Last Updated on May 21, 2022 by Oktay Sari
This month, we had a company event at Rapid Circle and I did a presentation about Security Baselines vs Endpoint Protection templates vs Settings Catalog vs device configuration policies. Yeah… that’s a mouth full.
For a change, I didn’t want to do a technical deep dive, but instead, talk more about some best practices and tips & tricks. Therefore I aimed for a 200+ level presentation.
So This time, a blog about something else.. It’s the presentation I gave, and I hope that it’s also interesting enough for you, and that you can appreciate this somewhat different post. Most of the pictures in this post, are the actual PowerPoint slides I used. Let me know what you think below in the comments section. I’m kind of stepping outside my comfort zone here.
I wanted to come up with a different title from what I normally have, and after a couple of hours I came up with “What Zombies can teach you about Security Baselines” I thought that might intrigue people a little bit more than “Security Baselines vs Endpoint Protection templates vs Settings Catalog vs device configuration policies”. I let it sink in for a couple of days and then started to think about the actual content. More importantly I was wondering if Zombies could actually teach us something about Security Baselines. Oh…boy…this is going to be harder than I thought.

I ended up with a crazy idea to come up the stage like a Zombie…Yup, I actually got myself a zombie suite and did it. Way outside my comfort zone now! I’m OK with a normal presentation but this time my knees are actually shaking and I feel nervous.
So after playing a short, apocalypse/end of days like homemade intro-video where I say goodbye to my parents and colleagues the video stops abruptly…
Simultaneously, I walk up the stage in a Zombie suite bumping up the chairs in front of me while people are still watching the intro video. I felt like one of the Zombies in Walking Dead! (and awfully awkward at the same time). People turn their head around and see me (in a zombie suite) walking…
I’m trying to see through the mask and get a glimpse of the people in front of me. Are they going to shoot me or not? Luckily, the audience can appreciate it and a liberating laughter is heard through the hall. I feel good not being shot. Finally up on the stage one of the first questions I ask is;
Who came for the title? Show of hands please… Oh boy… no pressure… I bet ya, I’m the first zombie telling you something about security baselines…

Here’s the evidence… Yup, that’s me… 🙂
MEM Device Configuration methods
Now, for the serious part… With Microsoft Endpoint manager you can configure devices using a variety of methods. You have security baselines, endpoint security templates, settings catalogs, device configuration templates and scripts, compliance policies and then some…

In this post, we’re going to have a look at these methods and try to learn more about the difference between them, as well as, when to use what.
Best practices configuring Windows devices
I’ll try to outline some of the best practices when configuring Windows devices using Endpoint Manager. When you configure your endpoint policies, try to start with security baselines, Microsoft’s recommended best practice configuration. If you want to configure specific security settings, like Defender for Endpoint, Bitlocker of Firewall settings, Use Endpoint Security templates. Then fill in the gaps with settings catalogs. If for whatever reason, you cant configure something there, you can always fall back to the (legacy) device configuration profiles/admx templates.
