Last Updated on December 31, 2023 by Oktay Sari
July 2022
IMPORTANT UPDATE: Microsoft announced the sunset for Windows Information Protection! WIP will be discontinued over time. Support for Windows Information Protection Without Enrollment will end by the end of calendar year 2022. Please read the official announcement and more on the following 2 sites:
- Announcing the sunset of Windows Information Protection (WIP)
- Support tip: End of support guidance for Windows Information Protection
If you have plans to implement WIP, I suggest you rethink your strategy accordingly. I will follow-up on this and update the WIP posts I have when more information is released by Microsoft.
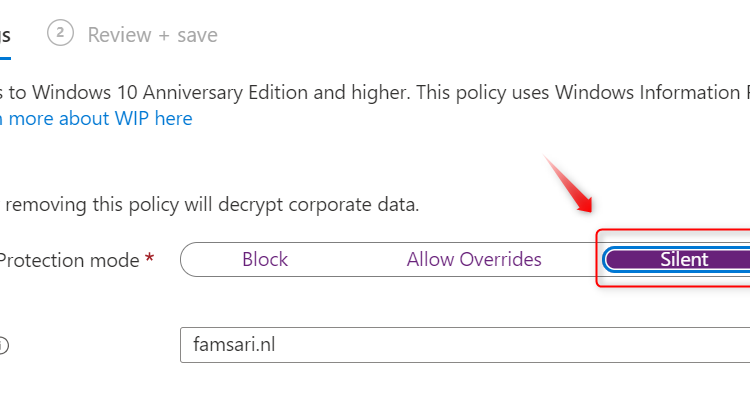
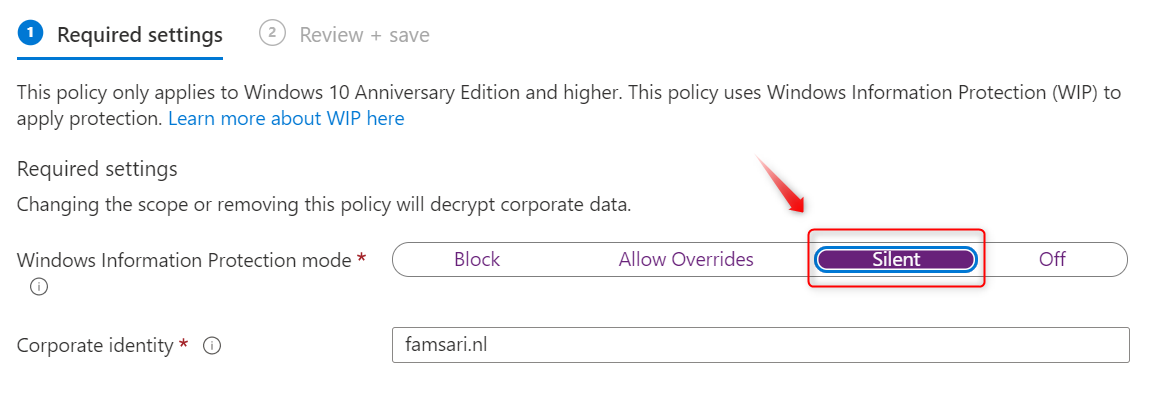
When you first start with Windows Information Protection (WIP), you might want to consider starting with the Protection Mode set to Silent. This is also called Windows Information Protection Learning Mode or WIP Learning Mode.
In silent/learning mode WIP runs silently and will not block anything. It will however encrypt and log all actions including inappropriate data sharing to the event-log, giving you the opportunity to monitor your WIP implementation and possible impact, before going to production. WIP Learning mode essentially monitors all applications that access corporate data. When I read back this series on WIP, I realize this post, should actually be one of the first post. This feature is underappreciated while it can save you a lot of time and frustration.
As always, I ask you to also check the official Microsoft documentation as they are very complete and probably will update their documentation more frequently. This post is part of a series and in upcoming post I’ll also write about limiting Access to Exchange Online or Sharepoint from unmanaged devices.
