Last Updated on December 31, 2023 by Oktay Sari
July 2022
IMPORTANT UPDATE: Microsoft announced the sunset for Windows Information Protection! WIP will be discontinued over time. Support for Windows Information Protection Without Enrollment will end by the end of calendar year 2022. Please read the official announcement and more on the following 2 sites:
- Announcing the sunset of Windows Information Protection (WIP)
- Support tip: End of support guidance for Windows Information Protection
If you have plans to implement WIP, I suggest you rethink your strategy accordingly. I will follow-up on this and update the WIP posts I have when more information is released by Microsoft.
Let’s have a look at collecting WIP audit event logs using Azure Monitor and how to read and monitor event logs from Windows 10 devices. Windows Information Protection offers data separation, keeping corporate and personal data separate, and leak protection, by blocking the use of cut and paste actions. Most events triggered by Windows Information Protection are logged in the event log. Collecting WIP audit event logs to a central place Like Log Analytics will help a lot.
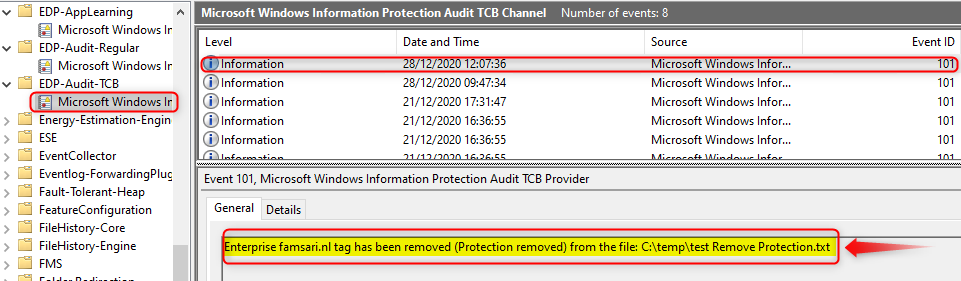
You can find these event logs under: Application and Services Logs\Microsoft\Windows
- EDP-Application-Learning
- EDP-Audit-Regular
- EDP-Audit-TCB
For example, when file ownership is changed from work to personal, or when corporate data is shared by moving a file to a USB drive or by copy/paste actions between apps. These actions are written to the event logs. To be able to audit the event logs from all your devices you will need to consolidate all these logs in one place. Otherwise it’s going to be a full-time job. In this post we’ll be collecting WIP audit event logs using Azure Monitor and Azure Log Analytics.
There are a couple of other post you might want to read: This post is part of a series.
- Introduction to Windows Information Protection
- Configuring MDM user scope and MAM user scope
- WIP-WE / MAM – Windows Information Protection without enrollment
- Windows Information Protection with Enrollment
- Windows Information Protection User Experience
- WIP-WE User Experience – WIP Without MDM enrollment
- Set up Azure Rights Management for WIP
- WIP Without Enrollment Selective Wipe
- Troubleshooting Windows Information Protection
- Monitoring and collecting WIP audit event logs (this post)
- WIP Learning mode
- Support Windows 10 BYOD with Microsoft Endpoint Manager and WIP-WE
Prerequisites
- Intune MDM enrolled Windows 10 device
- an existing or a new Log Analytics workspace
- The Microsoft Monitoring agent installed on MDM enrolled Windows 10 devices
- Be sure to check the network requirements
WIP monitoring Limitations
The Microsoft Monitoring Agent collects the events and sends them to Azure Log Analytics. Deploying software using Intune, can only be done on devices that are MDM enrolled. Therefore, you’ll need Windows 10 devices that are MDM enrolled with Intune. Collecting WIP audit event logs from personal (BYOD) devices (Azure AD registered) is not possible by default. This is only possible when users choose to MDM enroll their personal devices! I haven’t tested installing the MMA manually on BYOD Azure AD registered devices, but that might be an option to further explore.
WIP and Azure Log Analytics Workspace
Use an existing Workspace or create a new Log Analytics Workspace. I’m assuming you know how to set up Log Analytics. If not, check out the Microsoft documentation here.
The Microsoft documentation about Collecting WIP audit logs using Azure Monitor is quite OK on this one, but does need an update. The Workspace ID and Primary key have been moved from advanced settings to agents management. I’ve added some screenshots to further explain the process.
- Go to Log Analytics->Advanced Settings->Data->Windows Event Logs
- add the logs you want to be send to Azure Log Analytics
There are 3 logs you’ll want to collect data from and I’ll go into more detail a little further below.
- Microsoft-Windows-EDP-Application-Learning/Admin
- Microsoft-Windows-EDP-Audit-Regular/Admin
- Microsoft-Windows-EDP-Audit-TCB/Admin
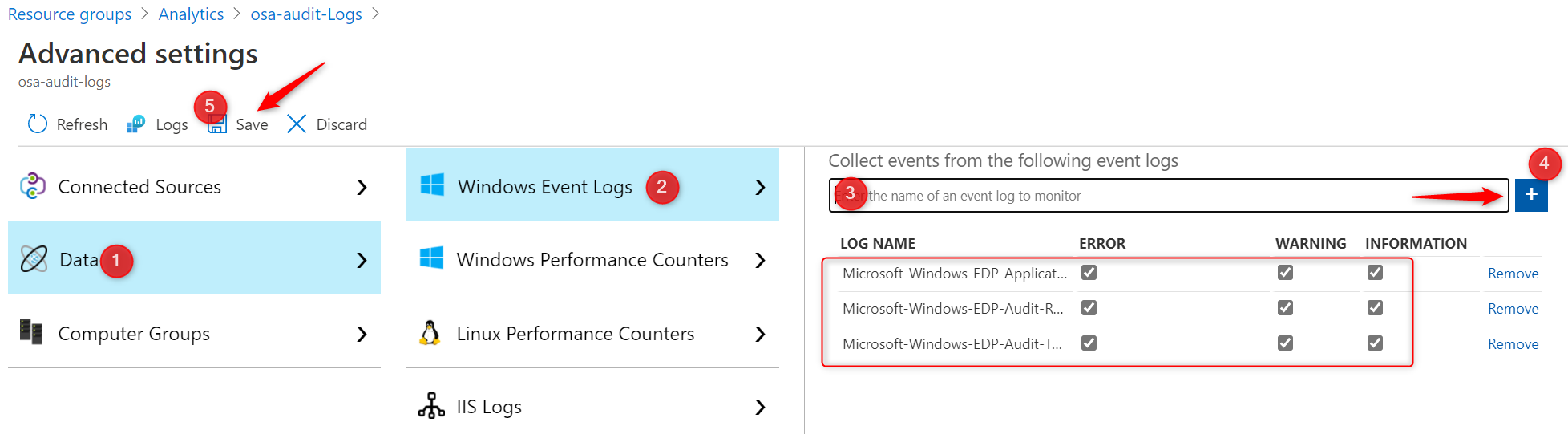
Note: Don’t forget or skip step 2! Otherwise you’ll not be able to analyze the logs in Azure.
