6.1.3 Audit Location […]
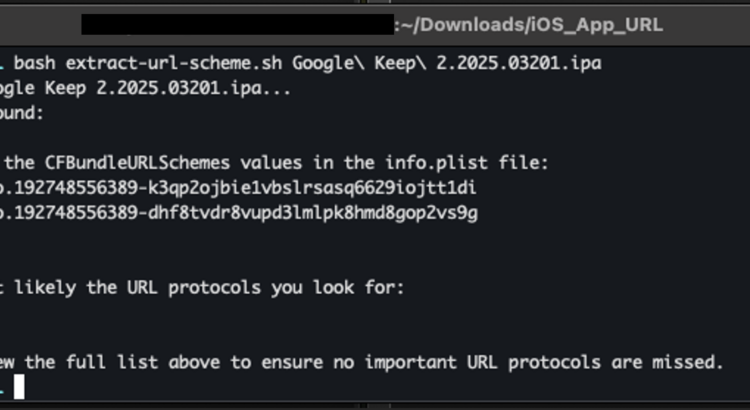
iOS MAM Policies; Discovering URL Protocols and Data Transfer Exceptions
It’s been a while since I did a blog on Mobile Application Management (MAM) policies, the unsung heroes of modern IT security. They quietly ensure that corporate data stays safe, even on personal devices. However, when it comes to data transfer exceptions, those tricky settings that allow unmanaged apps to interact with managed app data, […]

macOS Security with Intune – From Basics to Bulletproof
Let’s be real—‘bulletproof security’ sounds cool, but in the world of cybersecurity, it’s more of a myth than a reality. Threats evolve faster than we can patch things, and there’s always a clever hacker out there looking for a way to crack your macOS Security. The goal here isn’t perfection; it’s about staying ahead of […]

Book review – Mastering Microsoft Intune
Normally, I don’t venture into book reviews, but “Mastering Microsoft Intune” by Christiaan Brinckhoff and Per Larsen compelled me to make an exception. Why? For anyone serious about Windows 365 and Microsoft Intune, this book is a crucial navigator to where you want to be. If you’re an IT pro, it definitely deserves some real […]
macOS App Deployment with Microsoft Intune: An In-Depth Guide
In today’s modern workplace, where macOS is becoming more popular, the ability to deploy and manage applications is crucial. Microsoft Intune offers powerful and versatile solutions for managing macOS applications, enabling organizations to automate the deployment process, enforce security policies, and provide centralized management. Introduction to macOS App Deployment with Microsoft Intune This guide aims […]

Managing macOS with Intune: Into the belly of PLIST files
Most of my blogging journey has been all about Microsoft Intune and Windows devices – But hey, change is the spice of life, or so they say. So, this year, I decided it’s time to mix things up a bit. I’ve jumped on the macOS bandwagon, got myself a shiny new Apple device, and have […]