Last Updated on December 31, 2023 by Oktay Sari
July 2022
IMPORTANT UPDATE: Microsoft announced the sunset for Windows Information Protection! WIP will be discontinued over time. Support for Windows Information Protection Without Enrollment will end by the end of calendar year 2022. Please read the official announcement and more on the following 2 sites:
- Announcing the sunset of Windows Information Protection (WIP)
- Support tip: End of support guidance for Windows Information Protection
If you have plans to implement WIP, I suggest you rethink your strategy accordingly. I will follow-up on this and update the WIP posts I have when more information is released by Microsoft.
In my previous post I’ve walked through the WIP-WE user experience (Windows Information Protection without enrollment) and showed you what the users experience when working on a Windows 10, BYOD (Bring Your Own Device). In the first part this post I’ll show you what happens to corporate data when an administrator performs a selective wipe on a personally owned BYOD (WIP Without Enrollment Selective Wipe). The second part, I’ll show you what happens when the user disconnects a device by removing his or her work account. Finally, I’ll finish this post by looking at Microsoft Office Outlook offline data files (OST files) and WIP limitations.
This post is part of a series. Have a look at my other posts for more information about WIP.
- Introduction to Windows Information Protection
- Configuring MDM user scope and MAM user scope
- WIP-WE / MAM – Windows Information Protection without enrollment
- Windows Information Protection with Enrollment
- Windows Information Protection User Experience
- WIP-WE User Experience – WIP Without MDM enrollment
- Set up Azure Rights Management for WIP
- WIP Without Enrollment Selective Wipe (this post)
- Troubleshooting Windows Information Protection
- Monitoring and collecting WIP audit event logs
- WIP Learning mode
- Support Windows 10 BYOD with Microsoft Endpoint Manager and WIP-WE
Prerequisites
Make sure you have a test configuration up and running and make sure you have the prerequisites in place;
- Intune enabled as the MDM authority
- Windows 10 1703 and above (Pro, Enterprise, Education)
- EMS E3 licenses (or at the very least Intune and Azure AD premium P1)
- Configure your MAM provider in Azure AD for WIP without enrollment
- Azure AD registered Windows 10 device
- Set WIP Protection mode to Block
- Set Revoke encryption keys on unenroll to On
Note: By revoking the encryption keys, access to encrypted files is blocked and therefore a user no longer has access to encrypted (WIP protected) corporate data.
Check settings Accounts Access work or school and make sure your device is registered with Azure AD by adding a Work or school account. Have a look at Azure AD registration in my previous post for more on that.
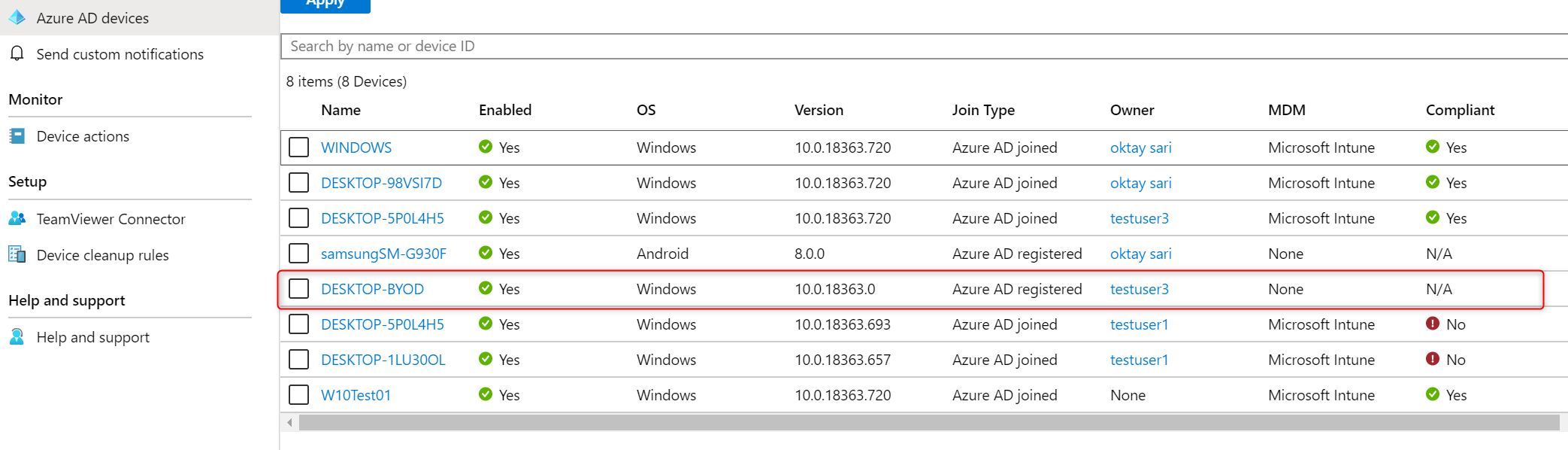
You can confirm this from the back-end by checking Azure AD devices. My test user is working on a Windows 10 device with the name DESKTOP-BYOD. Azure AD registered and not managed by MDM.
For now, I’ll have to assume everything is in place to get started with an actual WIP Without Enrollment Selective Wipe from the management portal.
Before the selective wipe
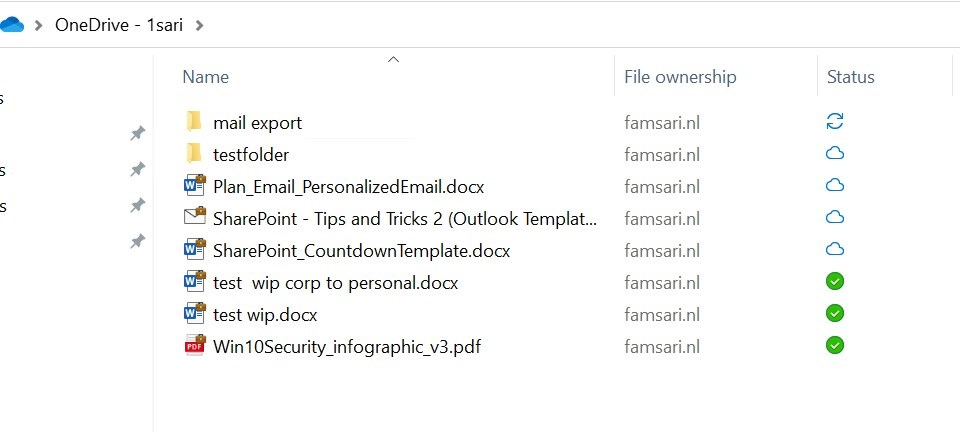
Now before you go ahead and start a Selective Wipe, have a quick look at your test device and make sure you have OneDrive for Business configured and you actually sync data to your device. I also have configured Outlook with e-mail data available. Otherwise there is no data to wipe ?
Is your corporate data protected with WIP? You can check the File ownership for a clue.