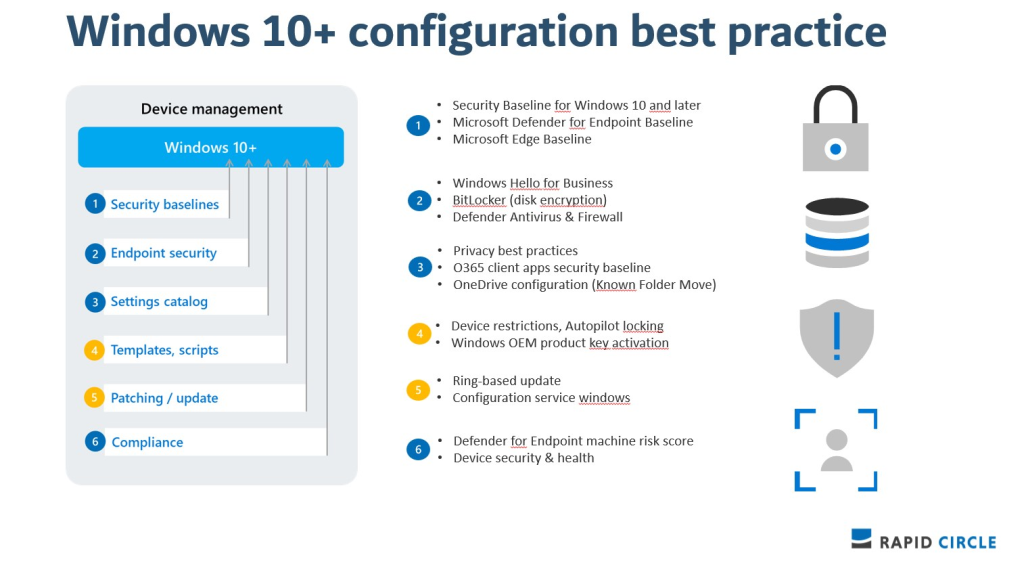
Security Baselines
Security baselines are pre-configured groups of Windows settings and default values that are recommended by the Microsoft security teams. It’s actually a template that consists of multiple device configuration profiles. They Include the best practices and recommendations on settings that impact security and are a good starting point to quickly create and deploy a secure configuration profile.

When it comes to security baselines, you should start with the defaults. But defaults are just that right? When a default value doesn’t work for your environment ( and I bet in most cases the don’t) , you customize the baseline to your needs. Furthermore, you should always check each and every setting that is configured in a baseline! Yes, that’s what I actually mean and I’ll show you why shortly.