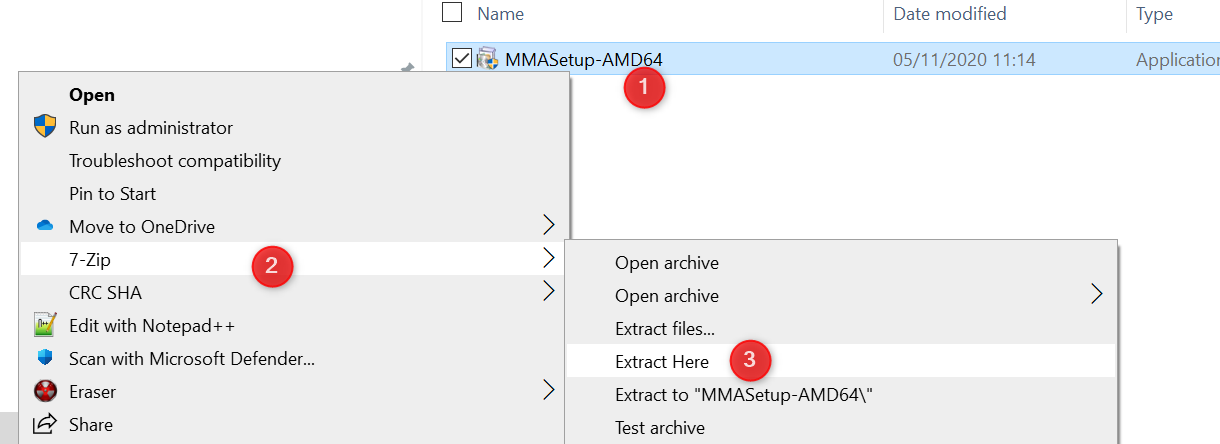
- Download the Microsoft Monitoring Agent here. You can also download the agent from Azure Log Analytics. Click on Agents management on the right and download your agent from there.

- The download contains a .EXE file but you can extract the .MSI file. I use 7-zip to do this
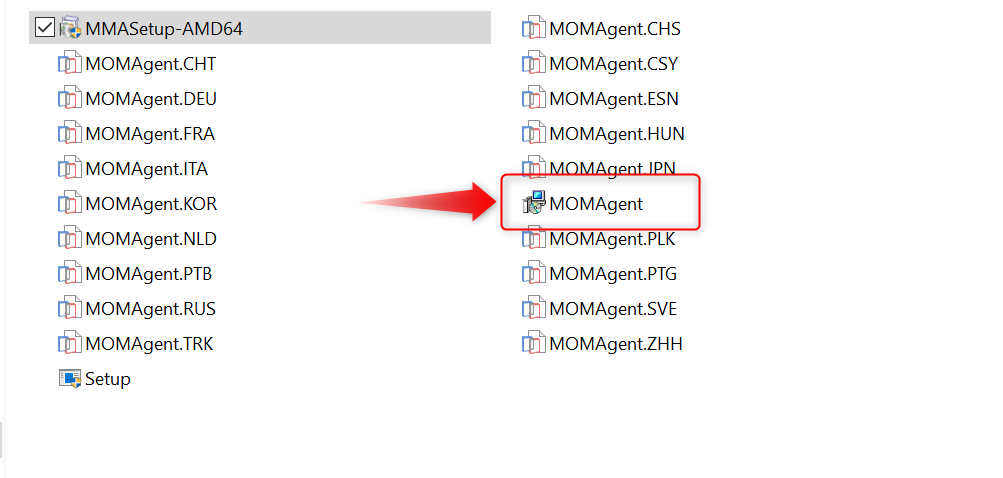
- Now you can deploy the MSI file with Intune. You only need 1 file: MOMAgent.msi
- Install the MOMAgent.msi to your WIP protected devices using the Workspace ID and Primary key from “Log AnalyticsAgents Management” where you’ve downloaded the agent.