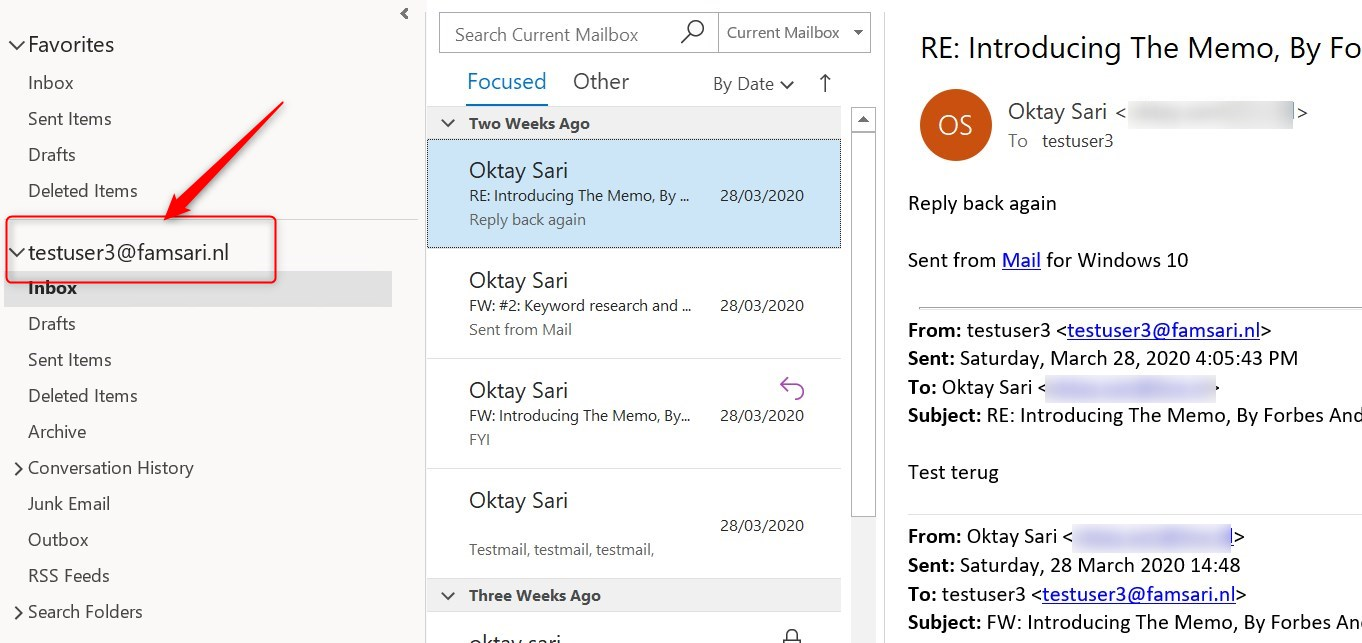
Office 365 Outlook is configured with a corporate e-mail profile
Part 1: Admin triggered selective wipe
To remove only organizational data from a device, an administrator can start a WIP Without Enrollment Selective Wipe on a Windows 10 device. Start by going to Microsoft Intune > Client apps > App selective wipe. You can also do this from the new management portal. It’s basically the same, but the menu looks a little different. For now I’m using portal.azure.com and go to Microsoft Intune.
- Go to Microsoft Intune >Client apps > App selective wipe
- Click + Create wipe request
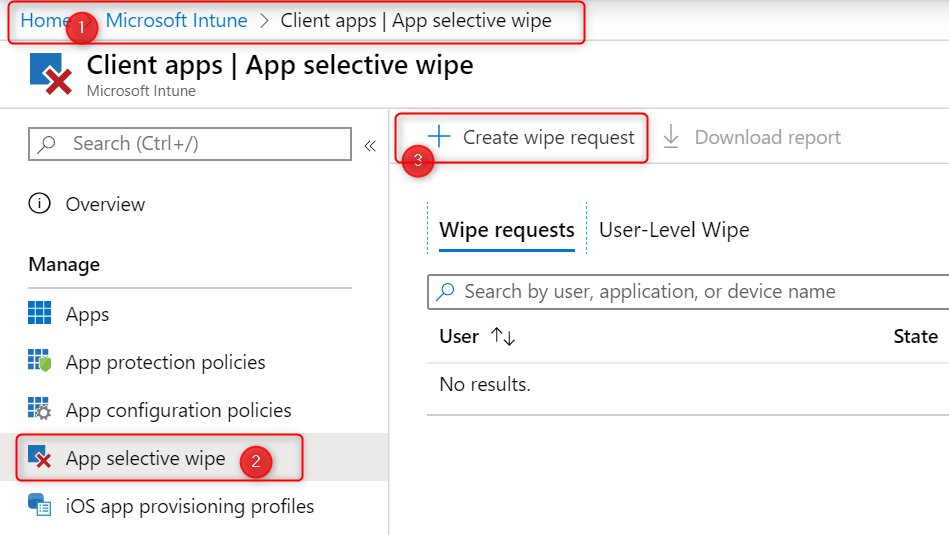
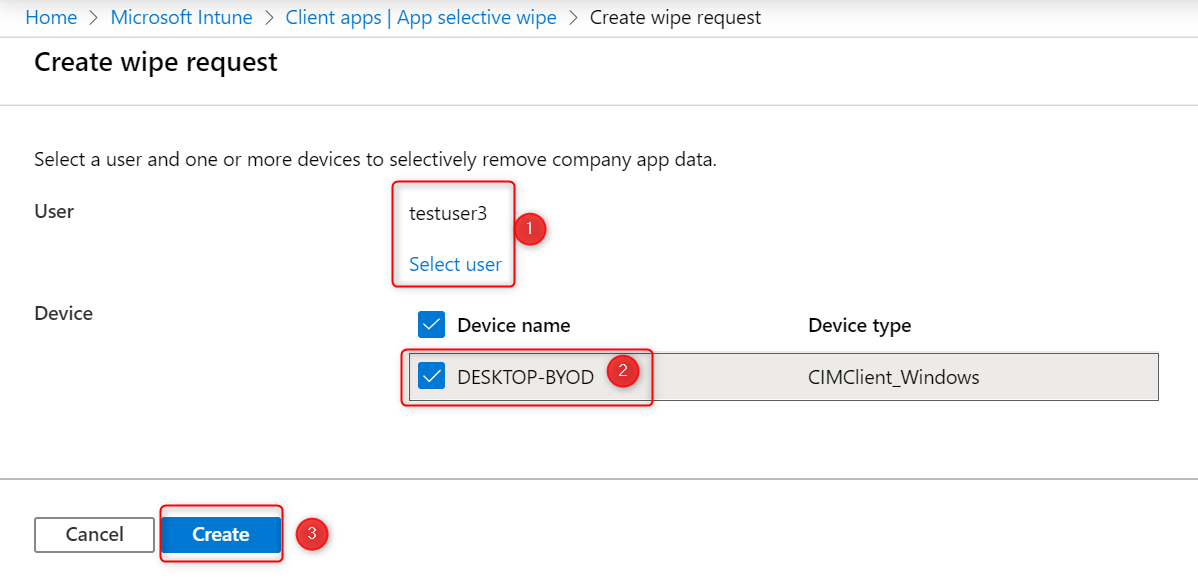
- Click select user. When you’ve selected a user, Intune will show any Windows 10 devices that are Azure AD registered.
- Choose a device on which you want to perform a selective wipe.
- Click on Create
When you are ready, the WIP-WE Selective Wipe request will show as pending. There is a report that shows the overall status of the wipe requests you have executed.