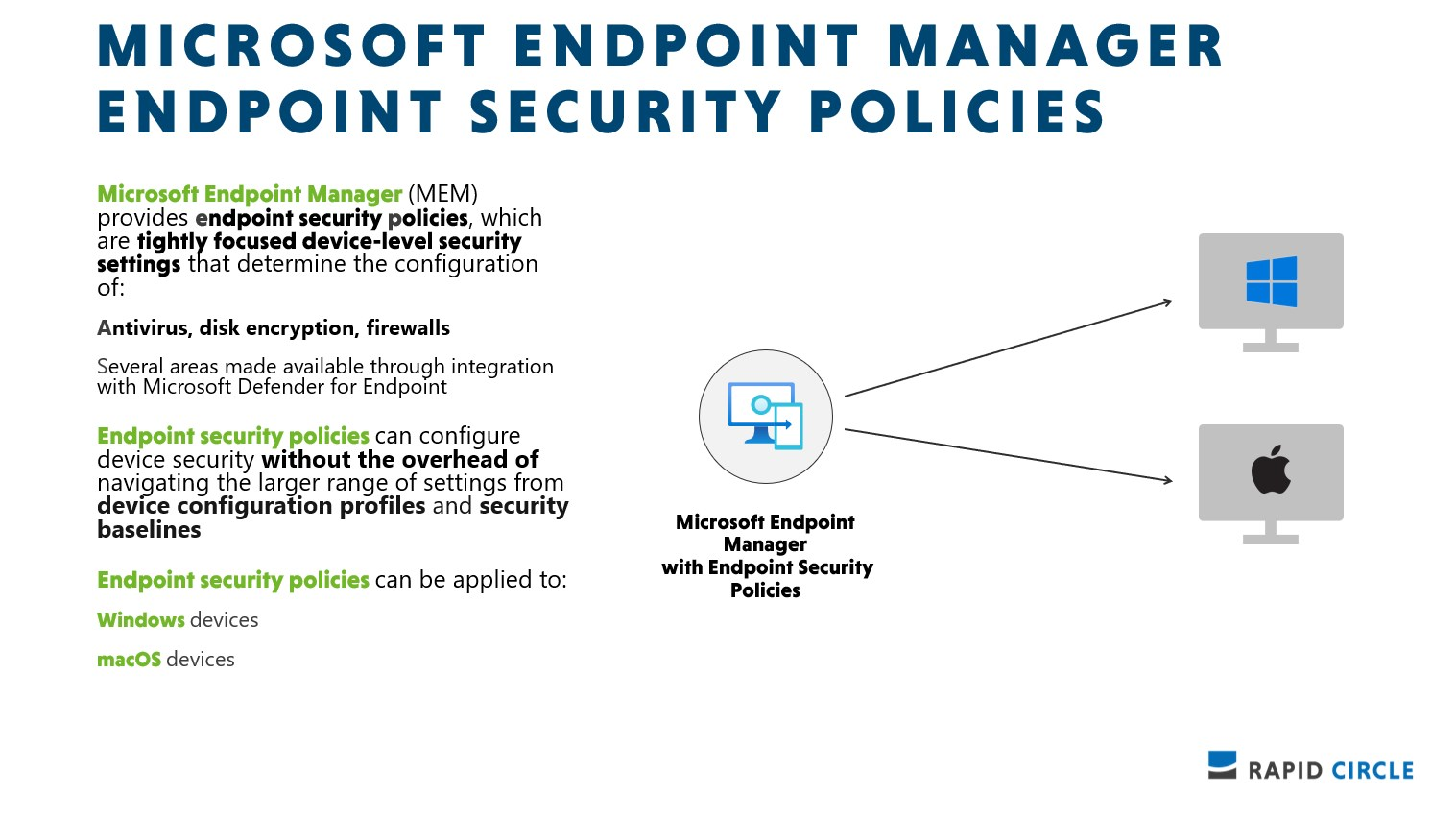
Endpoint Security policies
Microsoft Endpoint Manager (MEM) also provides Endpoint Security Policies, which are tightly focused device-level security settings that can configure settings for Antivirus, disk encryption, firewalls and account protection.
One of the benefits is that endpoint security policies come without the overhead of settings from device configuration profiles and security baselines. They can be applied to Windows devices and macOS devices.
Settings Catalog
Settings catalog are something else. I learned to appreciate settings catalog more and more over time. They lists all the settings you can configure, in one place. So if you want to configure each and every setting for OneDrive for Business, you go for settings catalog! Settings catalog can be applied to Windows devices and macOS devices. You can also configure Edge and Chrome settings!
