Last Updated on October 17, 2021 by Oktay Sari
While passwordless authentication with Windows 10 and Azure AD is possible for quite some time, many organizations still use older and less secure authentication methods. I guess there is still a lot of mystery around going passwordless. Some System administrators are concerned about difficult time consuming configuration changes and user adoption challenges. With this blog, I hope you’ll learn more about passwordless authentication and how to get started.
- First we’ll cover the basics, and I’ll review the FEITIAN BioPass FIDO2 Security key
- The second part of this post covers the administrator actions to configure passwordless authentication with Windows 10 and Azure AD
- Then we’ll see what the user experience is like
- I’ll end with some final thoughts and thing to remember
What is passwordless authentication?
Lets start with the basics; Passwordless authentication is any form of authentication that doesn’t require the user to provide a password (obviously)to sign-in to Windows 10 or any service on the web. Microsoft Azure supports the following passwordless options;
- Windows Hello for Business
- The Microsoft Authenticator app
- And FIDO2 security keys
This blog is all about going passwordless with FIDO2 security keys. With a Security key you can log in passwordless to:
- Microsoft 365 web apps using a supported browser
- Apps federated with Azure AD
- Azure AD joined or Hybrid joined Windows 10 devices
- And other web apps/services that support FIDO2
What is a FIDO2 security key?
Google FIDO2 for more info or have a look here. I’ll keep it short; The FIDO (Fast Identity Online) alliance promotes open authentication standard. It’s goal is to create strong authentication by reducing the use of passwords.
Which FIDO2 keys support passwordless authentication with Windows 10 and Azure AD?
There are many vendors that offer FIDO2 security keys and If you want to know which are compatible with Azure and Microsoft 365, have a look at this site. In this post, I’ll be using the FEITIAN BioPass (Biometric Security key) with the build-in fingerprint sensor. A big thank you goes out to Della Han from “FEITIAN Technologies Co., Ltd.” For providing the security keys for testing.

I’ve used FEITIAN products before and in a previous post I wrote about OATH TOTP Hardware tokens with Azure MFA using the C200 TOTP token.
FEITIAN BioPass FIDO2 security key
Here’s my first impression for the all metal FEITIAN BioPass FIDO2 security key. The key looks great, comes in both USB A and C, and to me, it feels rock solid! I was concerned that the Security key would wiggle in my USB port when trying to authenticate using my fingerprint but it responds to a very light touch and lightning quick! You don’t have to push down risking damage to your USB port.
The fingerprint module prevents any misuses of the token from people other than authorized user and this little key can store up to 50 fingerprints! . The key has a red and a green LED, indicating failed or successful fingerprint verification. Watch the LED when you put your finger on the sensor. There is one thing you need to keep in mind. If you fail to verify your fingerprint 15 times in a row, you will have to reset the device. Once reset, all data including your fingerprints and credentials will be deleted.
You can use standard Windows 10 settings to manage your key, but the BioPass FIDO2 Manager for Windows gives you more control and even an option to test your fingerprints.
On with the setup! Let’s dive into Azure and configure passwordless sing in.
Requirements for passwordless authentication:
- Azure AD Multi-Factor Authentication
- Enable Combined security information registration
- Compatible FIDO2 security keys
- For Azure AD joined devices the best experience is on Windows 10 version 1903 or higher.
- Hybrid Azure AD joined devices must run Windows 10 version 2004 or higher.
Enable passwordless authentication with Azure AD
Let’s enable passwordless authentication in Azure AD. Browse to:
- Azure AD > Security > Authentication methods
- Click on FIDO2 Security Key
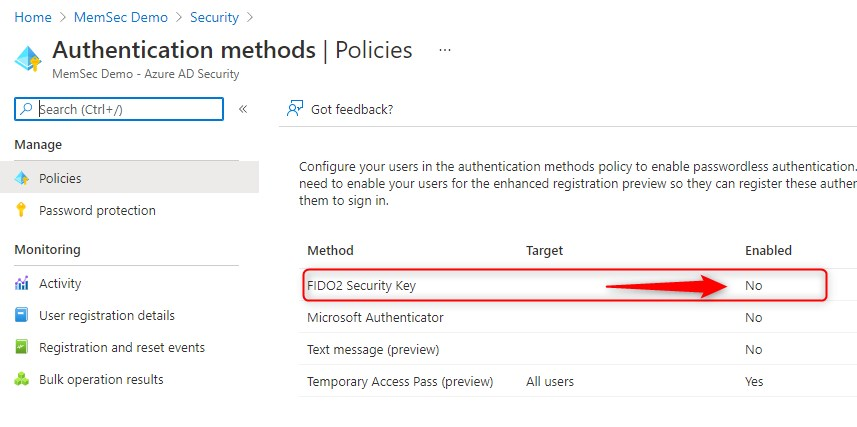
- Select ENABLE > Yes
- Select All users or select a group of users

- Click Configure for some optional settings:
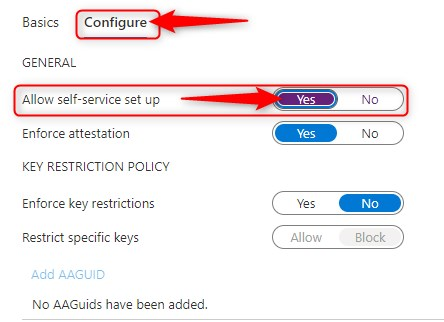
The default configuration here should be just fine. Most important setting here is the “Allow self-service set up” option. This should remain set to Yes. If set to no, your users will not be able to register a FIDO key. Yes, you did read that correctly. Users need to setup their own FIDO2 Security key. It’s as easy as configuring the Microsoft Authenticator app.
Enforce key restrictions should be set to Yes only if you want to only allow or disallow certain FIDO security keys. See the links below for more information.
