Last Updated on October 9, 2018 by Oktay Sari
So now that I have a little spare time during my holiday, I couldn’t help my self but thinking about a problem where employees of a client could not open URL’s to websites on their mobile phones. I know I should think about the azure colored sea and sandy beaches waiting for us, but there was something about those links not opening in any browser, including the Intune Managed Browser. Do you have app protection policies configured and users complaining they receive a “No available apps”error when trying to open a URL? Then I hope this post helps a little. In a previous post I wrote about managing BYOD devices with Intune MAM policies and I suggest you read that if all this is new to you.
Intune App Protection Policies
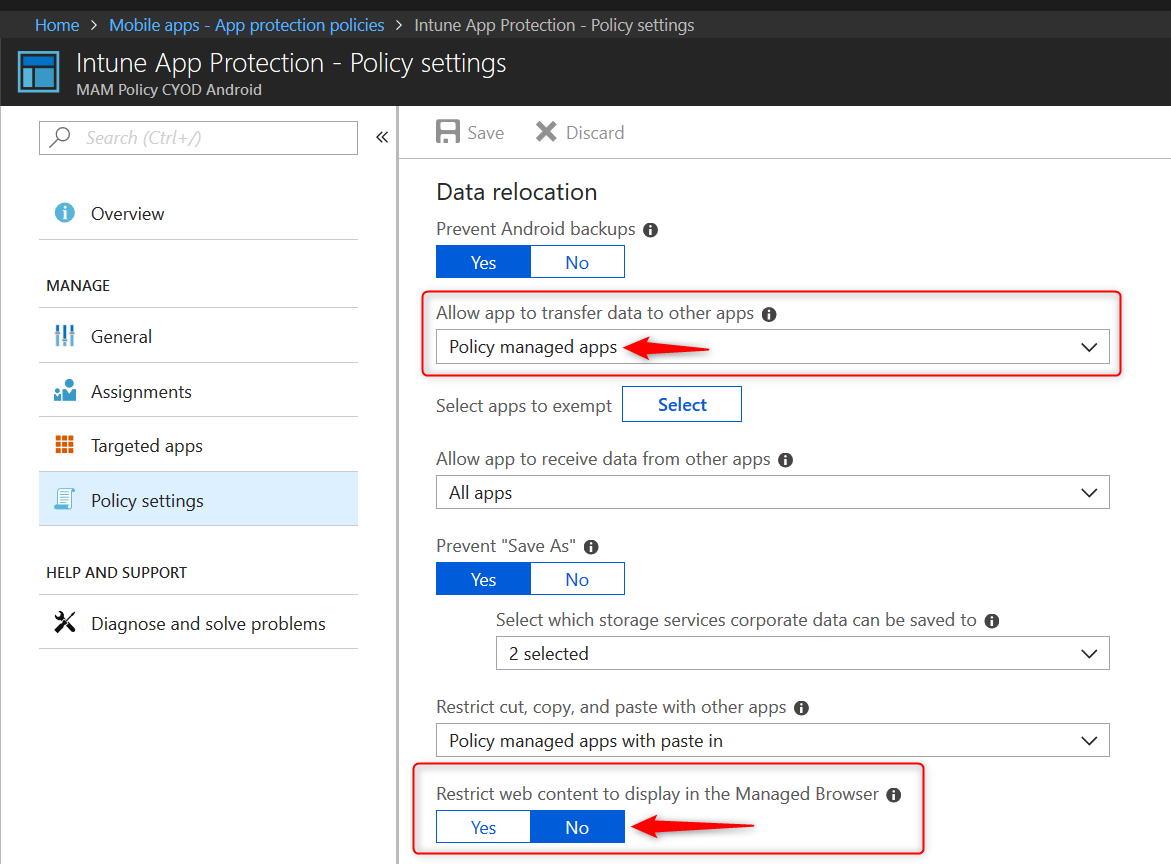
I started reviewing the policies configured and reading up on the documentation. Please see a screenshot for the configuration I started off with.
- Navigate to >Azure Portal> Intune> Mobile Apps> App protection policies
- Open the policy in question
- Click on Policy settings
Notice the following settings:
- “Allow app to transfer data to other apps” has been set to “Policy managed apps”
- “Restrict web content to display in the Managed Browser” has been set to “No”
User experience on Mobile without Intune Managed Browser
I’ll get back on the Policy settings but before I continue, I had to see myself so I enrolled a test Android device to MDM and made sure the policies are applied to my device. Then I tried to open any URL to see what would happen.