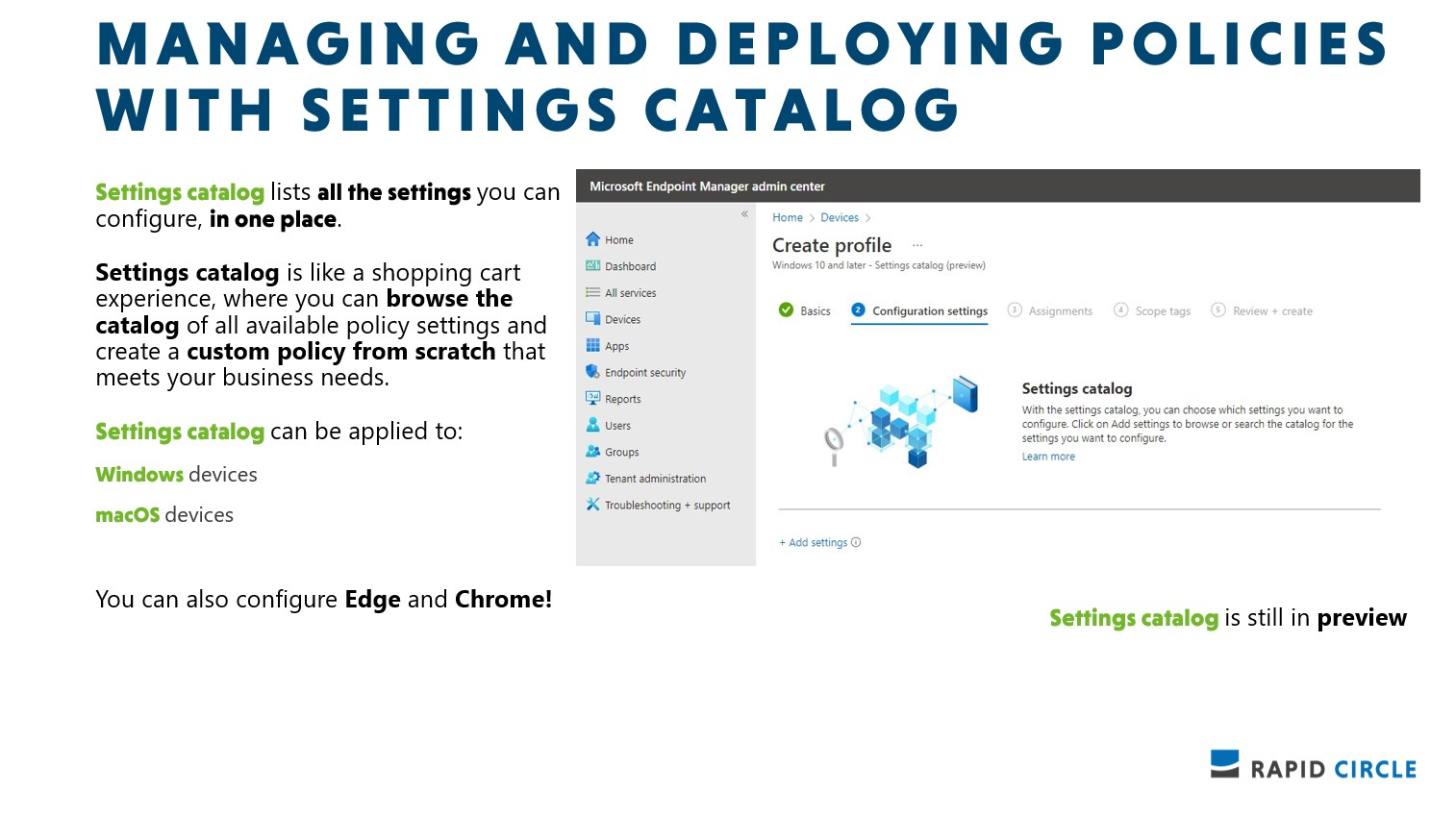
Although settings catalog is still in preview, it is the recommended method to configure devices. More and more settings are added to the settings catalog, and it makes custom OMA-URI policies almost redundant. You should definitely use settings catalog when ever possible.
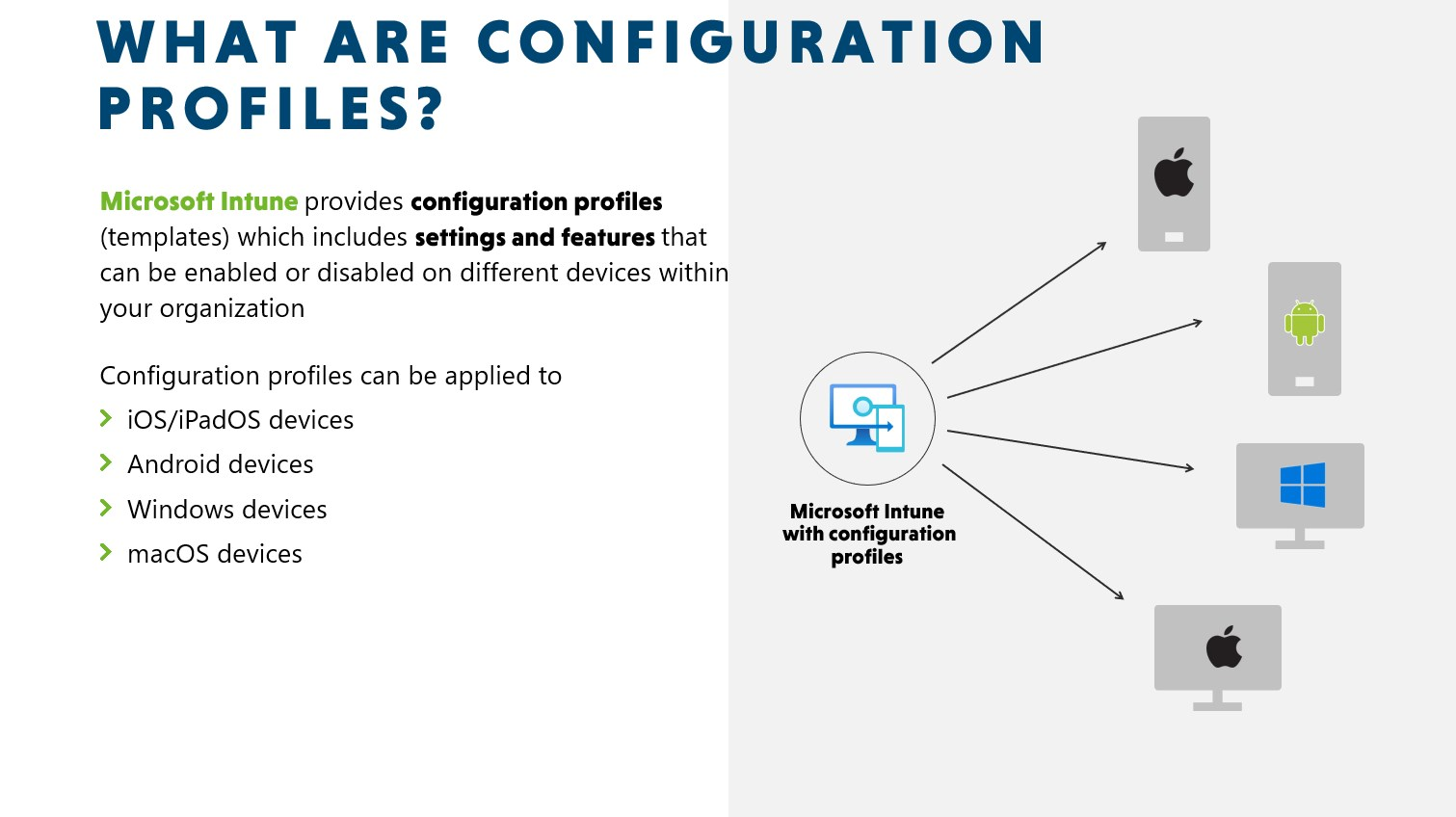
Device Configuration Profiles
Then finally, we also have the good old configuration profiles. I still see many tenants, that almost totally rely on these legacy configuration profiles. I don’t think It’s going to disappear anywhere soon and for sure, there are still many configuration profiles you can use for Android, iOS and Windows devices. But it should be your last resort for Windows devices. All the juicy new stuff, will go to the first 3 options.
Configuration profiles can be applied to iOS/iPadOS devices, Android devices, Windows devices and macOS devices.
What have we learned this far
- Security baselines are pre-configured groups of Windows settings and default values that are recommended by the relevant Microsoft security teams.
- Endpoint security policies can configure device security without the overhead of settings from device configuration profiles and security baselines.
- Settings catalog lists all the settings you can configure. If you want to see all the available Firewall settings, or all the available BitLocker settings, then use this option. Also, use this option if you’re looking for specific settings.
- Templates include a logical group of settings, such as device restrictions, kiosk, and more. Use this option if you want to use these groupings to configure your settings.