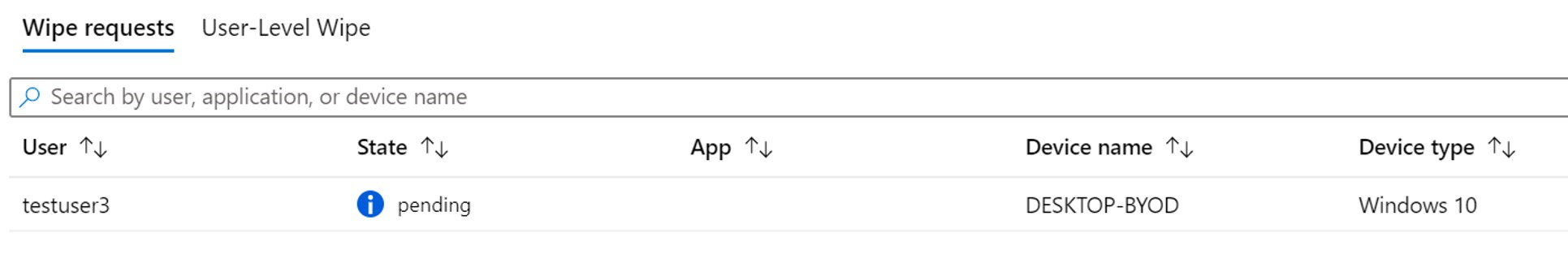
That’s all there is to it. The selective wipe request is created.
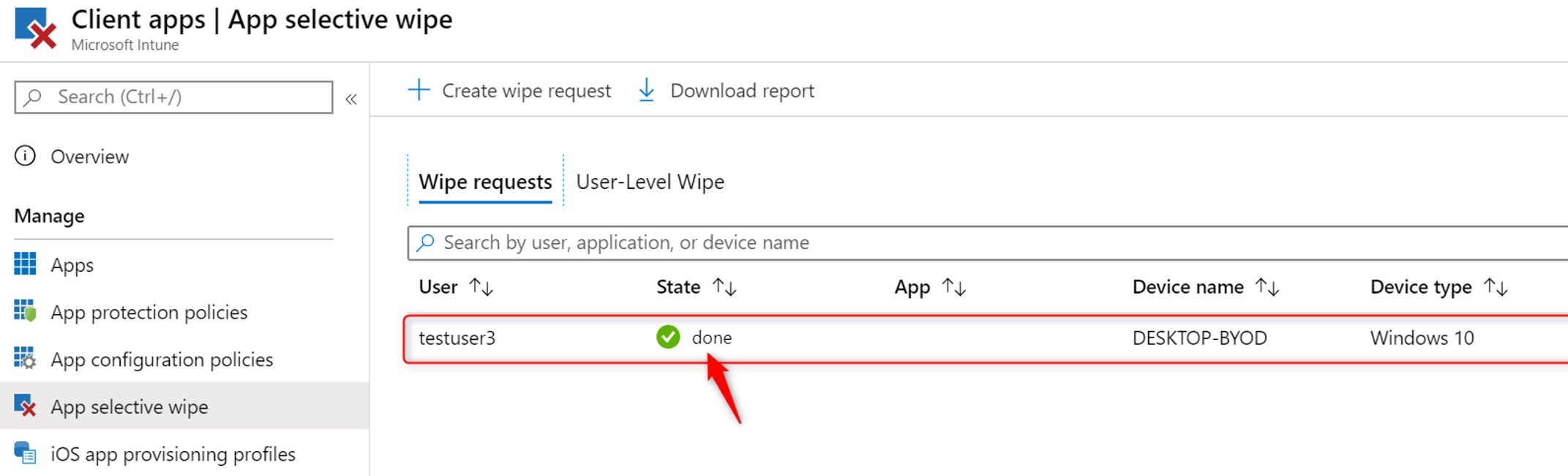
When the device has synced with Intune, it will start to revoke the encryption key and effectively block access. The report now shows the status of the wipe request has changed from pending to done.
User Experience after a admin triggered selective wipe
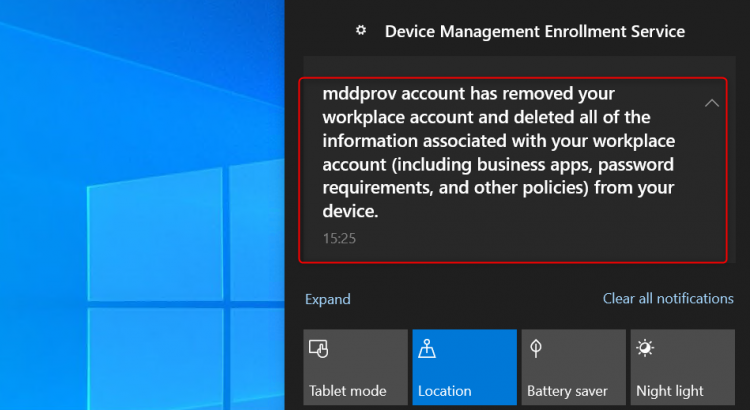
The very first thing that happens when the wipe request is received by a device, is a notification from the Device Management Enrollment Service. It tells you that the workplace account has been removed.
You did set the WIP configuration setting Revoke encryption keys on unenroll to On right? This is where the encryption key is revoked!
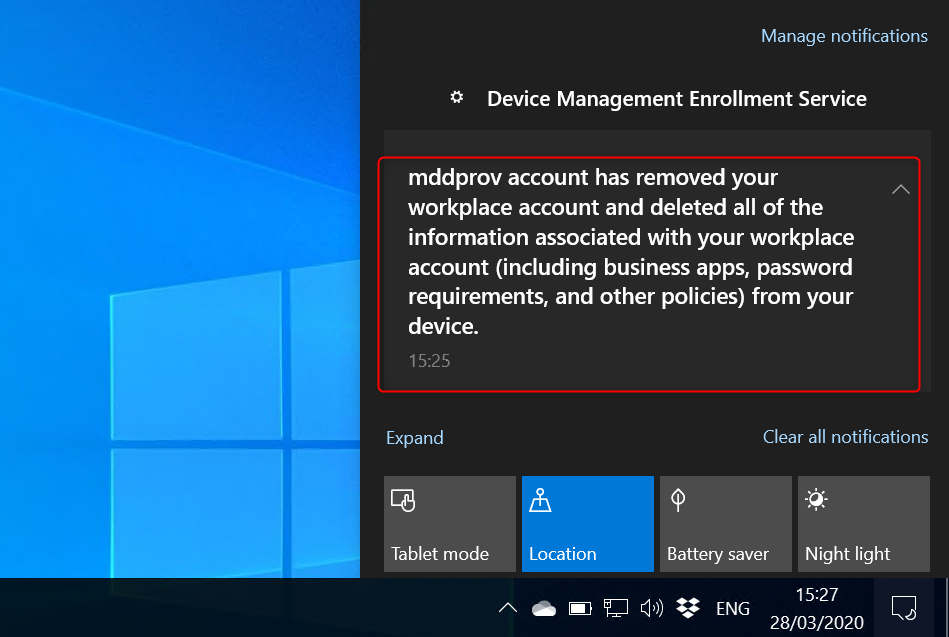