You have successfully enabled FIDO2 Security Key for Sign in and Multi Factor Authentication (Strong Authentication)
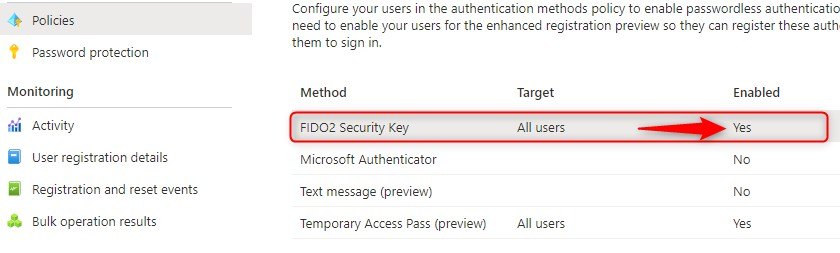
Note: This does not mean you are ready for passwordless sign in to Windows 10. You can however login to Microsoft 365 apps using a browser and a configured security key.
Enable passwordless security key sign in to Windows 10
Signing in using a security key while working in a browser is great, but we want to take this a step further so we can also sign in to our Windows 10 devices without using a password.
You will have to enable “Use security keys for sing-in” option in your tenant for this to work. This can be done in two ways. A tenant wide setting targeting all users, of a more granular method where you can target specific user or device groups.
Enable tenant wide with Windows Hello for Business:
- Browse to Microsoft Endpoint manager admin center
- Go to Devices > Device enrollment > Enroll devices > Windows Enrollment > Windows Hello for Business
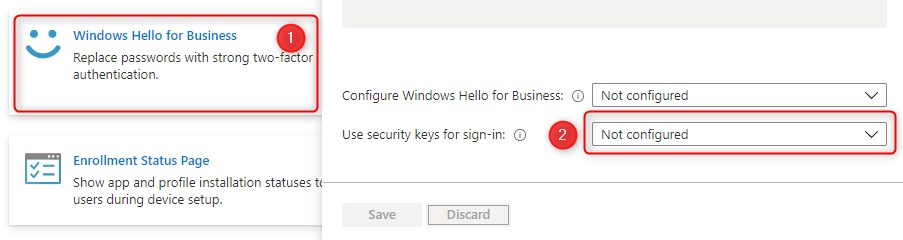
Device configuration profile for Windows Hello for Business
You can also use a device configuration profile (Identity protection) to configure devices for Windows Hello for Business. Identity protection profiles can target assigned users or devices, and apply during check-in.
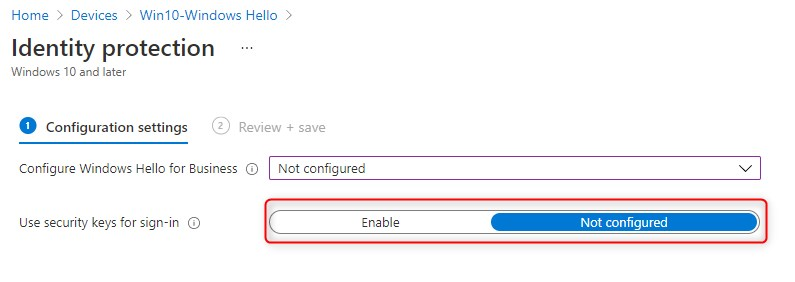