Born to Click
You are born to click right? Way ahead of the curve… So you go out and configure every security baseline you can get your hands on, and deploy it to all devices, because….it’s best practice…and what could go wrong? For this slide, a baby zombie was just too cruel, but I think this picture is just right 😉
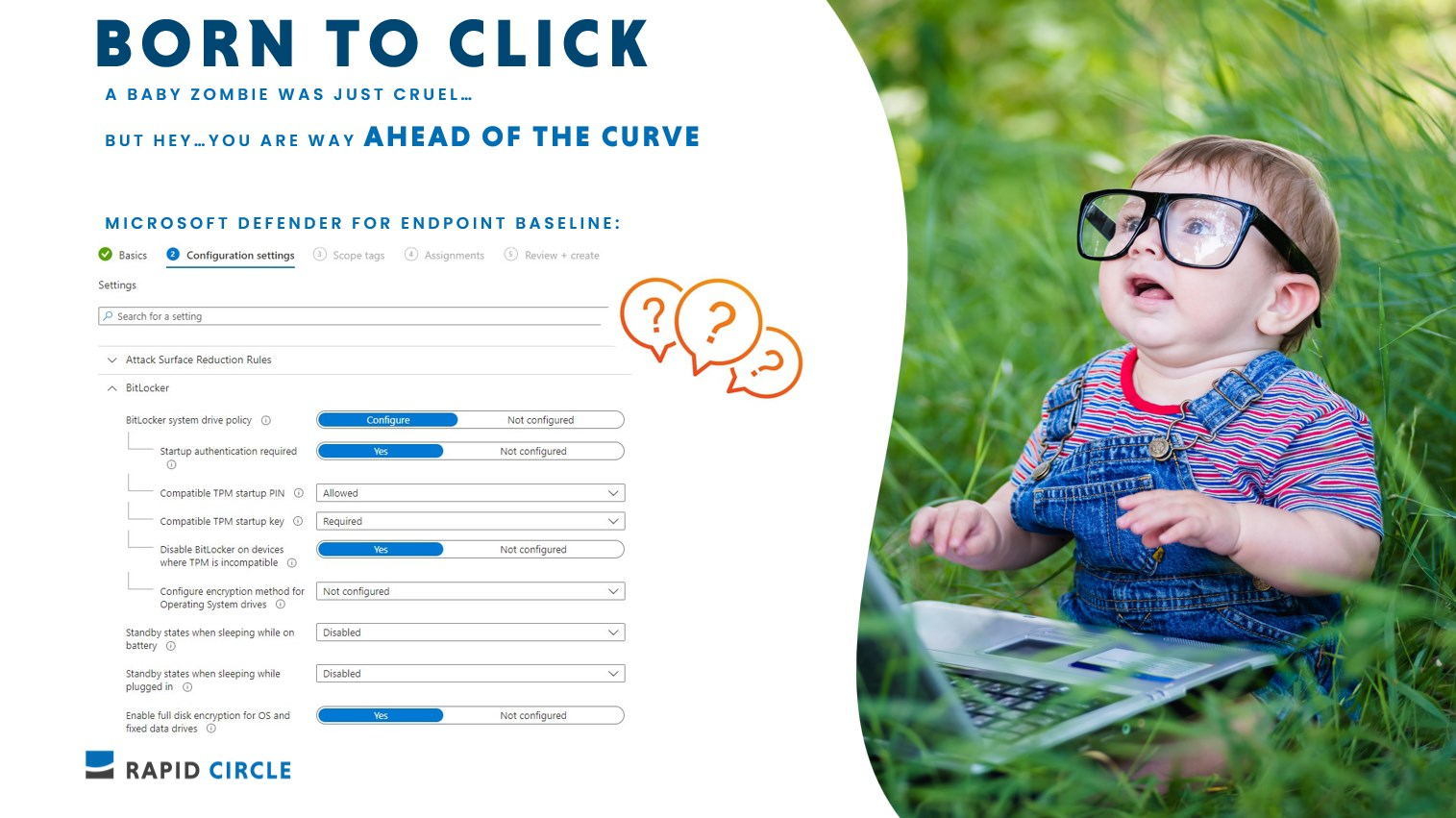
Here’s an example of a default MDE Security Baseline. Do you see what’s wrong with this configuration right here?. Let’s assume we have Autopilot in place and deploy devices with zero touch. What is wrong with this default defender for endpoint baseline?