OneDrive for Business after a selective wipe
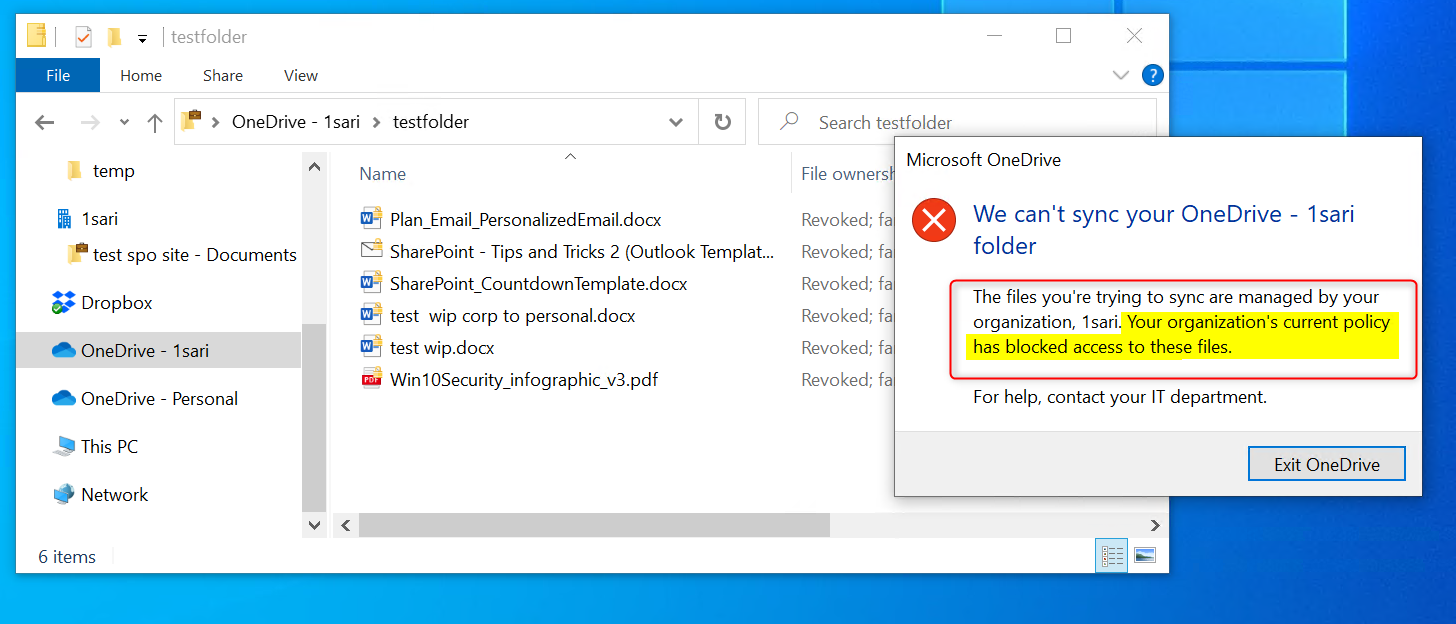
If OneDrive for Business or Outlook are open, they will close automatically. It’s not the best user experience since the apps basically crash. The second thing the user sees is an error message from Microsoft OneDrive. OneDrive for Business can’t sync data because the encryption key has been revoked.
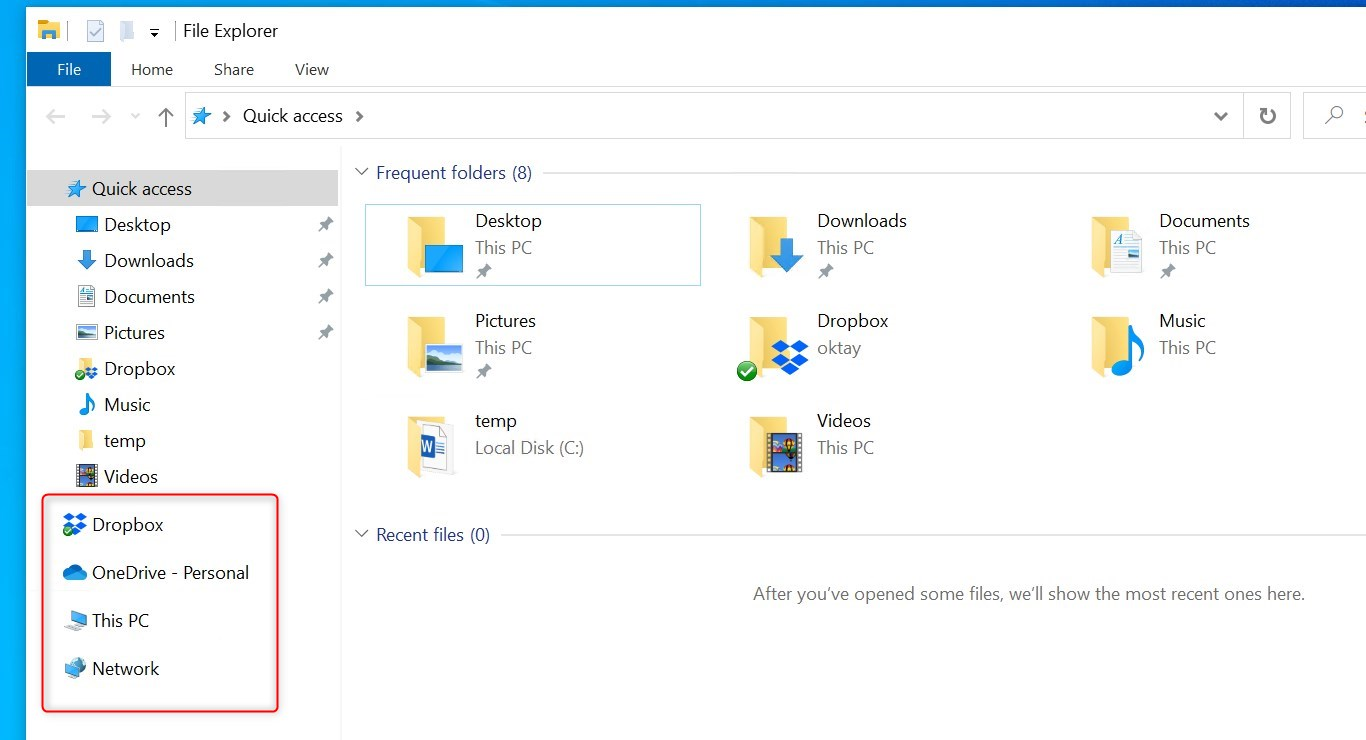
When the user opens Explorer, OneDrive for Business is no longer available. WIP Without Enrollment Selective Wipe seems to do the job right?
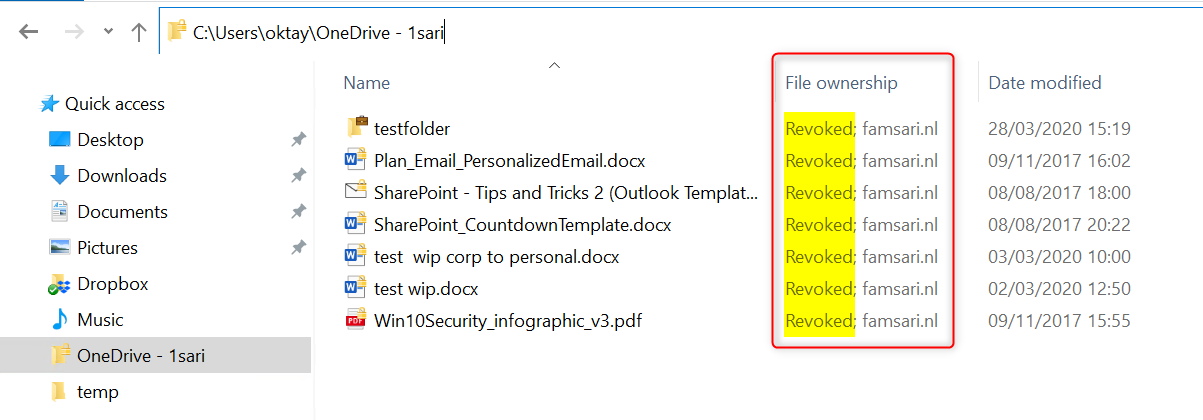
Note: The selective wipe process doesn’t actually remove locally stored corporate data! It only revokes the encryption keys. That in turn effectively removes access to locally stored corporate data.