Choose the options that is best suits your needs. You will need to Enable this setting to continue. For the purpose of this test, I’ve used the tenant wide setting and enabled it there.
Note: This setting does not depend on Windows Hello for Business so you do not need to change that if you don’t want to. However, I highly recommend you enable Windows Hello for Busines.
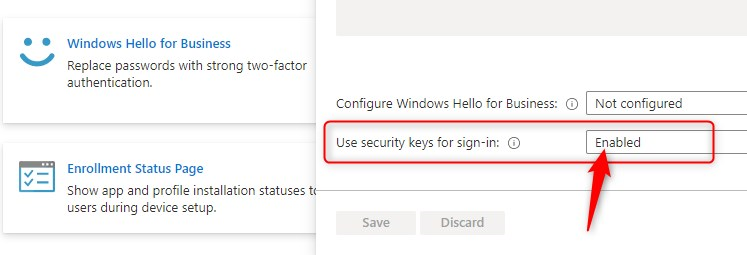
It might take a while for the new setting to be available for your users. If you used a device configuration profile, you’ll have the option to see if the policy deployed from within Microsoft Endpoint Manager. When everything is set you will have the option to sign-in with your security key
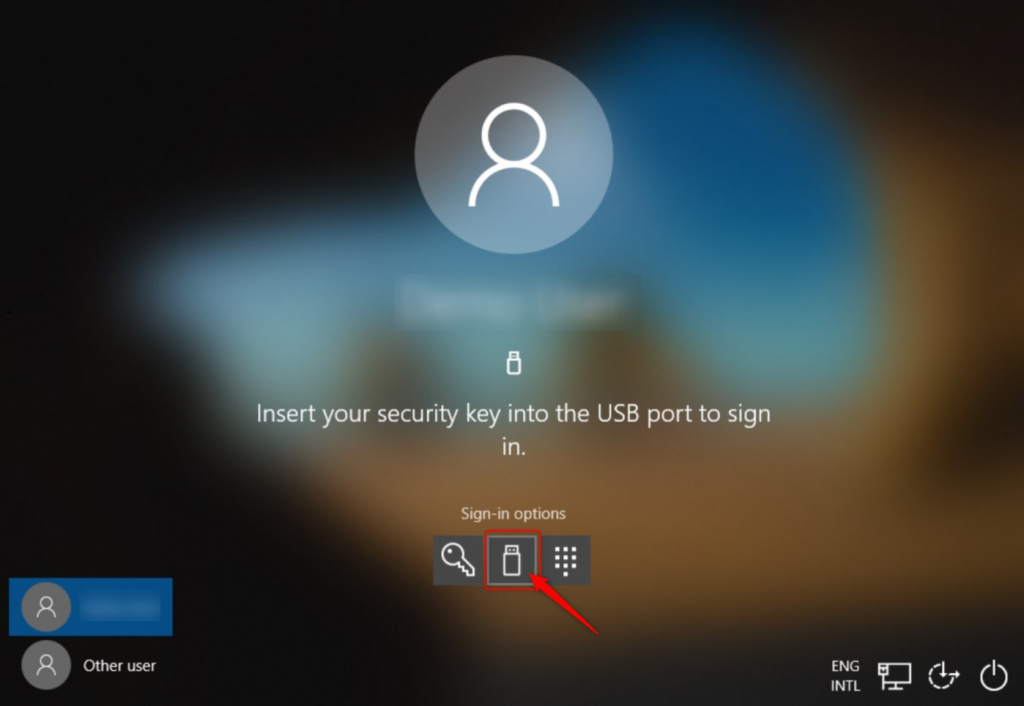
User experience – Configuring a FIDO2 Security key
There are a few options to add and configure your FIDO2 Security key. This post will focus on the first two options:
- You can use the build-in Windows Security key manager (Settings > Sign-in options)
- You can also go to https://aka.ms/mysecurityinfo to setup your security key in Azure
- The FEITIAN BioPass I used has a key manager you can download
Option 1: Windows Security key manager
- Go to Settings > Sign-in options
- Click Security keys > Manage
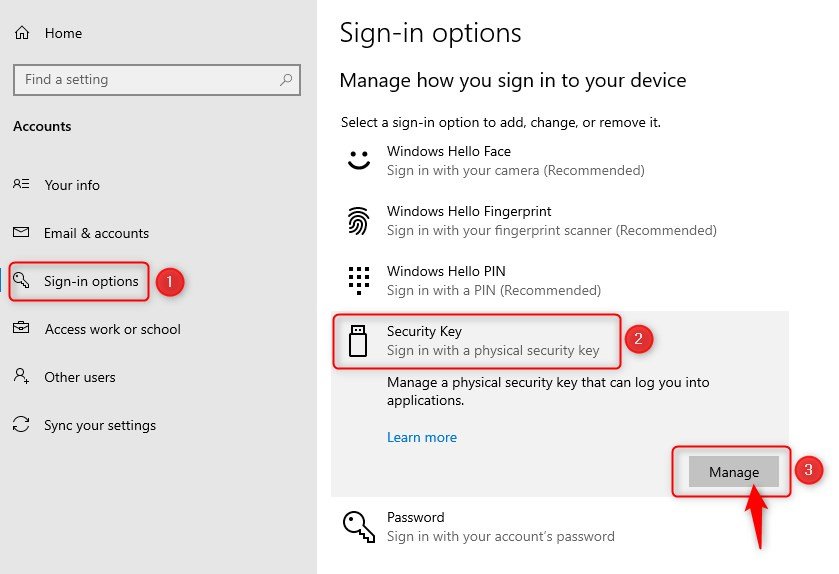
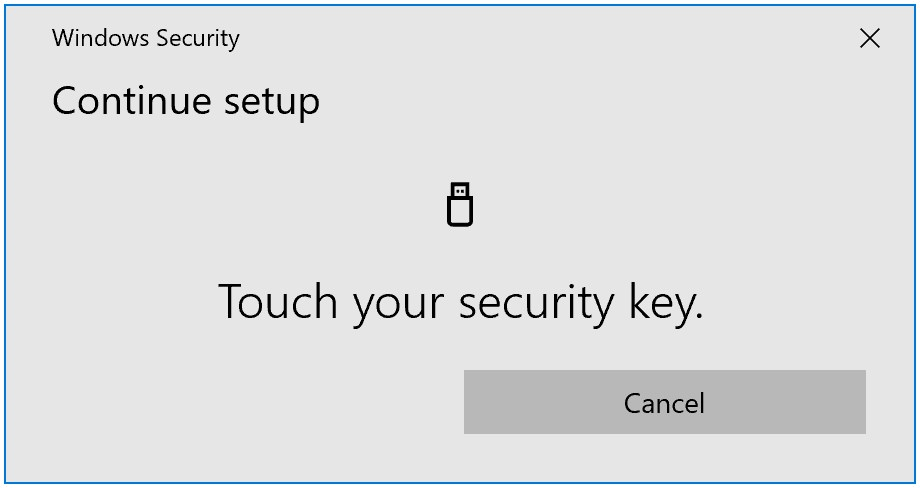
- Insert your Security key
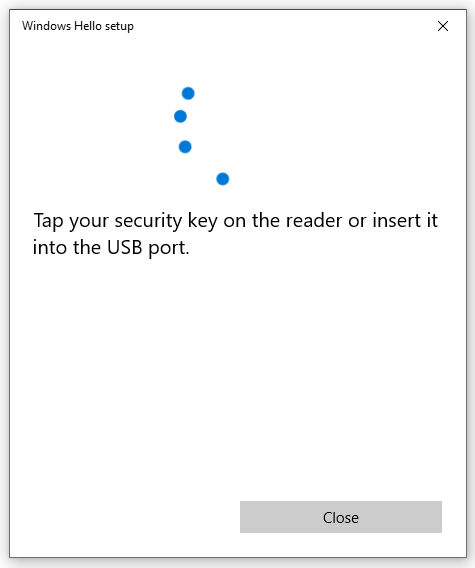
- Touch your security key

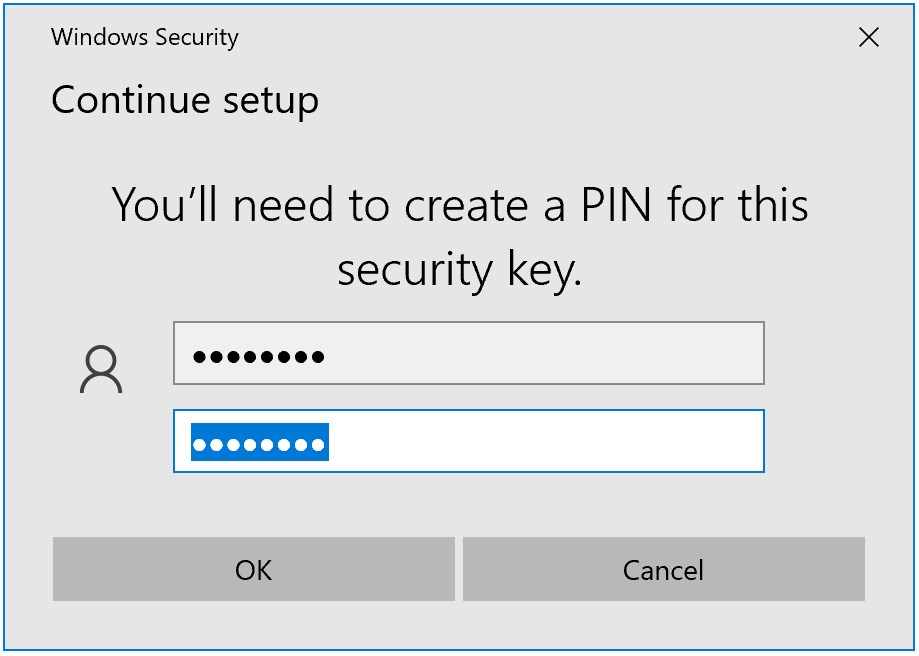
Since I’ve already setup a PIN earlier, I’ll continue with setting up Fingerprint.