- Introduction to Windows Information Protection
- Configuring MDM user scope and MAM user scope
- WIP-WE / MAM – Windows Information Protection without enrollment
- Windows Information Protection with Enrollment
- Windows Information Protection User Experience
- WIP-WE User Experience – WIP Without MDM enrollment
- Set up Azure Rights Management for WIP
- WIP Without Enrollment Selective Wipe
- Troubleshooting Windows Information Protection
- Monitoring and collecting WIP audit event logs
- WIP Learning Mode (this post)
- Support Windows 10 BYOD with Microsoft Endpoint Manager and WIP-WE
Prerequisites
- Intune MDM enrolled Windows 10 devices
- Intune licenced users
- an existing or a new Log Analytics workspace*
- The Microsoft Monitoring agent installed on MDM enrolled Windows 10 devices*
- Be sure to check the network requirements
* These are not actual prerequisites for WIP learning Mode or needed for WIP to function.
WIP Learning Mode Limitations
Windows Information Protection Learning Mode also has its limitations. You’ll need Windows 10 devices that are MDM enrolled with Intune because deploying software to Windows 10 using Intune, can only be done on devices that are MDM enrolled. The Microsoft Monitoring Agent collects the event logs from client devices and sends them over to Azure Log Analytics. Furthermore, the default reporting options are very limited.
Azure Log Analytics and the Microsoft Monitoring Agent
By default you have some reporting functionality from the Endpoint Manager portal but they are very limited. That is why we’ll be using Log Analytics for monitoring. Use an existing Workspace or create a new Log Analytics Workspace. I’m assuming you know how to set up Log Analytics. If not, check out the Microsoft documentation here. I’ve also explained how to deploy the Microsoft Monitoring Agent and how to get started in my previous post about Monitoring and Collecting WIP Event logs. Go ahead and read that first and come back here when you’re ready.
WIP Learning mode reports
Starting right off the bat with your WIP Protection mode set to “Allow overrides” or “Block” sounds like a plan, but if you have no clue what apps your users are working with you’ll probably want to start with the WIP protection Mode set to “Silent” As mentioned above, you can find two reports in the Endpoint Manager (MEM) Portal; The App learning report and the Website learning report.
App learning report
The App learning report gives information about apps that are not included in your policy and try to access WIP protected corporate data.
- Go to your MEM portal at https://endpoint.microsoft.com
- Click on Apps > App protection status > Reports
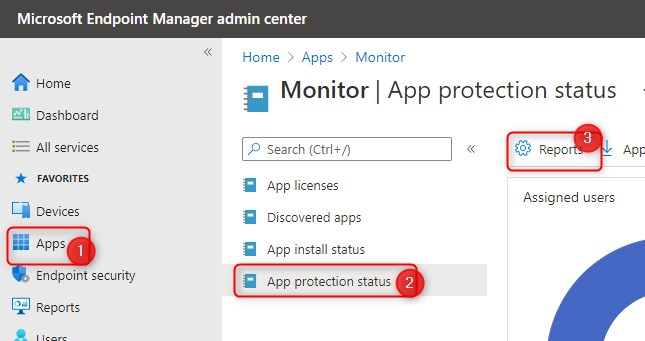
Click on App Learning report for Windows Information Protection on the left to see the App Learning report. The report includes apps that I did not configure with my WIP policy. In this same menu, you can also click on Website learning report for Windows Information Protection. For example, you can see that Adobe Acrobat Reader DC, Dropbox, Chrome and Notepad++ have been used by users to access WIP protected data.

On top of this page you can still find a link to the deprecated/rebranded OMS portal. The link actually takes you to the Desktop Analytics documentation. This might be confusing (it was for me) because for Desktop Analytics you still need Configuration Manager. Check out the FAQ and the first Question. It doesn’t quite work with Intune yet…
Q: “Can I use cloud-enabled analytics with Intune-managed devices?”
A: “Not today, but….”