If the user does stumble across locally stored corporate data, the “File ownership” column shows Revoked;domain-name . This tells us that the encryption key has been revoked.
When opening a corporate document, an error message shows the user doesn’t have access privileges to open corporate documents.
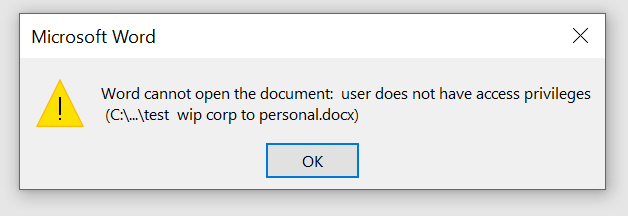
Microsoft Office Outlook after a selective wipe
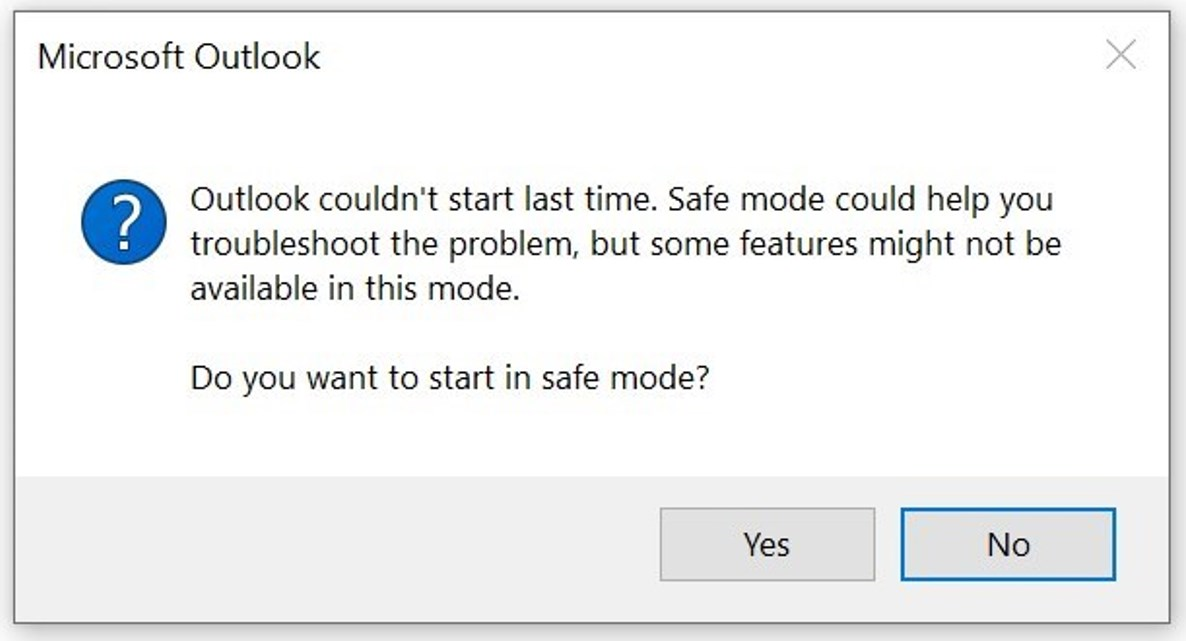
Upon starting Outlook, two things can happen:
- If there is a personal e-mail account configured, Outlook will start but you’ll have to start in Safe Mode to begin. In most cases you’ll have to re-configure another e-mail profile for your private e-mail. This seems like a buggy thing. You will also see that corporate e-mail has been removed after Outlook starts again.
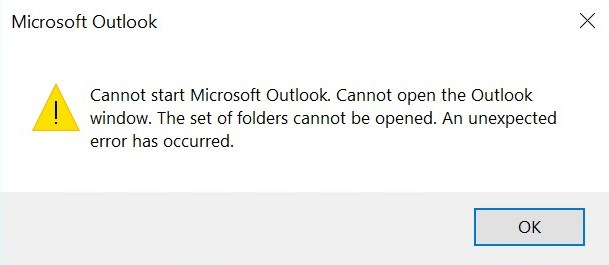
- When only a corporate e-mail profile is configured, the first time you start Outlook you’ll have to re-configure another e-mail profile. Either way, the user is confronted with error messages:
When you only have a corporate e-mail profile, you’ll see the this warning only:
When you also have configured a personal email account like outlook.com, you’ll also see the next error message too:
Part 2: User disconnects Azure AD registered device
When you no longer need to use your device for work, you can unregister or disconnect your device from Azure AD. Go to Settings > Accounts > Access Work or School. Select your account and click Disconnect.
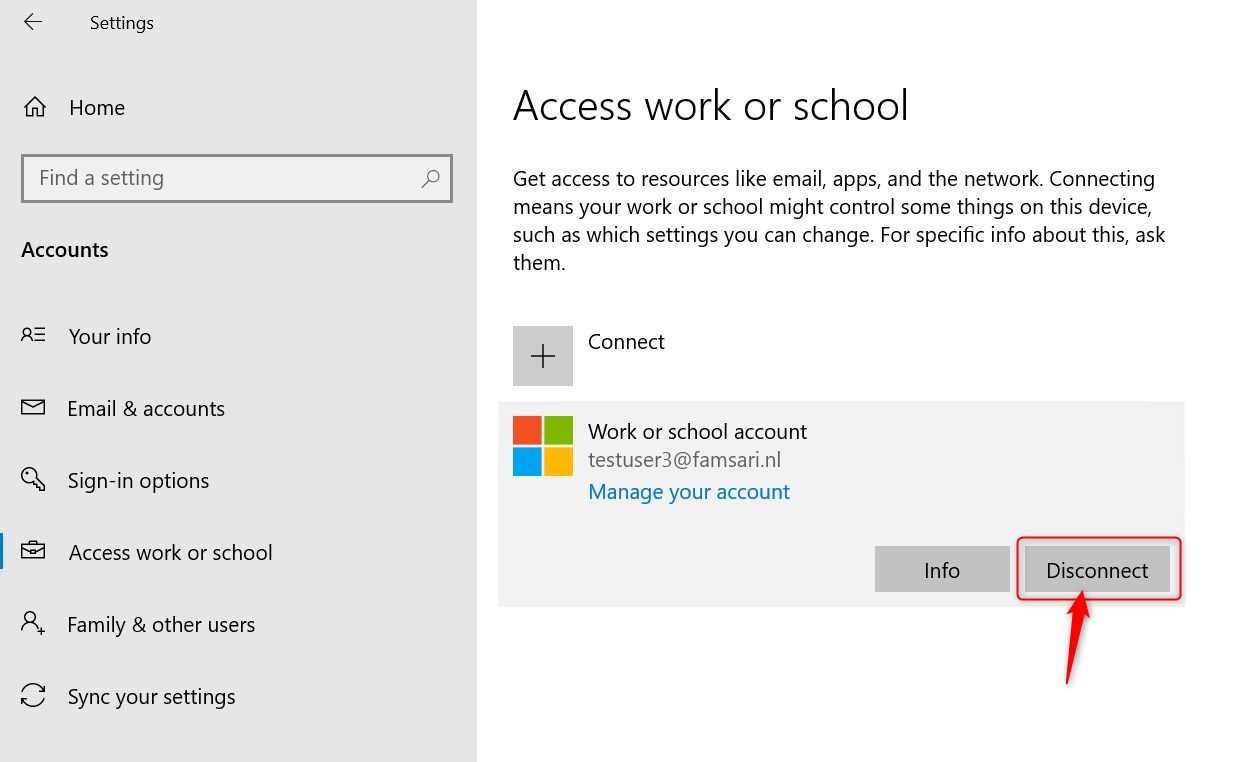
The next screen shows a warning. Disconnecting your device will remove access to work resources. Remember, this doesn’t actually remove locally stored corporate data.
