Today, we’re once again diving into deploying network drive mappings on macOS with Microsoft Intune, but with a twist! We’re showcasing an enhanced version of the previous shell script that’s been turbocharged with new features and improvements. Fasten your seatbelts – it’s time for an upgraded ride in the world of automation. You can read […]
Deploy Network Drive Mappings on macOS with Microsoft Intune
Update: Check out the new version of this script. Turbocharged with new features and improvements Revamping Network Drive Mappings on macOS with Intune Welcome, fellow tech adventurers, to the world of macOS management with a dash of Microsoft Intune magic! Today, we’re going to explore how you can deploy network drive mapping on macOS devices […]
Still going passwordless
Last year, I had the opportunity to do in-person presentations about going Passwordless and also wrote many blogs about this topic. In this post I wanted to share some of the information I talk about during these presentations and give you a better idea of why you should consider going passwordless. I will also share […]

Microsoft Ignite 2022
In this post I’ll focus on the highlights and announcements around Microsoft Intune and Security during Microsoft Ignite 2022. I will also try to give an impression of my experiences during Ignite 2022. Microsoft Ignite 2022 (Oct 12 – 14) was perhaps different than any other Ignite I attended before but looking back I’m still […]
Uninstall ESET Endpoint Security with Intune Proactive Remediations
This is going to be a short blogpost showing you how to uninstall ESET Endpoint Security with Intune Proactive Remediations. I was working on a project where the customer had Windows 10 and Windows 11 devices enrolled with Microsoft Endpoint Manager (Intune) but still used ESET Endpoint Security. One of the requirements was to migrate […]

Working passwordless on Mobile devices
In my previous post “What is your excuse for passwords”, I wrote about going passwordless all the way and how to enroll a Windows device with Autopilot using Azure Temporary Access Pass (TAP), and a FIDO2 security key. Working passwordless on Windows is easy, but when it comes to working passwordless on Mobile devices like […]

What is your excuse for passwords
What is your excuse for passwords and why is it, that we still heavily rely on passwords? Is it because passwords are easier to remember by end-users, or is it that someone thinks that end-users are not capable of handling anything else then a simple password. In other words, do we tend to think of […]
Conditional Access policies in Report-only Mode. Now what?
Conditional Access policies in Report-only Mode…Now what? Conditional access policies in Report-only mode allow you to evaluate the impact of Conditional Access policies before you enable them. For instance, you can see conditional access policies in Report-only mode in the Azure AD sign-in logs, but there’s more to it and that’s what this post is […]
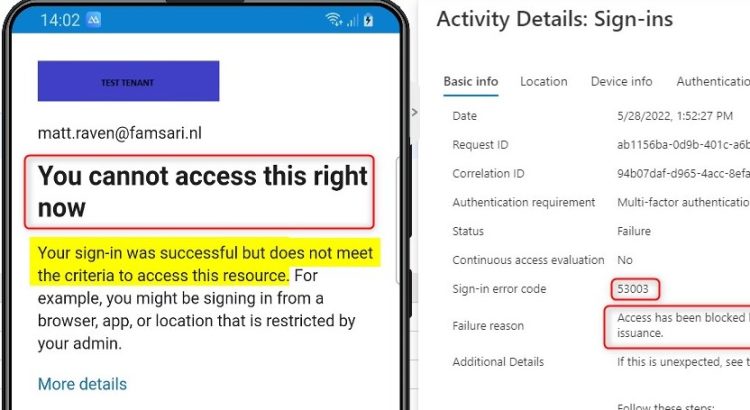
Blocking access to Microsoft 365 outside the Android for Work Profile with Endpoint Manager
This post is about blocking access to Microsoft 365 outside the Android for Work Profile with Endpoint Manager. After seeing a question on techcommunity I thought I might as well do a quick post on this topic. Please note: Normally you would block access to Microsoft 365 resources by using a combination of device compliance […]

What Zombies can teach you about Security Baselines
This month, we had a company event at Rapid Circle and I did a presentation about Security Baselines vs Endpoint Protection templates vs Settings Catalog vs device configuration policies. Yeah… that’s a mouth full. For a change, I didn’t want to do a technical deep dive, but instead, talk more about some best practices and […]