If you do happen to have Configuration Manager, than you can use the WIP section in Device Health. It highlights any Windows Information Protection misconfigurations. Some background info: Windows Analytics retired on January 31, 2020 in favor of Desktop Analytics. From this date on, new customers are no longer able to onboard to the Upgrade Readiness and Device Health solutions in Azure. However, Update Compliance is still available via the Azure portal.
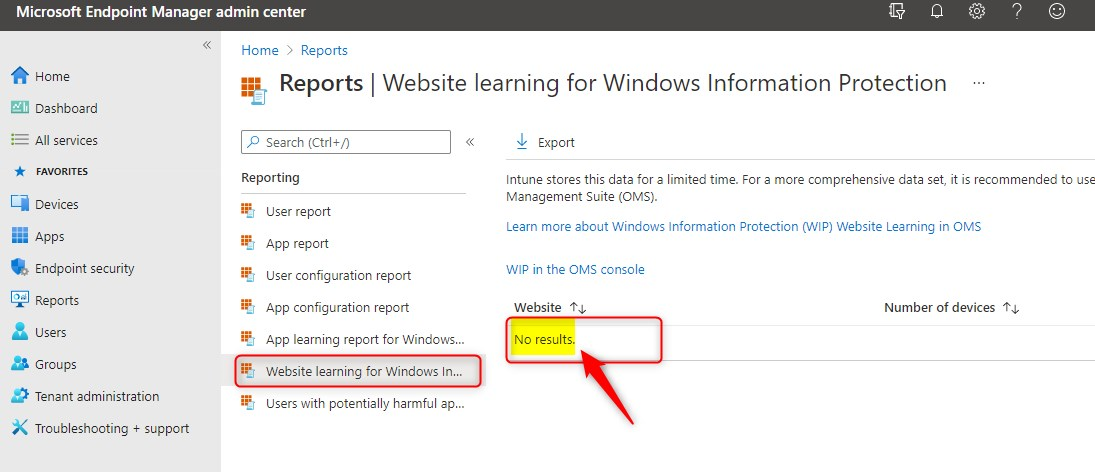
Website learning report
There’s also a website learning report. The Microsoft documentation tells you that you can view a summary of devices that have shared work data with websites. It should show which websites are accessed by WIP-enabled apps. But I have never been able to produce any reporting here. If you did manage to get some info here, please share it below in the comments. I tried with a tenant or 5 and it always shows No results. Yet another reason to go with Log Analytics.
Log Analytics
As you can see, the default reporting options in MEM do not give a lot of information but it can get you going on without any additional configuration. If you do want more information, you’ll have to use Log Analytics. Read my previous blog Monitoring and Collecting WIP Event logs If you want to learn more about the setup.
There are 2 logs to monitor for apps that access enterprise resources:
- Microsoft-Windows-EDP-Application-Learning/Admin
- Microsoft-Windows-EDP-Audit-Regular/Admin
Microsoft-Windows-EDP-Application-Learning/Admin
They Microsoft-Windows-EDP-Audit-Regular/Admin log shows any application that tries to access WIP protected corporate data. It shows the date and time, the application name and also the Computer Name and other info.

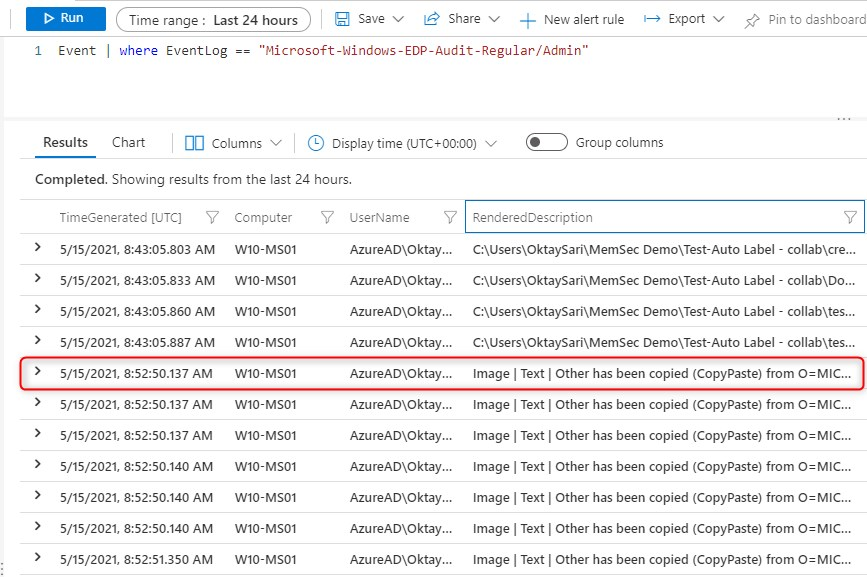
Microsoft-Windows-EDP-Audit-Regular/Admin
The Microsoft-Windows-EDP-Audit-Regular/Admin log shows even more information. Here you’ll see what actually happened with your WIP protected data. For example this report shows data is copy/pasted to google translate!