Note: I’m using the FEITIAN BioPass FIDO2 Security key. Your experience could be a little different depending on the key you have. If you did not used or configured your security key before, than you’ll first need to setup a PIN, before you can add a fingerprint.
Select Security Key Fingerprint and click on Set Up
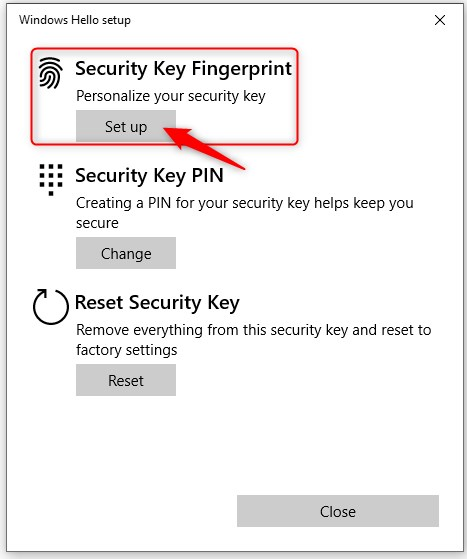
- Type in your PIN
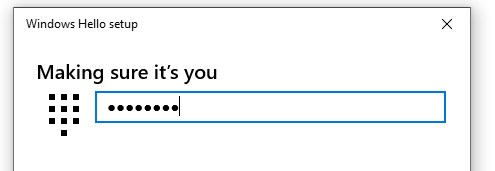
- Follow the instruction to setup a fingerprint
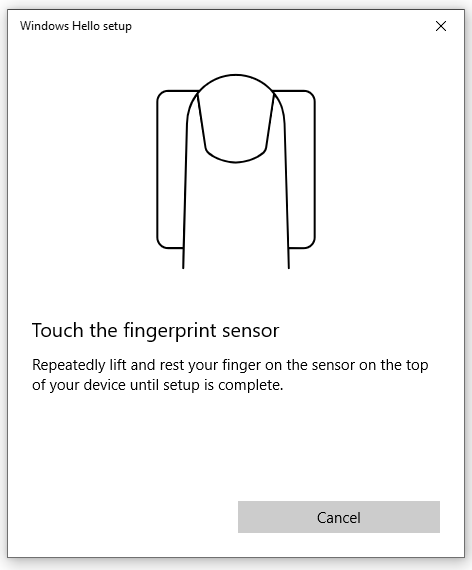
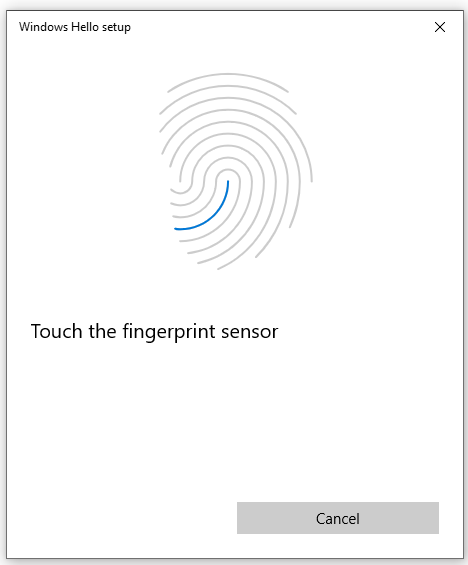
When you are ready, Add another finger as a backup in case you cannot use your primary finger and then finally close the window.
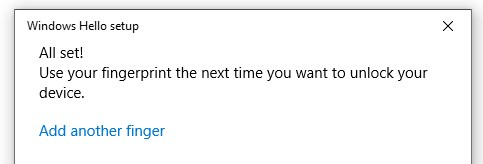
Option 2: Azure AD Security info
Users can configure the methods they use to sign into their account or reset passwords in Azure AD.
Browse to https://aka.ms/mysecurityinfo to see all assigned Authentication methods available for sign-in or MFA.