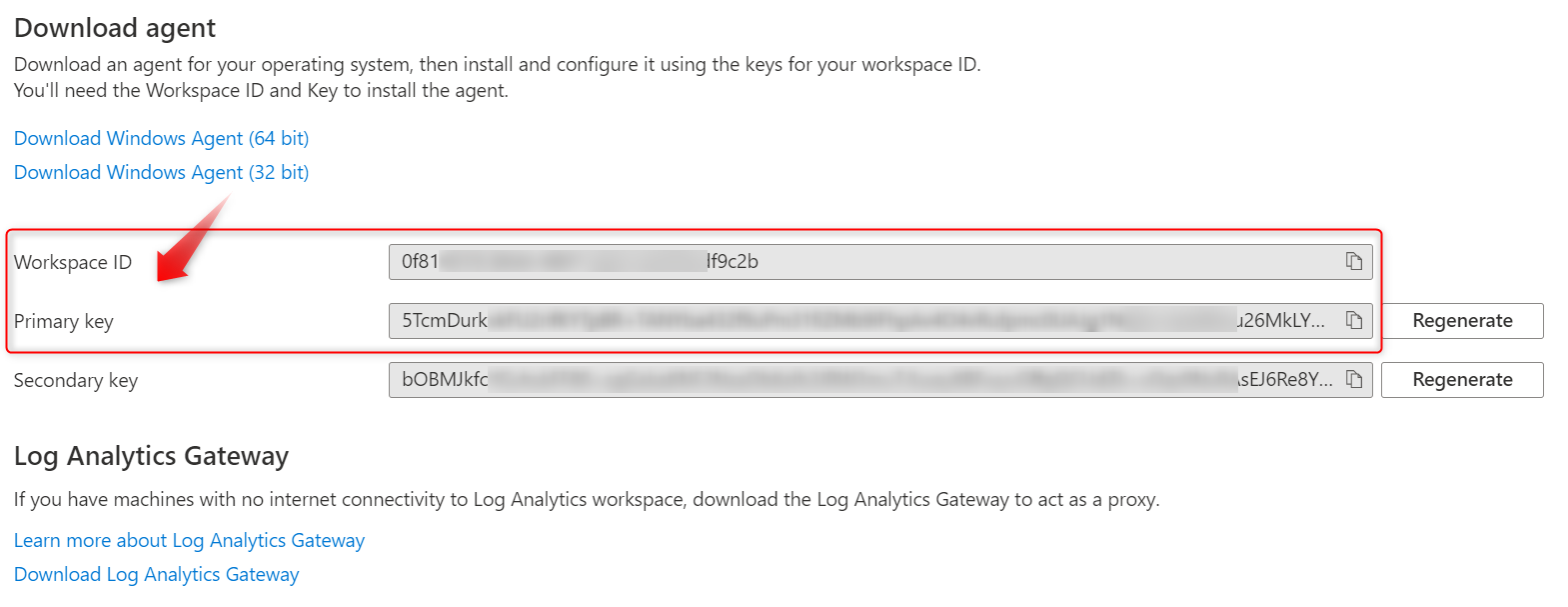
- To deploy the MSI file via Intune, and make sure you update the command-line arguments:
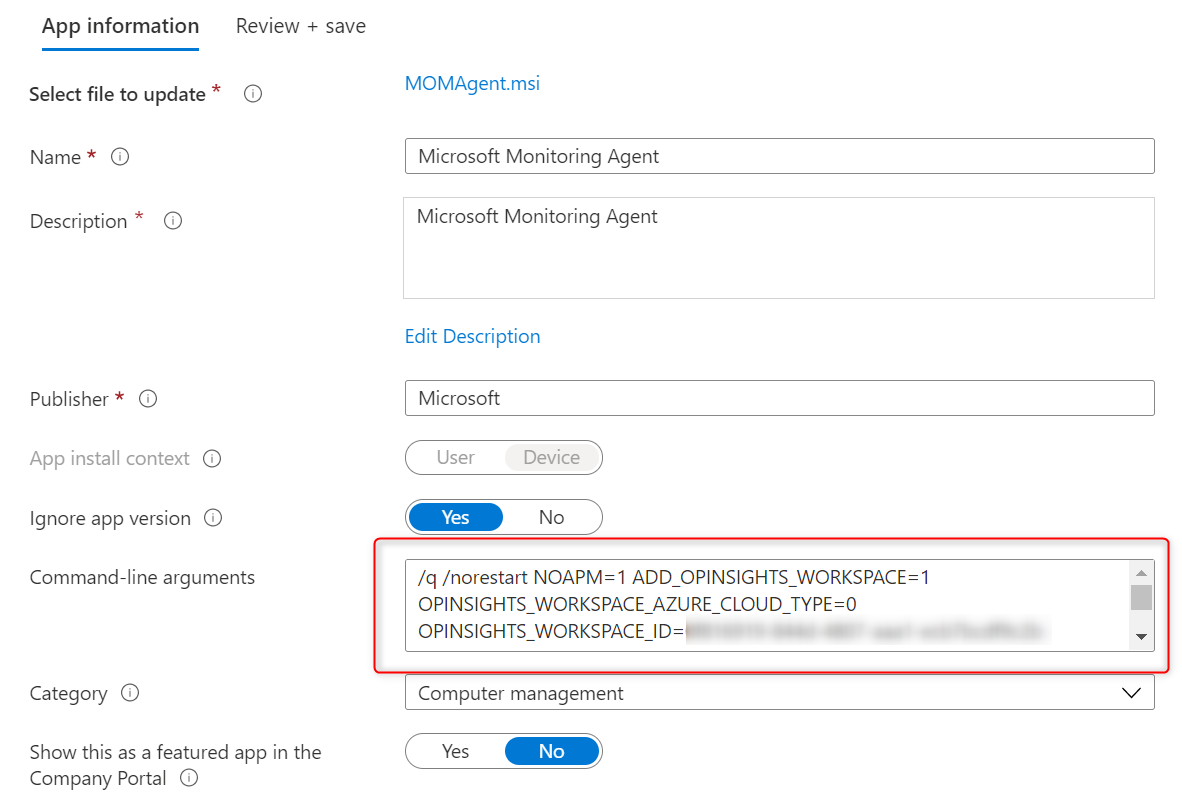
/q /norestart NOAPM=1 ADD_OPINSIGHTS_WORKSPACE=1 OPINSIGHTS_WORKSPACE_AZURE_CLOUD_TYPE=0 OPINSIGHTS_WORKSPACE_ID=0f81xxxx-0000-xxxx-0000-xxxxxxxf9c2b OPINSIGHTS_WORKSPACE_KEY=5TcmDurkxxxxxxxxxxxxxxx000000000000xxxxxxxx0000000000xxxxxxxxxx0000000000xxxxxxxxxx0000026MkLYQ AcceptEndUserLicenseAgreement=1REPLACE the WORKSPACE_ID & WORKSPACE_KEY with your own keys. The above keys in bold are for illustration purposes only but I guess you get that.
- You can check the agent deployed status in Intune and start receiving data in about 10 minutes after installation completes.