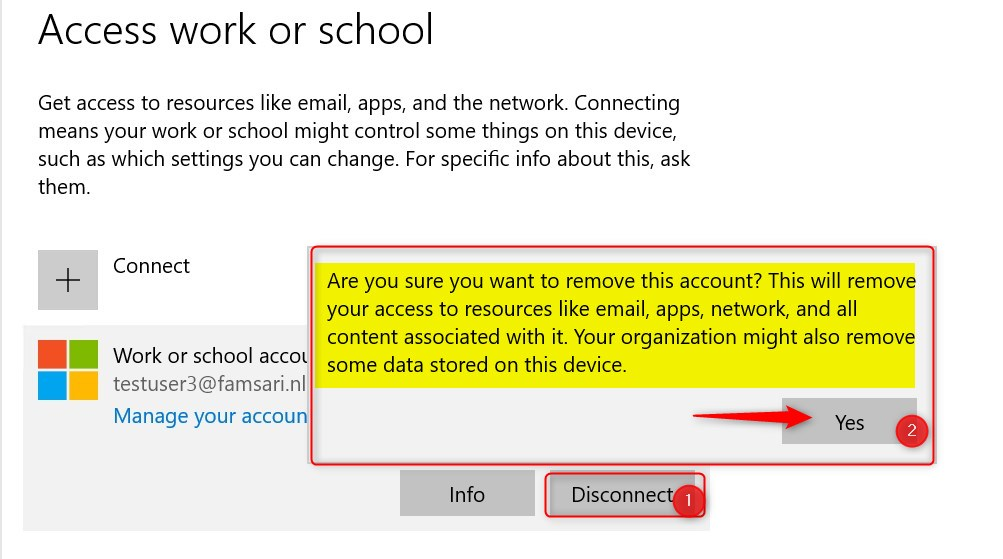
When you click Yes on this screen, the device will no longer be Azure AD registered. In most cases user experience will be affected almost immediately. From here on, the experience is the same as described above for both OneDrive for Business and Microsoft Outlook.
Part 3: Microsoft Outlook offline data files and WIP
There is an issue you need to be aware of when it comes to Outlook offline data files (emailprofile-name.ost) and Windows Information Protection (WIP). In particular with WIP-WE (MAM) and Bring Your Own Devices that are only Azure AD registered.
By default, Microsoft Office Outlook offline data files are NOT marked as Work files, and are therefore not protected by WIP.
Read that previous sentence again and then, have a look at: C:\Users\[username]\AppData\Local\Microsoft\Outlook\
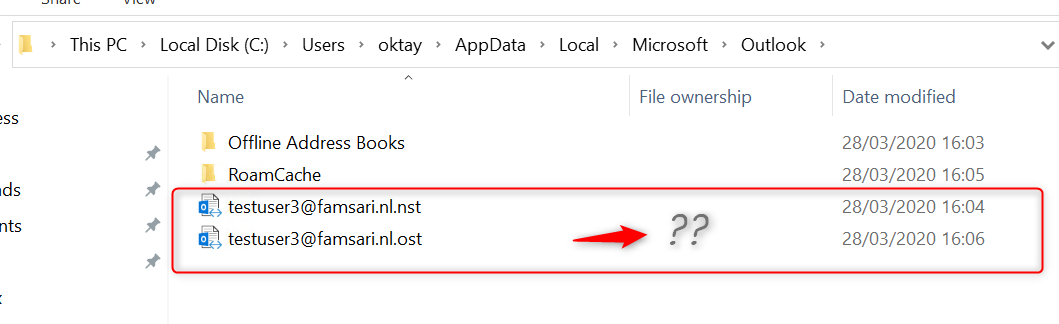
Microsoft recommends to use Microsoft Office Outlook profile in Online mode, or to use encryption to protect OST files manually. However, encryption is not something you can centrally manage very easily on Azure AD registered devices that are not managed by MDM.
A device that is Azure AD registered has only been registered in Azure AD. This registration gives you no meaningful controls over the device. You cannot push configuration profiles or enforce device based conditional access policies on devices that are only Azure AD registered. Your users would have to MDM enroll their devices for that to work.
What happens to OST files upon selective wipe?
When you execute a selective wipe, the OST file is untouched until you restart Outlook. When you restart Outlook or create another Outlook mail profile, the OST file is deleted automatically. Most users will not think of copying or moving the OST file after a selective wipe and before starting Outlook, but it does give a window of opportunity for a data breach. And yes, you can copy the OST file before a selective wipe is executed.
What can I do with OST files, once I copied or moved them?
Normally you could open the OST file with special software and convert it to a PST file. After that, You can open the PST file in Outlook and do anything you want with the data.
Of course, I tried to open the corporate OST file with various OST readers and OST to PST converters but was not able to read anything except folder-name structures. I’m no encryption specialist but everything is just scrambled and unreadable. Most OST viewers give an error indication the file is corrupt or encrypted.
So is there a form of encryption in place? Please tell me if you know something about this in the comments below.