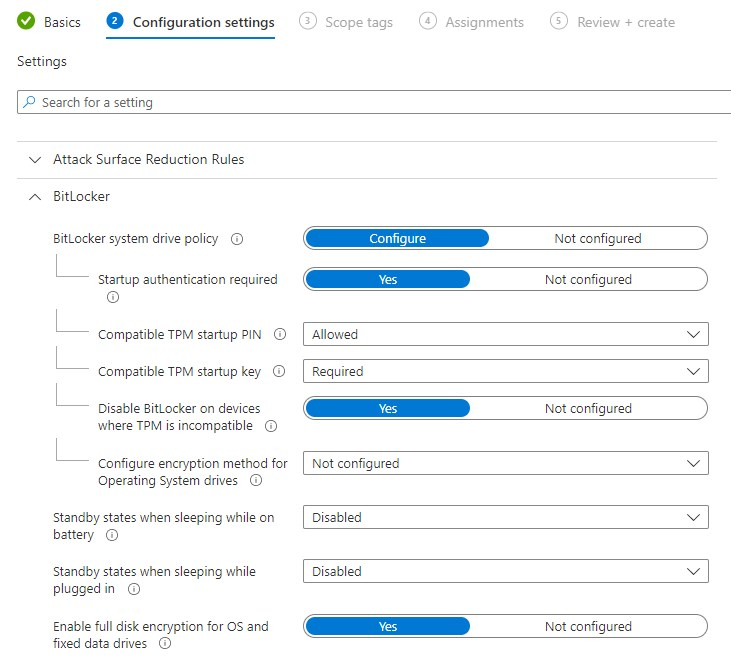
There’s really nothing wrong with it. I can work just perfectly as is. Nut now read this again “Let’s assume we have Autopilot in place and deploy devices with zero touch”
I’ll tell you why this default policy will not work in this scenario.
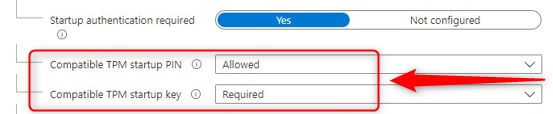
When you click on the tooltip you’ll read this: “For silent enable scenarios (including Autopilot) this setting cannot be successful, as user interaction is required. It is recommended that PIN is disabled where silent enablement of BitLocker is required.”
So your end users are going to have to deal with questions they probably don’t know the answer to. That’s a no-go.
Now here comes another thing. Let’s assume you decide to flip the switch for this part of the configuration. You are setting “Startup authentication required” to “Not Configured” like this:
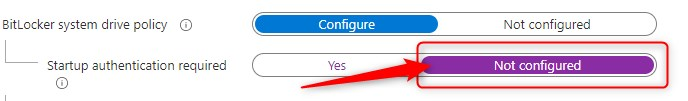
One second thought, you decide to flip the switch back to “Yes”. Pay attention here.. because now, the default (and recommended?) settings are different then before. This time, they almost got it right!
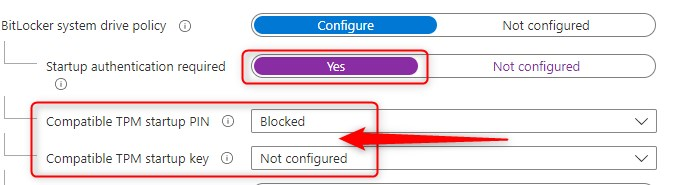
I provided Microsoft with feedback about this behavior and when I hear back from them, I’ll update this post again.