Analyzing WIP event logs
So you’ve configured your Log Analytics Workspace and installed the Microsoft Monitoring Agent on your devices right? You cannot wait to see what data is going to pop-up in Log Analytics. But what kind of data can you find in the 3 Event logs you’ve added in step 2 before?
If you followed this post to add the event logs to your Log Analytics Workspace there a 3 logs to monitor for events.
- Microsoft-Windows-EDP-Application-Learning/Admin
- Microsoft-Windows-EDP-Audit-Regular/Admin
- Microsoft-Windows-EDP-Audit-TCB/Admin
Microsoft-Windows-EDP-Application-Learning/Admin
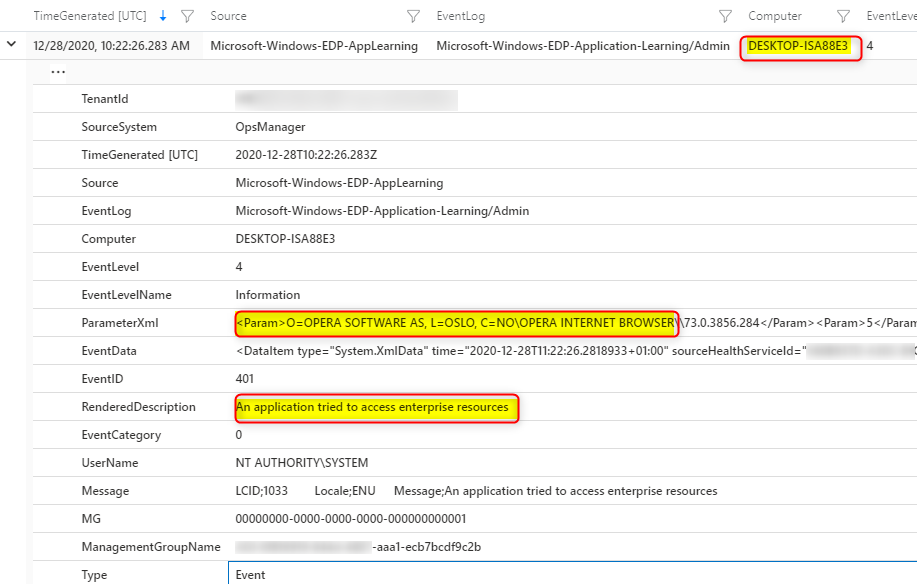
This log will collect information on applications that try to access enterprise resources. When you look at the events on the device itself, you’ll see event ID 401 “An application tried to access enterprise resources” When you look at the details, you will also see which app was trying to access your WIP protected data. In this example it’s Dropbox.
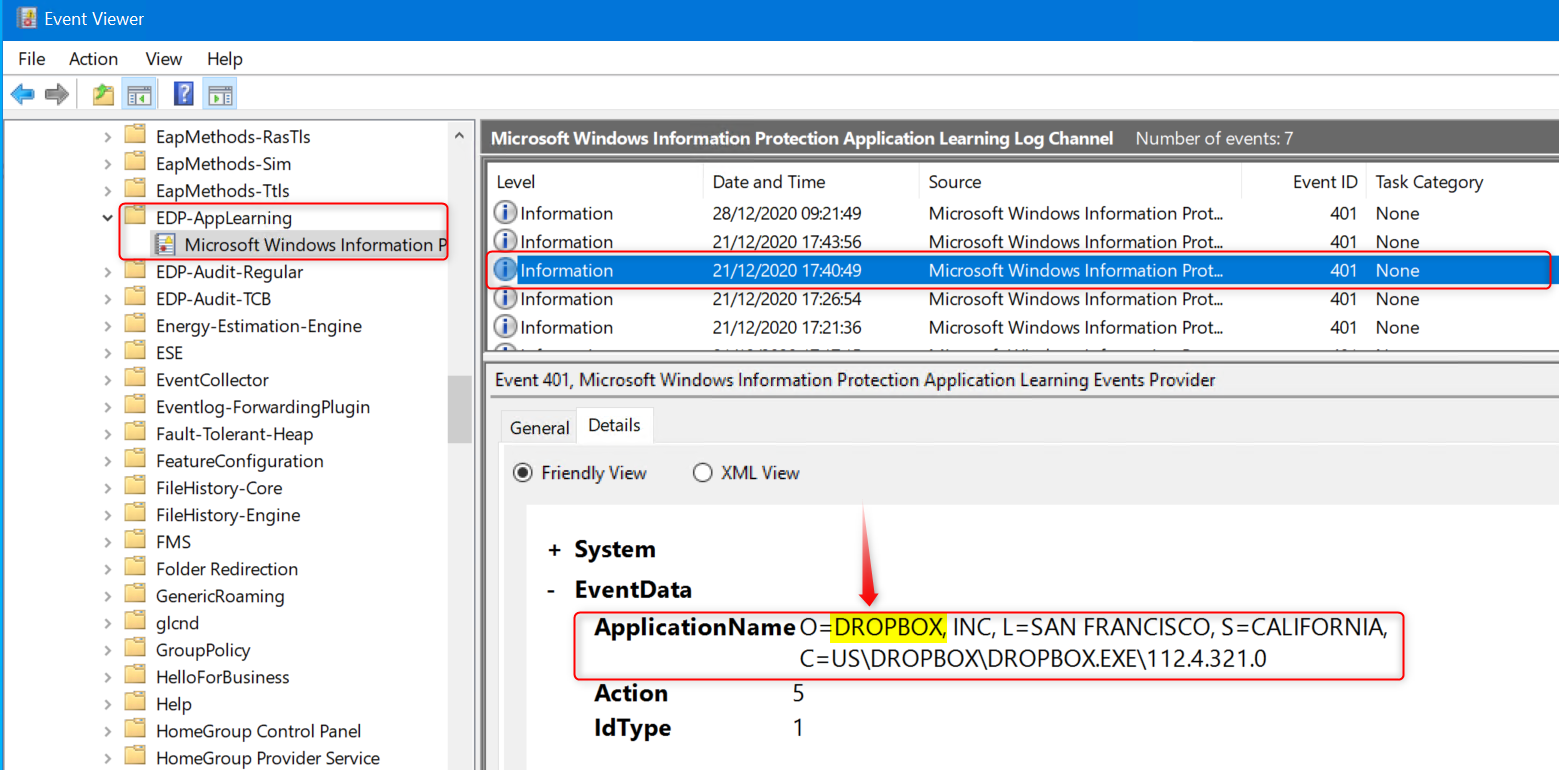
In the example above, the app trying to access enterprise data is Dropbox. I know Dropbox is not on the allowed apps list so this tells me it probably did not succeed in accessing or synchronizing data to Dropbox. But I have my WIP policy set to “Allow override”. What if the user changes file properties and removes protection by changing the File ownership to personal? That action will end up in Microsoft-Windows-EDP-Audit-TCB/Admin.