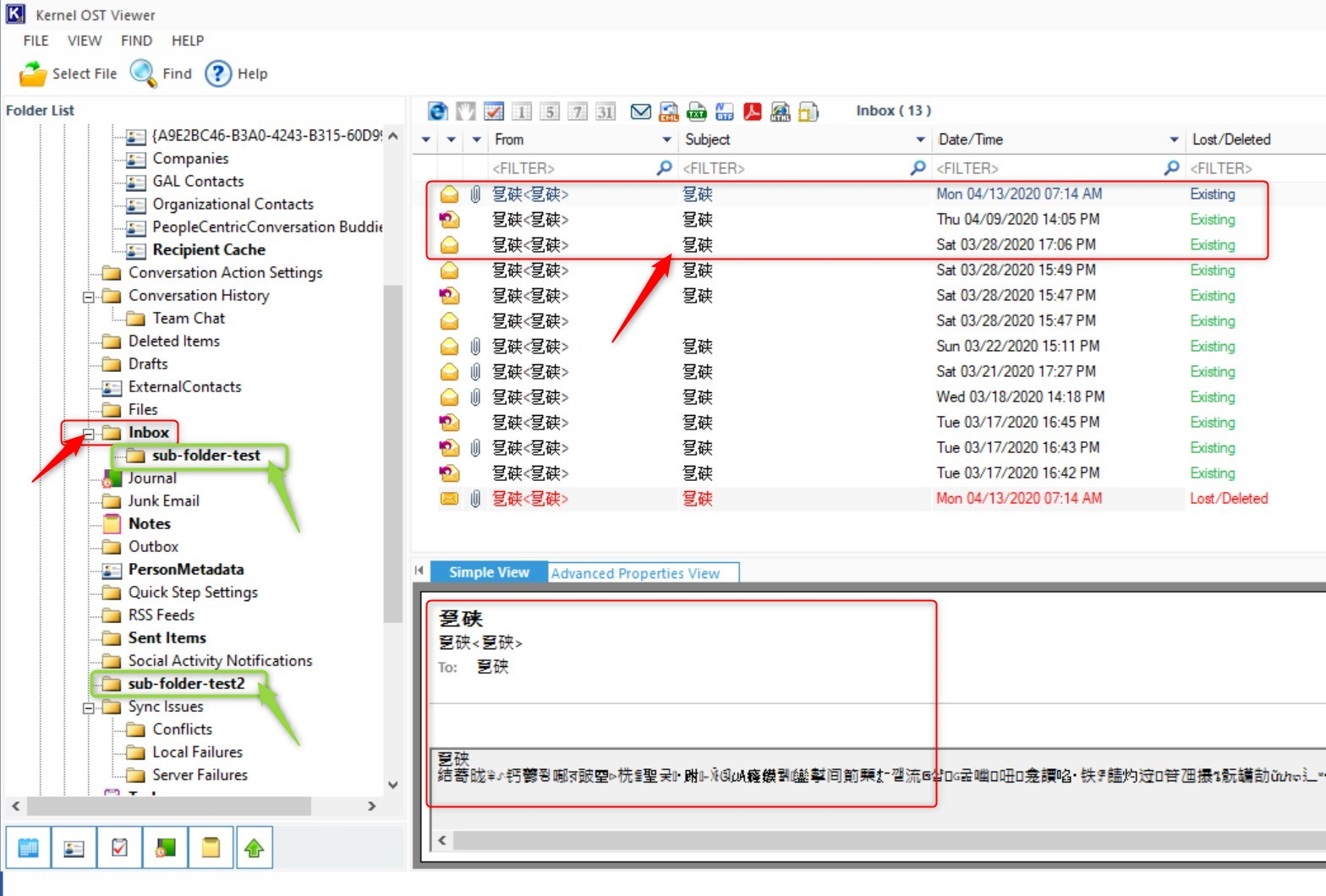
Just to be sure, I copied another OST file from my personal e-mail profile on the same device and same Outlook configuration. This time, I’m able to read everything and can even convert the file to PST.
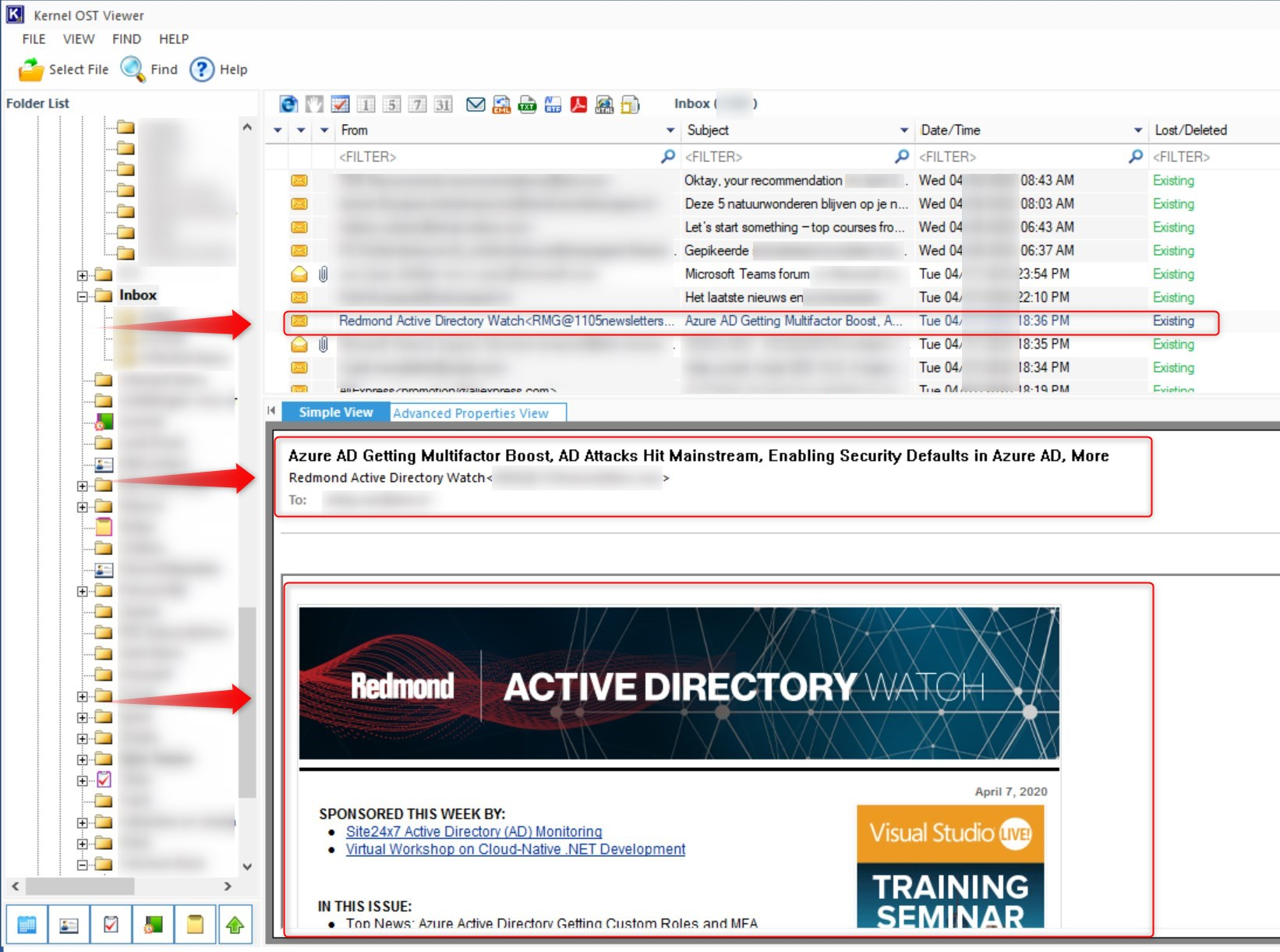
My personal thoughts on this OST issue
I find it strange that it’s not possible to work protect OST files. Hope someone can shed a lite on this anytime soon. Especially because other Outlook files seem to be protected by WIP. For example, when I export my mailbox to a PST file, by default it’s protected by WIP. I’m not able to safe it without WIP protection, no matter where I try to safe it.