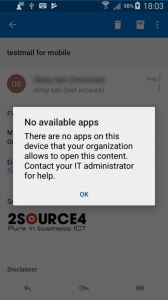 Like all affected users I cannot open a URL. Even after installing the Intune Manged Browser I got the same error “No available apps. There are no apps on this device that your organization allows to open this content. Contact your IT administrator for help.”
Like all affected users I cannot open a URL. Even after installing the Intune Manged Browser I got the same error “No available apps. There are no apps on this device that your organization allows to open this content. Contact your IT administrator for help.”
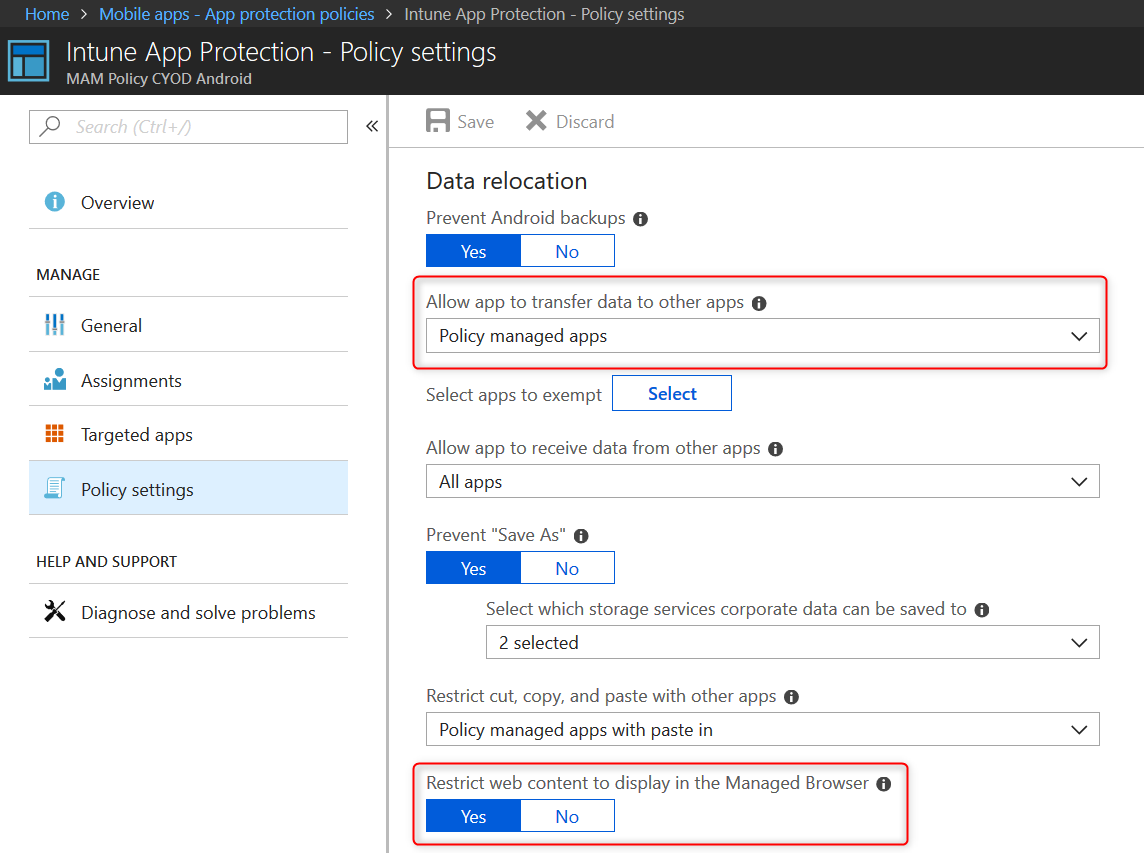
So this is annoying at the very least. The first thing I did was to set the restrict web content to display in the Managed Browser setting to Yes, sync the policy and try again. Now I can open URL’s with the Intune Managed Browser. (Make sure the Managed Browser is installed)
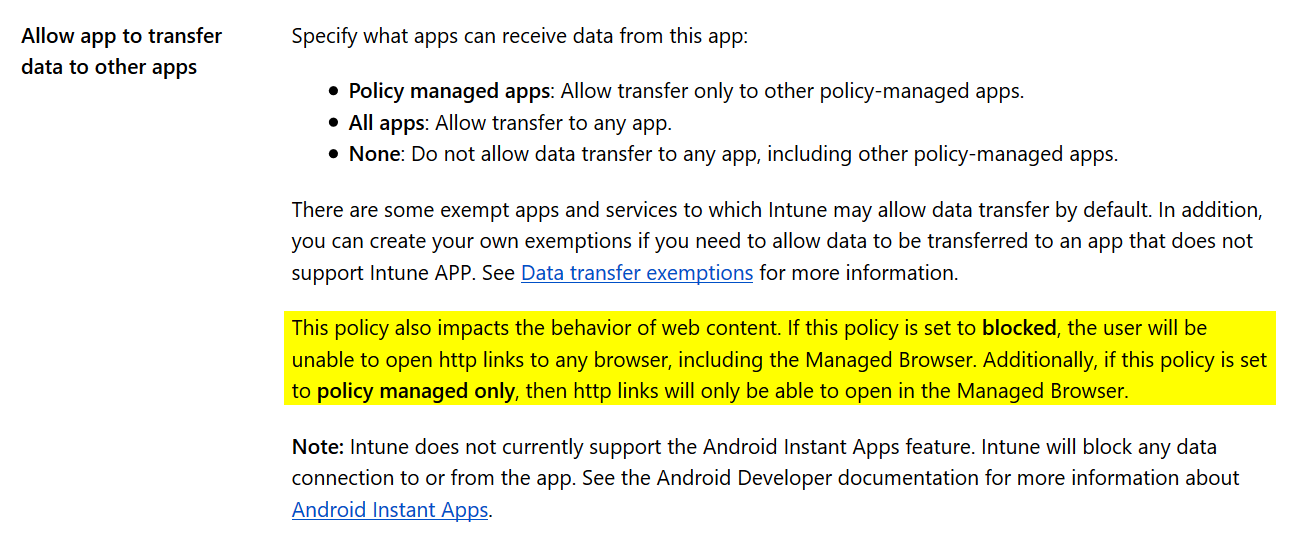
Why did this work? It’s the Allow app to transfer data to other apps setting. This policy impacts the behavior of web content and when set to policy managed apps, then http links will only be able to open in the Managed Browser.
Since the restrict web content to display in the Managed Browser was set to No there are no other apps that can open URL’s and the users will see this error.
You can read the Microsoft documentation about Android app protection policy settings in Microsoft Intune for more info.
Like most of us the administrator started out and configured the settings to the best of his knowledge. He did read How to create and assign app protection policies but did not read about all the possible settings and the impact some of them have. We now have the settings configured like this:
Summary
If you do want to configure the Allow app to transfer data to other apps setting, you will have to think about other implications as well. You might for example want to add Data Transfer Excemptions to allow data transfer between apps. In most cases configuring this policy setting to Allow all apps will work but if you are concerned about data leaks you might want a little more restricting setting.
- Support Tip: Intune APP, Android, and the Managed Browser
- How to create and assign app protection policies