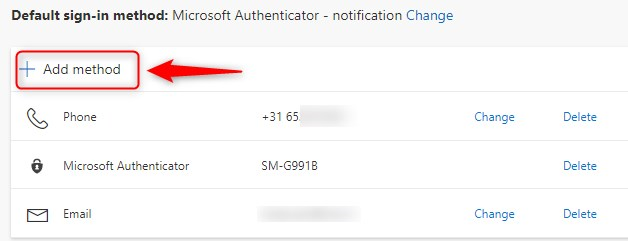
- Click Add method
- Select Security key
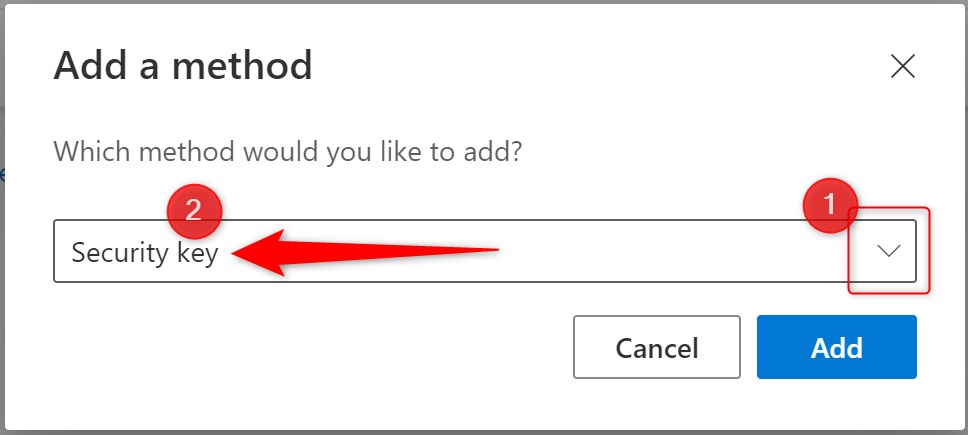
- To set up the security key follow the setup assistant. You will have to sign in with MFA authentication to continue.
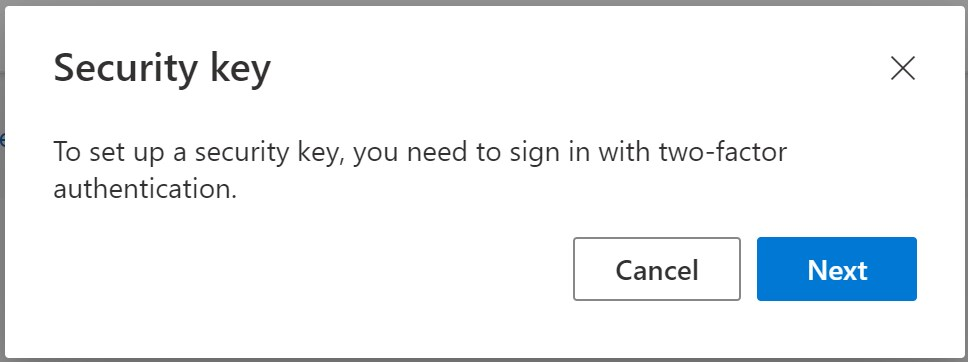
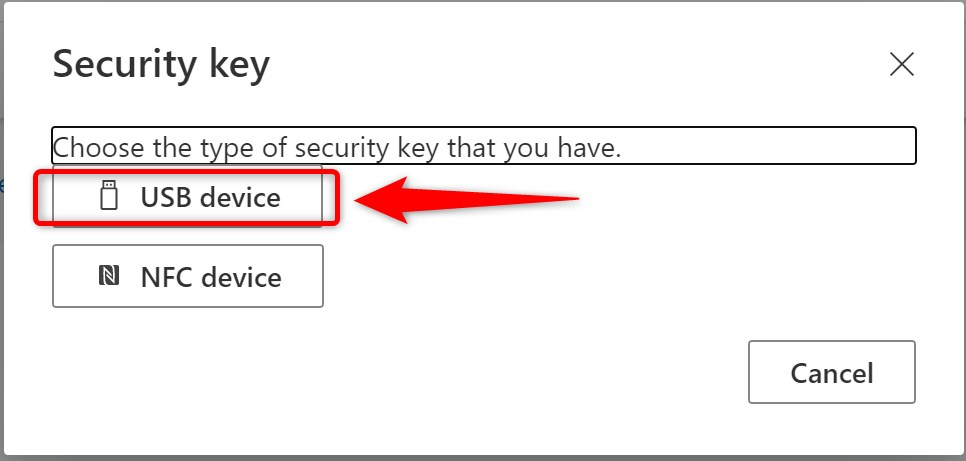
- In this case I’m Choosing USB device
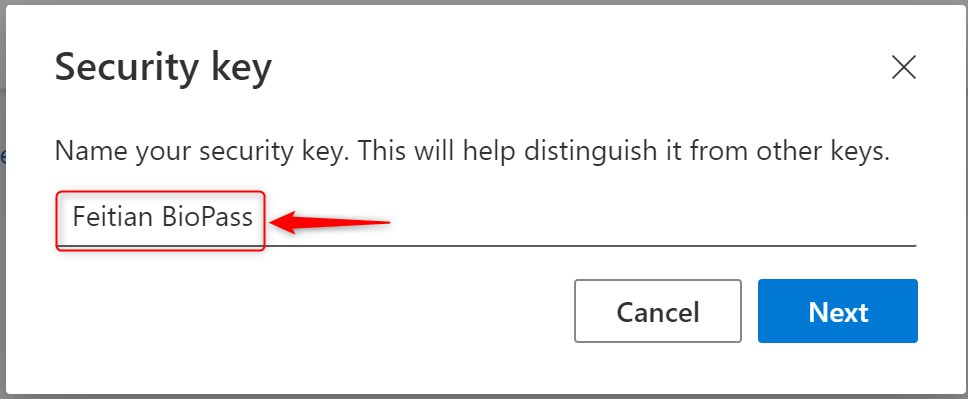
- Have your key ready and click Next
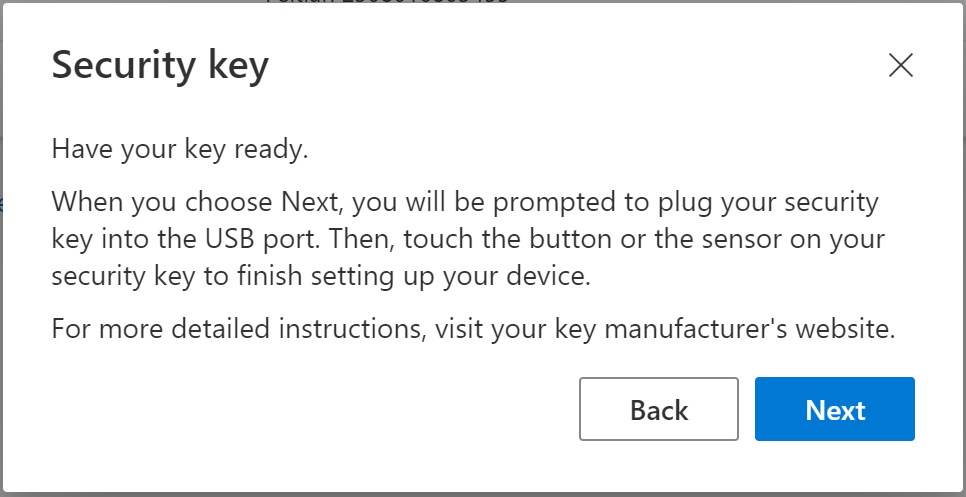
A few more screens…
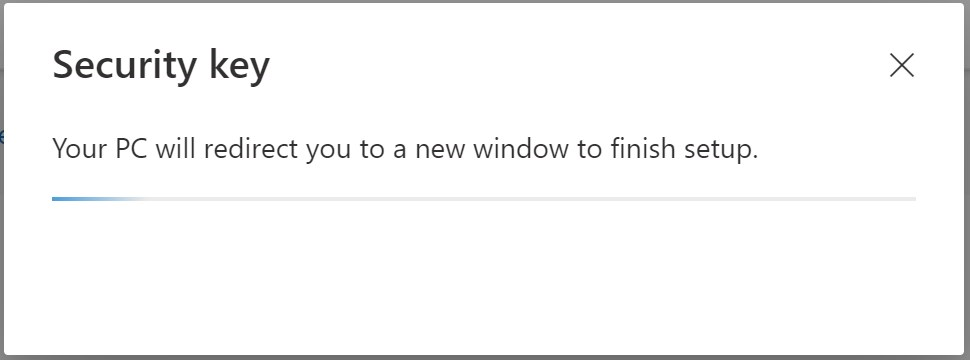
Have your security key ready:
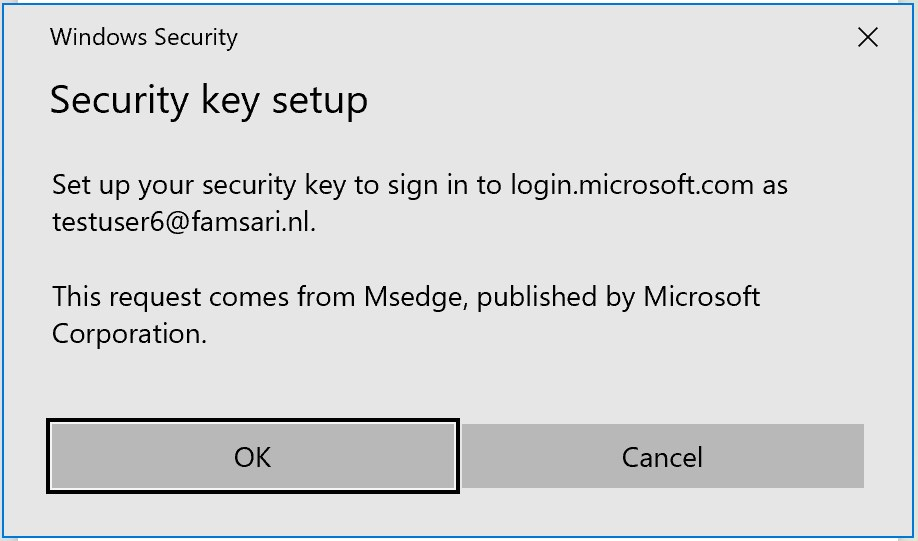