More on that later, but first let’s have a look at another example. The user is going to upload a WIP protected file as an attachment in Gmail. When using Google Chrome, which is also not on the allowed apps list, the action is logged. Same as with Dropbox. There was an attempt to access WIP protected data with an application, but the user probably clicked on the No button when confronted with the “Use work content here?” pop-up, so it’s OK up to this point.
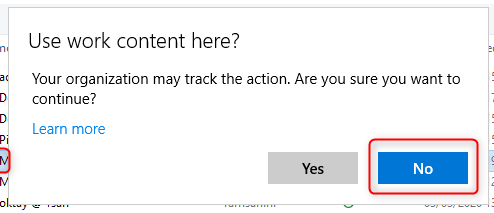
When the user clicks on Yes, the WIP protection is removed and another event is written to Microsoft-Windows-EDP-Audit-Regular.
Microsoft-Windows-EDP-Audit-Regular/Admin
When applications access WIP protected files and the user is allowed to remove protection, upon doing so, this action will be audited and the event written to the Microsoft-Windows-EDP-Audit-Regular/Admin log.
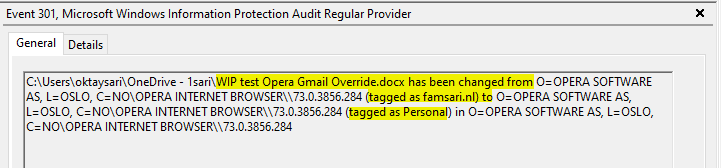
In the next example, a user tries to upload a WIP protected file using the Opera browser to Gmail. As you’ve seen before, the action will be audited and an event is written to Microsoft-Windows-EDP-Application-Learning/Admin when the user clicks on No. If the user clicks on Yes and removes the WIP protection, the action is also audited and an event is written to the Microsoft-Windows-EDP-Audit-Regular/Admin. Do you still follow me on this one?
Have a look at the screenshot below from the event log on my Windows 10 test device.
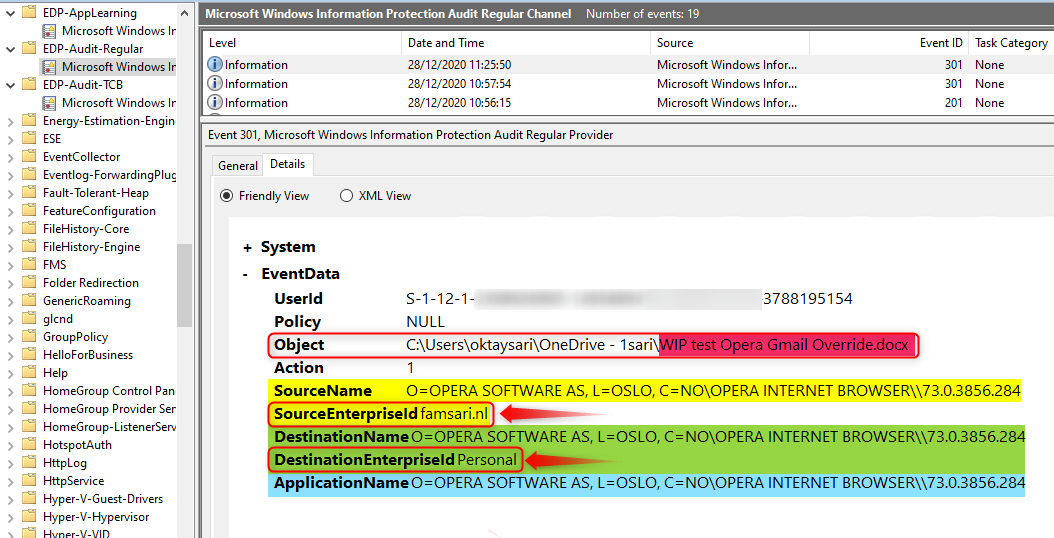
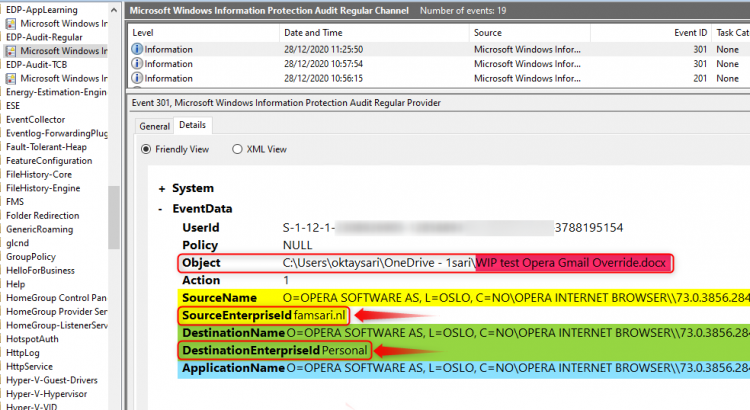
- The Object is a word document named WIP test Opera Gmail Override.docx
- SourceName is the name of the application from where the file is being accessed.
- SourceEnterpriseId is showing the enterprise tag. The file is protected!
- DestinationName is the name of the application to where the file is being transferred/copied.
- DestinationEnterpriseId shows the file has changed from corporate to personal!
- And then you have the ApplicationName which is the Opera browser in this example.