- Android app protection policy settings in Microsoft Intune
- Data transfer exceptions
Hi, I get the same error but in my case the the Restrict web content to display in the Managed Browser setting is Yes and Allow app to transfer data to other apps is set for Policy Managed Apps. There may be a bug with the chrome experience when chrome is set at default browser https://blogs.technet.microsoft.com/intunesupport/2018/07/11/support-tip-intune-app-android-and-the-managed-browser/
Have you encounter such issues?
Hi Mihai, Your configuration still forces links to open in a managed browser like Edge or the Intune Managed Browser. If I’m correct you need to set the “Restrict web content to display in the Managed Browser” to “NO”, and then create the data transfer exception to the browser of your choice. In this case Chrome. Follow this link: https://docs.microsoft.com/en-us/intune/app-protection-policies-exception to read about exceptions to the Intune MAM data transfer policy . Hope this helps
Great article. I have a situation with urls pointing to services where the Android OS will start a third party app like Twitter. The URL (https://twitter.com/etc….) can be opened manually by typing it in the managed browser, but it can’t be accessed directly from Outlook, Teams or any other managed application. I would love to find a way of opening these kind of URL’s in the managed browser instead of failing in the launch of the unsecure app.
Hi Simon, This is a very good question. In my case all links in e-mails will open in the Edge Mobile browser and not the app itself. Since Edge is a managed browser, the users do not receive an error. I think this has to do with deep linking in Android and default app behavior. You could try to reset default apps in Android or configure twitter to open supported links in other apps instead of the app itself. I’m not an expert on Android but have a look at: https://www.makeuseof.com/tag/default-apps-deep-linking-android/ and read the article. It has useful information and… Read more »
Anyone worked out how to manage JPG attachments? There doesn’t seem to be an approved MDM app for this file type (other than use Outlook’s built in viewer).