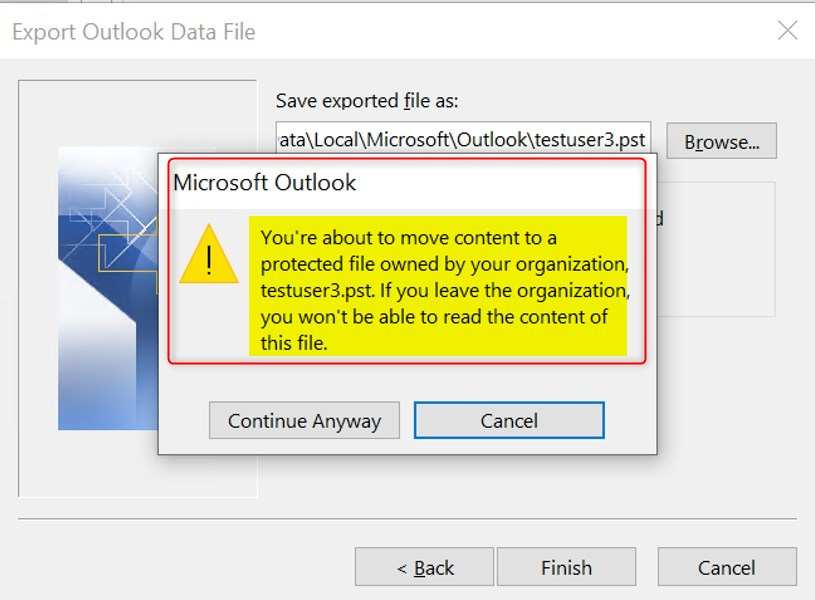
Outlook even warns about moving content to a protected file owned by my company, and I won’t be able to read the content when I leave the company. The PST file has the File ownership set to my protected domain.
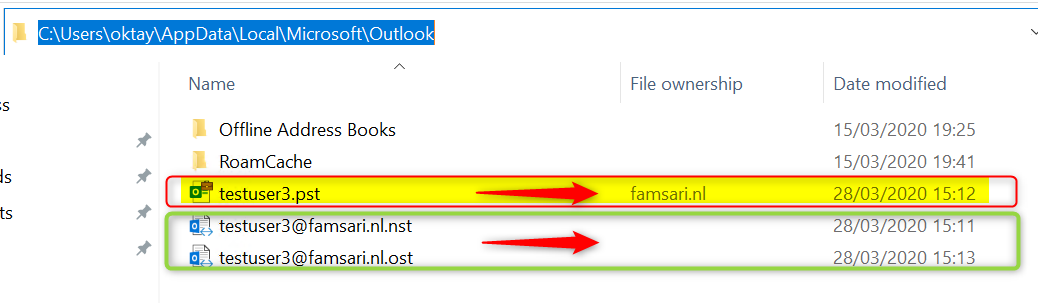
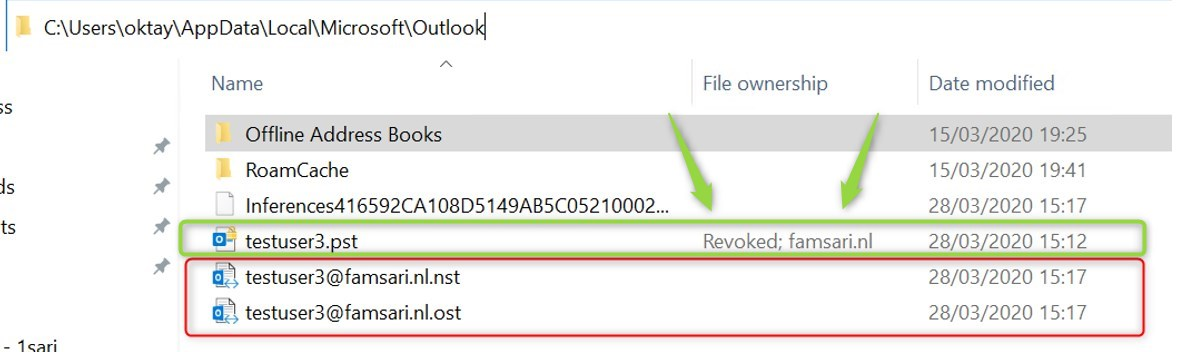
When you execute a selective wipe, the encryption key is revoked again and you can’t access the file anymore.
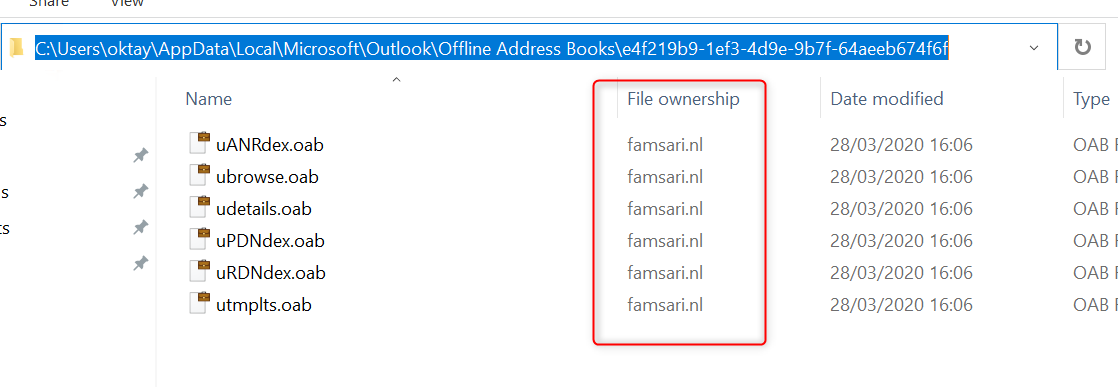
To make it even stranger, I found that Offline Address Books are WIP protected by default. How does that work?
So why is it not possible to WIP protect OST files? I not so satisfied with Microsoft’s answer by putting it on the WIP limitations list. It seems to me, that it’s possible. I do believe that Microsoft continues to perfect Microsoft Intune and that this will be solved sometime in the future. Until then, we will have to work around this limitation.
What can you do?
I guess a best practice would be to go for Outlook on the Web combined with Conditional access policies to enforce restrictions.
You can restrict the ability for users to download attachments from email to a local device or block attachments entirely. By using a browser, users are able to view and edit these files safely , without leaking data to a personal devices. I’ll write more about that in another post in this series: Limiting Access to Exchange Online on unmanaged devices.
Final Thoughts
I hope this post helps you with implementing WIP and perhaps even challenges you to do your own testing and share your thoughts with us. I think some of this post can be confusing but non the less, I wanted to share my findings and hope to learn more. Please leave a comment or share this post if you think it might help others.
Links:
- How to wipe only corporate data from Intune-managed apps
- Limitations while using Windows Information Protection (WIP)
- Create a Windows Information Protection (WIP) policy
- Conditional Access in Outlook on the web for Exchange Online
- Set-OwaMailboxPolicy
- User Voice: Extend WIP to protect Outlook mailbox data
Just a long shot.
Could a CSP policy with the following solve it? (if encryption is not supported)
Do not allow an OST file to be created
\Microsoft Outlook 2016\Account Settings\Exchange
Prevents offline folder use at startup. This is equivalent to clicking the Disable Offline Use button in the Offline Folder Settings dialog box.
Thank you for a great blog post!
Not sure if you can push a CSP policy to Azure registered device ??
Hi Jonas,
Maggy is right. You can’t push a csp policy to Azure AD registered devices. They’ll need to be Azure AD joined and Managed by MDM (Intune)
Oktay, Thank you for an outstanding series of articles. I’ve scoured the web for information on this subject (WIP & MAM-WE) for over a week, learning all I could. Your series has stood head-and-shoulders above any other resource or discussion I’ve found. I am envious of your skills, and wish I could write as clearly & concisely as you have done in this series. I am really looking forward to reading the five articles yet to be published. I hope you do get to them.
[…] WIP Without Enrollment Selective Wipe […]
[…] WIP Without Enrollment Selective Wipe […]
[…] WIP Without Enrollment Selective Wipe […]