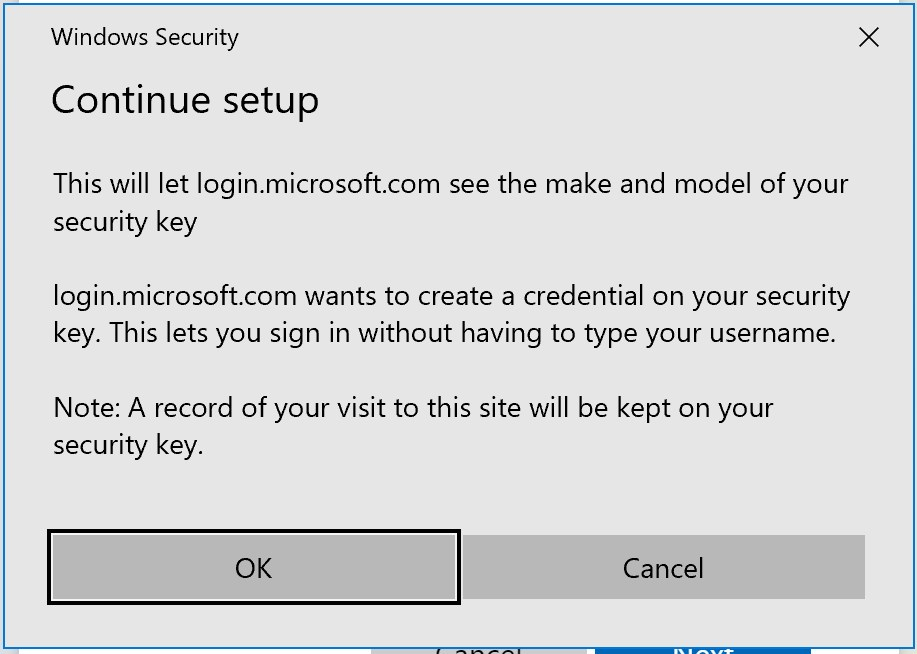
Insert your security key:
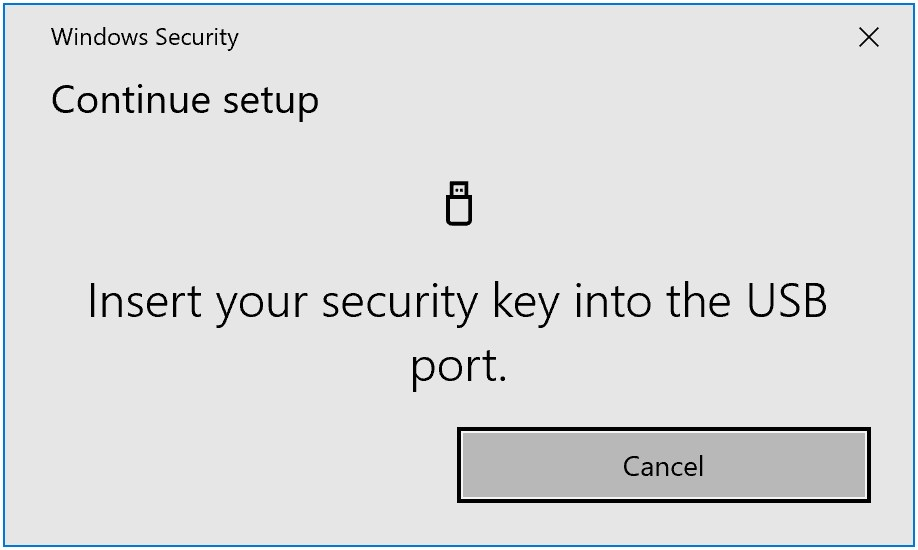
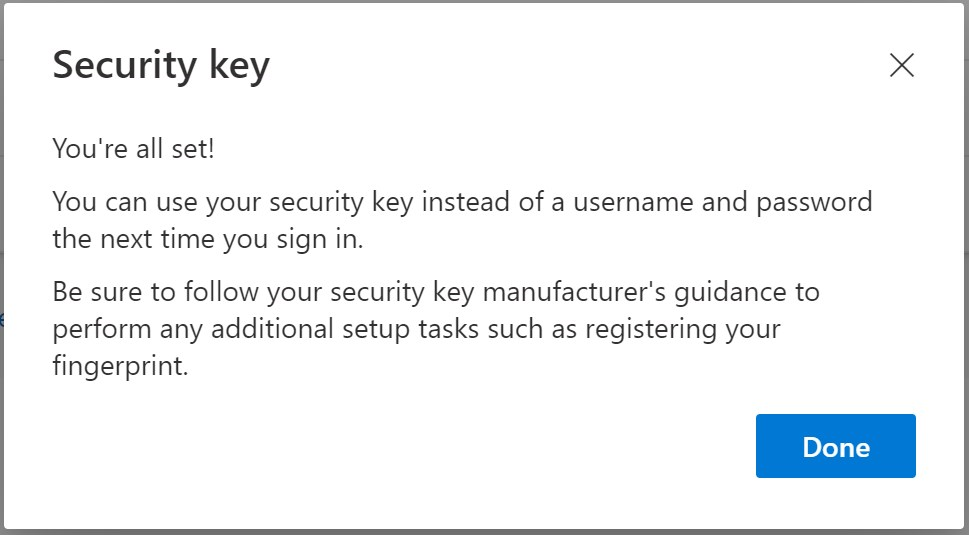
In your Security Info screen, you can now see the Security key is ready!
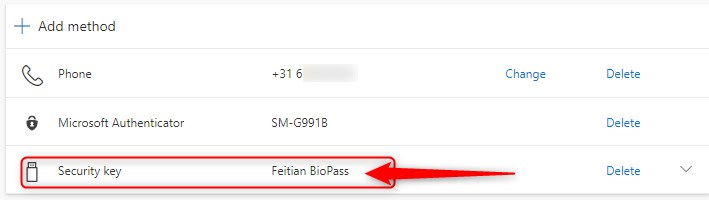
Note: Using Azure AD Security Info you cannot add a fingerprint to your Security Key. This means that you will have to provide a PIN when signing in to Office 365 web apps. You can still manage your security key using the Windows 10 Security key manager to add a fingerprint. In my case, I can also use the FEITIAN Security key manager to add fingerprints.
User experience – Passwordless sign in with Windows 10
Depending on the FIDO2 Security key you have, your experience might be different. I’m using the FEITIAN BioPass FIDO2 Security key with fingerprint support and I don’t have to enter a PIN after inserting my security key. If your key does not support fingerprint, you will have to enter a PIN to sign-in to Windows 10. Here’s is a short video demo logging in to Windows 10 with my security key.
Here’s a direct link to the video: https://youtu.be/PGMNU-GM0x8
User experience – Passwordless sign in with browser
You can sign in to Office365 with your FIDO2 security key using a supported browser.