Microsoft-Windows-EDP-Audit-TCB/Admin
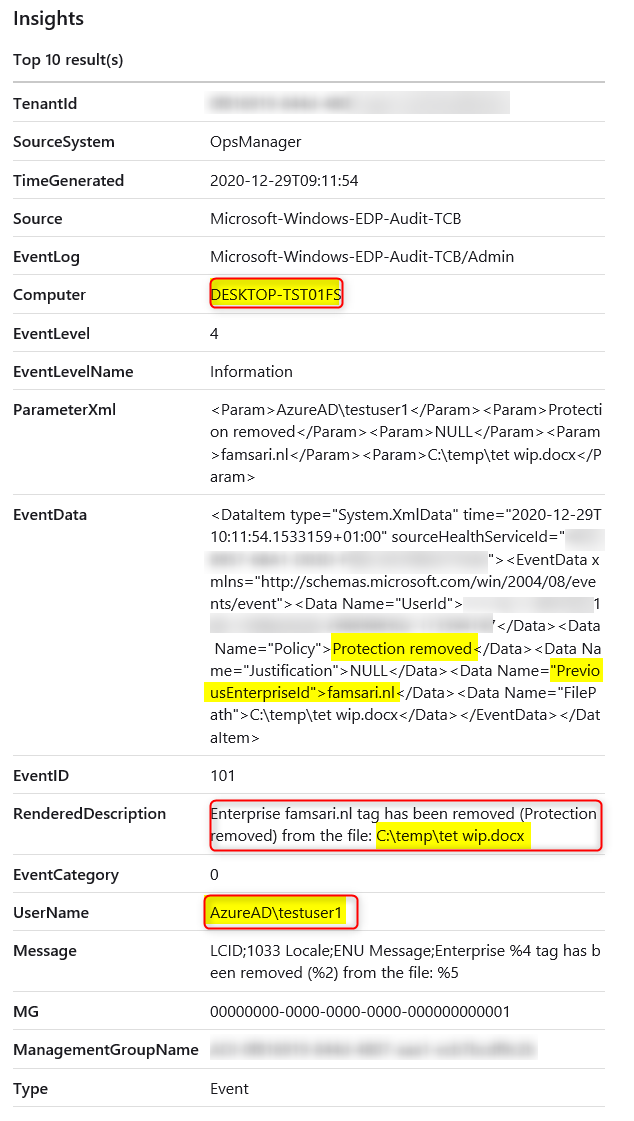
The final log we’ll have a look at is Microsoft-Windows-EDP-Audit-TCB/Admin. This event log audits events where protection has been removed by a user, for example by right clicking on a protected file and using the File ownership menu option to change from Work to Personal.
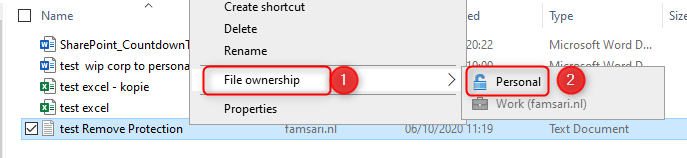
When you check the event in the logs, you’ll see the Enterprise tag has been removed from the file.
So there you have it. These are the 3 event logs you’ll want to monitor. What you don’t want to do is check each and every device you manage manually. That’s just crazy when you have Azure Log Analytics to do the hard work for you.
Searching in Azure Log Analytics logs
Now that the Microsoft Monitoring Agent has been installed to your devices, it starts collecting WIP related information and send that over to Azure Log Analytics for storage and further analysis. You’ve seen how to check the event logs on the device itself but you can do this from a central place for all your devices.
Go to your Azure portal and browse to Log Analytics workspaces. Open the workspace you’ve setup earlier and then click on Logs (1).
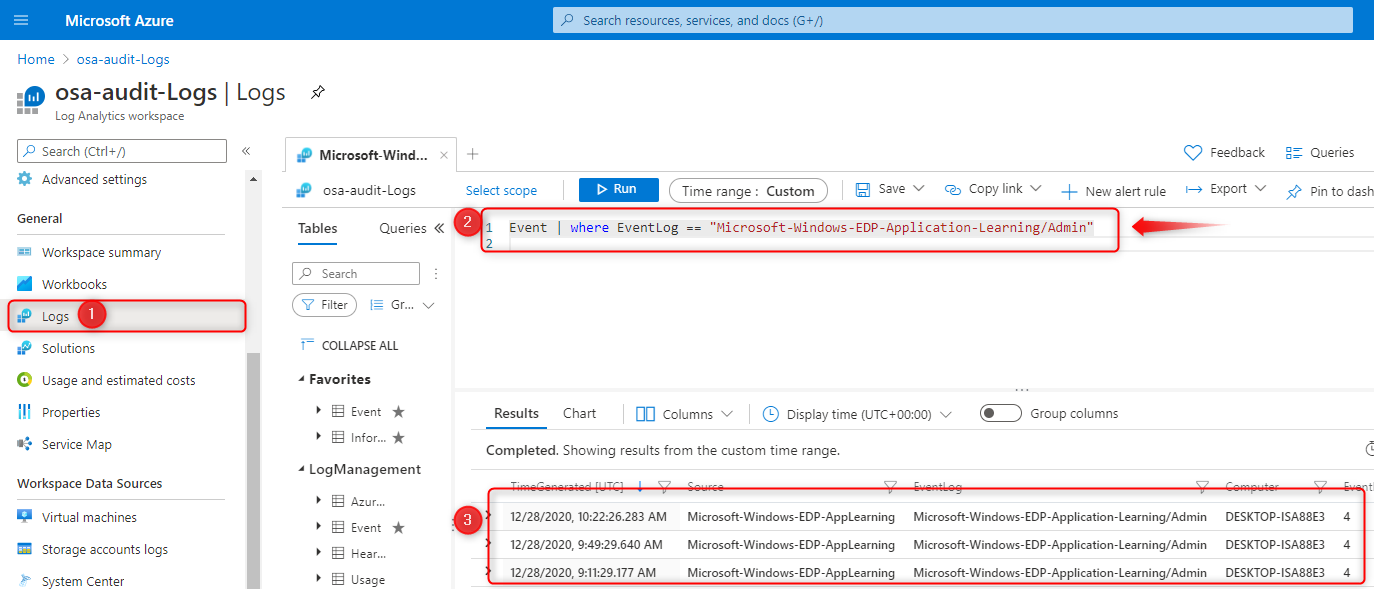
If everything is setup correctly you should be able to run a query (2) like:
Event | where EventLog == "Microsoft-Windows-EDP-Application-Learning/Admin"This will show you all entries written to the event logs of all your devices. The information is formatted differently but contains the same information as on the device itself.