Making Impact
What I’m trying to tell here is this. Nobody is perfect. When someone tells you, something is best practice, don’t assume it is for your scenario! Always understand the impact of the configuration you deploy and double check! And yes, that means you have to understand each and every setting you configure.
Go for the smart way to make an impact

If you do decide to go for the easy way and accept every default configuration, I can tell you this much…you are going to make an impact… An impact on your users. They will probably go zombie on you, or their devices. You will also have an impact on your support engineers. Because they will have to deal with everyone calling the support desk.
Trusted to Deliver
Avoid backing yourself into a corner by going with the defaults because it’s easy and convenient. You are trusted to deliver a secure and conflict free configuration.
So you better put on your best smile when the big boss calls… 🙂

Avoid Conflicts
Managing the same setting on the same device through multiple policy types, will result in conflicts and you should give it your best to avoid that . You can avoid conflicts by not using different baselines, instances of the same baseline, or different policy types and instances to manage the same settings.
- Separate baseline types can include the same settings but use different default values for those settings.
Read that again! This sounds so strange and confusing to me. But for now, it’s a fact we have to deal with. I’m repeating myself; make sure you understand what you are configuring.
- Security baselines often manage the same settings you might set with device configuration profiles or other types of policy.

- For example, the settings found in Endpoint security policies are a subset of the settings that are found in endpoint protection and device restriction profiles in device configuration policy, and which are also managed through various security baselines.
- Use Intune’s built-in tools to identify and resolve the source of conflicts
Make sure you plan ahead, which methods you’ll use to deploy configurations. When you do use multiple methods to configure the same setting, make sure your policies either agree (both configure the same setting) or aren’t deployed to the same devices.
Here’s a bonus.. Compliance policies can also conflict with other policies!
- Compliance policy settings always have precedence over configuration profile settings
- The most restrictive compliance policy setting applies
- When the password requirement is changed for W10+ (within your compliance policy). Users with passwords that meet the requirement are still prompted to change their passwords. Yes that’s right. So try to make sure your compliance policies are configured correct the first time!
Finally…
Intune settings are based on the Windows configuration service provider (CSPs). The behavior for these settings depends on the CSP. Some CSPs remove the setting, and some CSPs keep the setting, also called tattooing. This means that when you change a policy, some settings, will still keep the setting you originally configured, For example, you changed something from blocked, to not configured. With some settings, the device keeps the setting at blocked.
If you want to apply a less restrictive profile, some devices may need to be retired and re-enrolled in to Intune. That means that you may have to retire and re-enroll Android, iOS/iPadOS, or even Windows devices.
Plan ahead
I like to have brain(storm) session with customers and really pick their brain to have a taste of what their needs actually are.
Better together
Zombies work better together, right? When configuring devices using Endpoint Manager, you’ll find that the real strength to configuring and securing devices, comes from combining various configuration methods.

Final note
I actually had a lot of fun preparing for this presentation. It was a company event and I felt comfortable enough to do this. Would I do this for a customer? I guess “not wearing a zombie suite” I was hoping that the actual content was interesting enough but tried to have some sort of a link with zombies. A big thank you to Rapid Circle for giving me the opportunity to go off the “beaten path” Although I was wearing a zombie suite, I also felt like a pioneer!
Sources and links
- Learn about Windows security baselines you can deploy with Microsoft Intune | Microsoft Docs
- Manage endpoint security policies in Microsoft Intune | Microsoft Docs
- What’s new in Microsoft Intune | Microsoft Docs

Nice one Oktay!!! The zombie theme is actually quite suitable 🤥
Thx Bobby 😉
[…] What Zombies can teach you about Security Baselines. My kids love zombie stories. In IT stories, zombies are a serious nightmare, so I don’t like them. But what can zombies teach us nonetheless? The best way to learn is from examples where other people have f*cked things up. It is from these screw-ups that good practices are drawn. […]
Good info Oktay! Very well explained.
Also, the zombie theme is nicely syncing with the blog 😀 😀