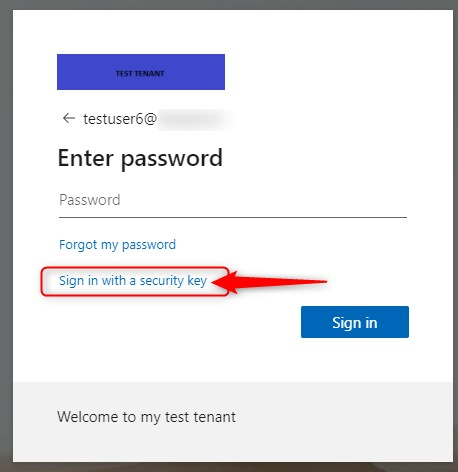
- Go to https://portal.office.com
- Type your username
- Click on Sign in with a security key
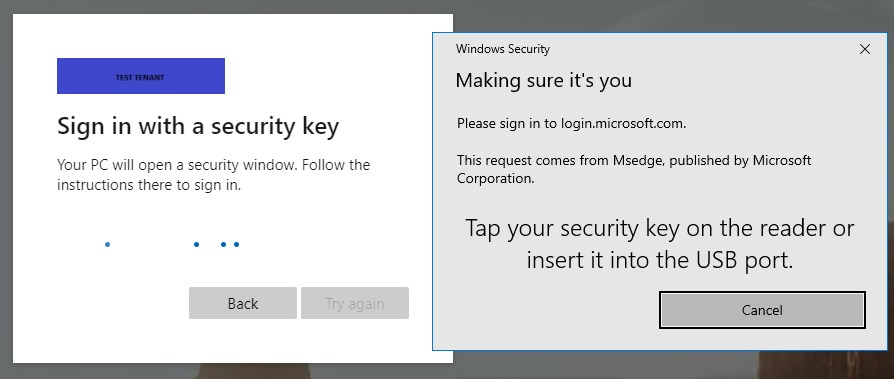
- Insert your security key
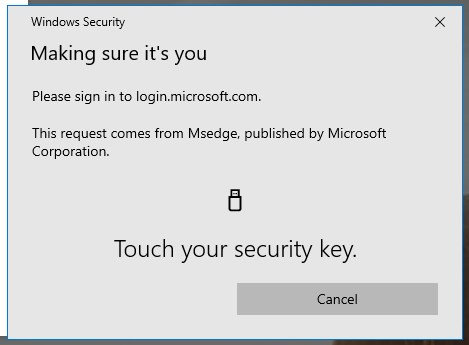
- Type your PIN
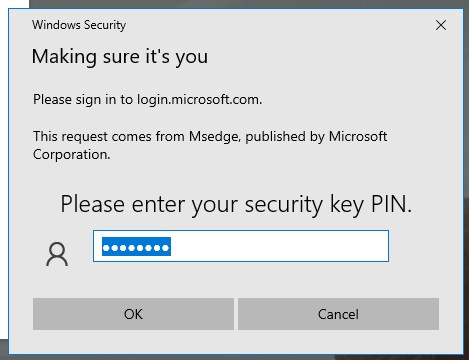
- Touch your security key
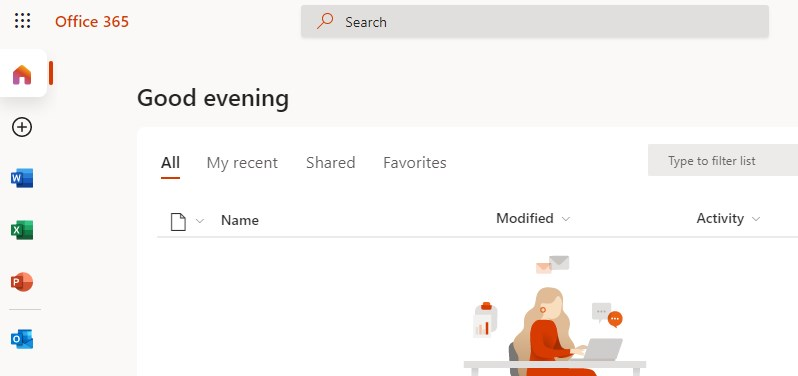
You have signed in without providing a password. Go ahead and read your e-mail 😉
Final thoughts
Windows Hello Face recognition is perhaps the best experience for a device where a user is enrolled and also a great way to go passwordless. FIDO2 security keys are a great option if your device does not support Face recognition. FIDO2 security keys are also a great option when using shared devices where Windows Hello for Business is not the best solution. It also provides your users the option to use their security key to sign-in with other web apps.
Further reading material
- Browser support of FIDO2 passwordless authentication | Microsoft Docs
- Azure Active Directory passwordless sign-in | Microsoft Docs
- Microsoft-compatible security key – Microsoft 365 Security | Microsoft Docs
- Passwordless security key sign-in – Azure Active Directory | Microsoft Docs
- Passwordless security key sign-in Windows – Azure Active Directory | Microsoft Docs
- Integrate Windows Hello for Business with Microsoft Intune – Microsoft Intune | Microsoft Docs
- Known issues and troubleshooting for hybrid FIDO2 security keys – Azure Active Directory | Microsoft Docs
- Plan a passwordless authentication deployment in Azure Active Directory | Microsoft Docs
- Browser support of FIDO2 passwordless authentication | Microsoft Docs
- Resources | FEITIAN (ftsafe.com)

Great article. Didnt know WHFB is not required, Thanks for sharing that. Only thing to solve, how can we lock Windows when we pull out the security key?
You can use Task Scheduler and trigger based on USB unplug event
Is there a way to set password authentification as default option?
When i configure this, it sets every machine it’s assigned, to usb logon.
Users without the key have to switch.
Hi Batu, try assigning a default credential provider using settings catalog. (Administrative Templates\System\Logon\Assign a default credential provider). have a look at the documentation here. And also read my other blog Eliminating Passwords for a list of most used credential providers. You’ll have to set the password credential provider as default.
Also want to mention again: Always use a pilot group when testing new functionalities just to make sure it has the desired outcome.
[…] If passwordless is new to you, you might want to start with another blog first: Passwordless authentication with windows 10 and Azure AD […]
[…] Passwordless authentication with windows 10 and Azure AD […]
Is it possible to authenticate ‘run as administrator’ using a fido2 key?