Also try these 2 other queries to see what’s come up;
Event | where EventLog == "Microsoft-Windows-EDP-Audit-TCB/Admin"
Event | where EventLog == "Microsoft-Windows-EDP-Audit-Regular/Admin"Unenlightened apps
I guess it’s a limitation or falls under the category “Works as designed” but when you add an unenlightened app to the allowed app list, nothing is audited for that app or written to the event logs! If you think about it, it works as designed. By adding the app to the allowed app list, you basically tell WIP to trust everything a user does within that app.
These apps will consider all data to be corporate, encrypting everything created or edited by default so think about this before you add unenlightened apps. Microsoft recommends only adding LOB apps to your allowed apps list
I’ve added Firefox as an example and signed-in to Google Gmail. I can now upload an attachment to e-mail or open a PDF file in Firefox without any issues and NO audit trail. I did not see the Override or cancel question! Same is true for Wordpad. If you add it to the allowed app list, a user can open a word document without being audited.
This alone is reason enough for me to only add enlightened apps to the list and to be very cautious when adding unenlightened apps. Just make sure you understand the consequences when you do add unenlightened apps.
The big difference between FireFox (unenlightened) and Edge (enlightened) is that Edge can differentiate between corporate and personal data whereas unenlightened apps like FireFox cannot. So If I was to upload a WIP protected file to Gmail using Edge, I would have to Override the WIP protection policy by clicking on Override:
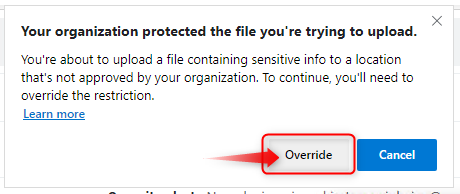
And only then, the protection is removed from the file while at the same time being audited. As you can see below, I have removed protection from a WIP protected file using the Edge browser while transferring enterprise data to mail.google.com.
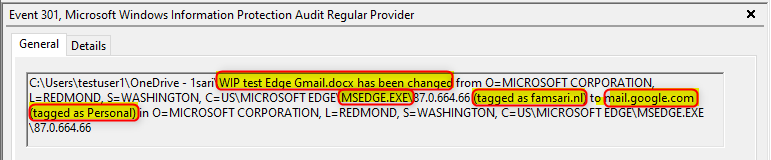
Edge should be the browser for business related work! You can still deploy other browsers, but don’t add them to the approved apps list or set the app entry to deny.
Other limitations or considerations
Let’s have a look at the results when we run the query;
Event | where EventLog == "Microsoft-Windows-EDP-Audit-Regular/Admin"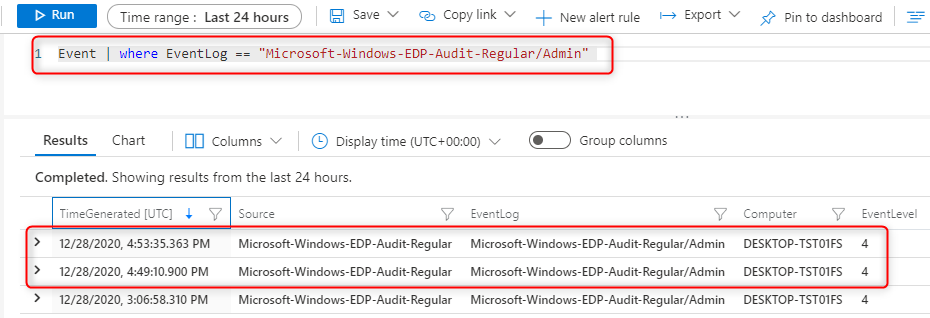
When I open the first result I can see what’s in the event log. I’m interested in 2 columns in particular; EventData and RenderedDescription. The information here is better to understand when you look at the event log on the device itself:
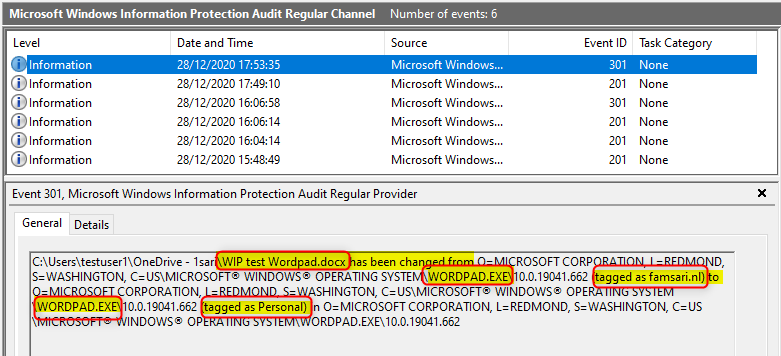
This is normal and to replicate this, you will have to open Wordpad, then in Wordpad go to the Menu File to open a document. Browse to your OneDrive folder and try to open a word document.