has been changed from O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US\MICROSOFT OFFICE\WINWORD.EXE\16.0.13929.20296 (tagged as memsec.nl) to translate.google.com (tagged as Personal) in O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US\MICROSOFT EDGE\MSEDGE.EXE\90.0.818.62
Or how about the example below. This shows a test document is uploaded to box.com using the Edge browser.
OneDrive – MemSec Demo\Documents\Testdoc Memsec – No Label – Copy.docx has been changed from O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US\MICROSOFT EDGE\MSEDGE.EXE\90.0.818.62 (tagged as memsec.nl) to app.box.com (tagged as Personal) in O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US\MICROSOFT EDGE\MSEDGE.EXE\90.0.818.62
Fine-tune Windows Information Protection
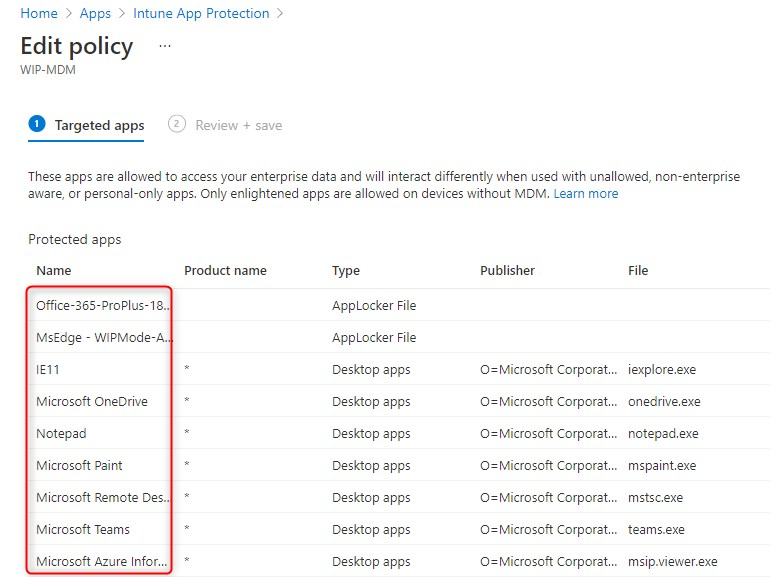
After setting up Windows Information Protection Learning mode, you’ll want to pilot this for a week or so and perhaps even longer. Then analyze the information in Log Analytics. As a result you will have a better idea of what users do with corporate data and what apps or websites they use. And you’ll also be able to fine-tune which apps and websites to include in your WIP policy to help reduce disruptive prompts for your users.
Have a look at my previous post about how to create a WIP policy and add apps to your policy.
WIP Learning Mode Follow up
When you feel you are ready, go ahead and switch the flip to “Allow override” or “Block”. But keep monitoring your Log Analytics to see if anything needs further fine-tuning. The “Windows Information Protection learning mode” post was the last one in the series on WIP. There are 2 post coming up about limiting Access to SharePoint Online and Exchange online. I feel that combining WIP and limited access from unmanaged devices, gives you the best of both worlds. I truly hope these posts have helped you get going. Please share any ideas or feedback you have.