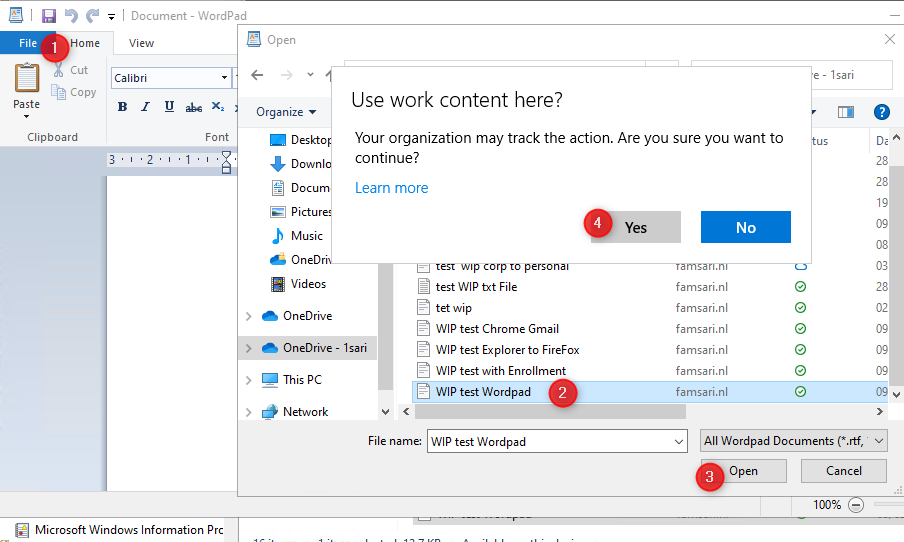
When you click on Yes, the action is audited and written to the event log because Wordpad is NOT on the allowed app list. So Basically you used Wordpad to open a WIP protected file in OneDrive. All good right?
Now when you open explorer and drag the same file from explorer.exe to wordpad, it’s audited but the information is incomplete. Have a look at the information below.
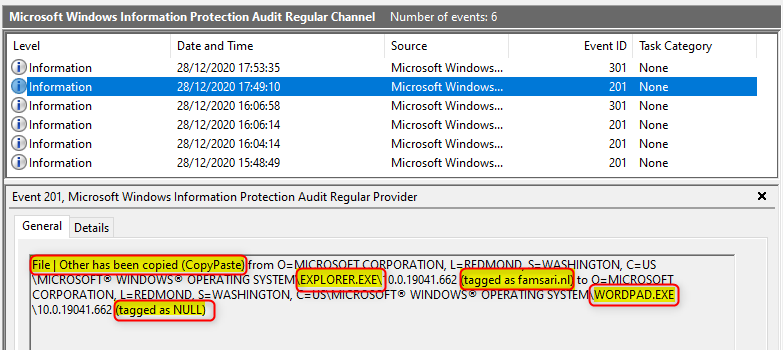
I know explorer.exe has been used to drag a file to wordpad, but I can’t see the actual filename. I can see the file is tagged as corporate when I started this action. After opening (overriding WIP) the file it should also show the protection was removed, but it only shows tagged as NULL.
To make it even more complex, The CopyPaste action from Explorer to Wordpad also writes an event to the Microsoft-Windows-EDP-Application-Learning/Admin log. But opening the document from within Wordpad itself, does not…Why is that?? I guess I have to talk to Microsoft about this and see if there’s a uservoice or not.
Administrators job – What to do with all this?
Azure Log Analytics gives you the option to monitor most of all WIP related logs for all your devices from one single console. It also comes with powerful alert rules for queries so you don’t have to do all the hard work.
For example: You can configure an alert rule to send you an e-mail when WIP protection has been removed from 5 or more files in less then 10 minutes.
If you’re a Kusto Query Rockstar (which I’m not yet….) you can be very specific when creating alert rules for your queries. Please share your queries if you feel they can add value.
Here’s an example email from an alert rule I created for testing purposes:
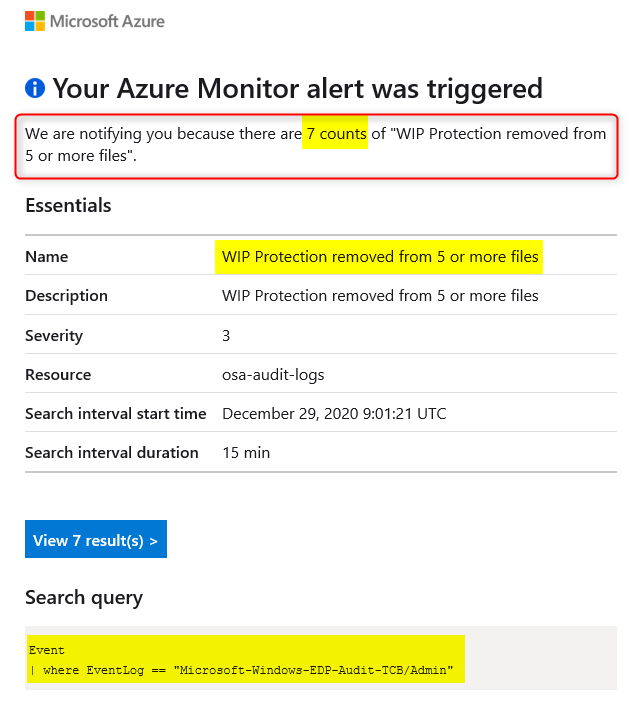
I hope this post was helpful. If you have any feedback or comments, please let me know below. I’m trying to answer every question I receive here on my blog, but realize I’m sometimes fashionably late. Sorry for that. It’s good to see others jump in when I’m late responding.
We help each other, that’s what we do and I have the utmost respect for everyone who jumps in. So thank you all!
I guess this will be my last post for 2020. Happy holidays, dear friends. May 2021 be kind to all of us!
Links and further reading
- How to collect Windows Information Protection (WIP) audit event logs
- Overview of Azure Monitor agents
- Azure Monitor agent overview (preview)
- Log Analytics agent overview
- Create a Log Analytics workspace in the Azure portal
- Install Log Analytics agent on Windows computers
- Overview of log queries in Azure Monitor
- Logging and analyzing the protection usage from Azure Information Protection
- Central reporting for Azure Information Protection (public preview)
Great article friend!
It’s really informative with rich points. I got many new ideas and important points from your article and it seems to be very useful for me 🙂
Thank you Sari and expecting many similar articles in the future.
Thank you!
[…] Sari wrote a good post on that matter, so I’ll skip the deep […]