Last Updated on October 4, 2022 by Oktay Sari
July 2022
IMPORTANT UPDATE: Microsoft announced the sunset for Windows Information Protection! WIP will be discontinued over time. Support for Windows Information Protection Without Enrollment will end by the end of calendar year 2022. Please read the official announcement and more on the following 2 sites:
- Announcing the sunset of Windows Information Protection (WIP)
- Support tip: End of support guidance for Windows Information Protection
If you have plans to implement WIP, I suggest you rethink your strategy accordingly. I will follow-up on this and update the WIP posts I have when more information is released by Microsoft.
Certainly Windows Information Protection (WIP) is a great solution for companies who want to enable a bring-your-own-device solution and at the same time protect corporate data. In a previous blog I wrote about managing BYOD devices with Intune MAM Without Enrollment and how to manage BYOD with Intune MAM without the need to fully enroll devices into MDM. That blog post focused on mobile devices like phones and tablets running iOS or Android. Let’s have a look at the different options we have with WIP and how we can secure corporate data on Windows 10 without restricting users who want to work on their personal devices too much.
In this post I’ll give an introduction to WIP and talk about how to help protect organizations against data loss and leakage.
This post is part of a series and in upcoming posts will be about Microsoft Cloud App Security, Limiting Access to Exchange Online or SharePoint on unmanaged devices. Combining the power of these tools, will give you a great solution to enable a bring-your-own-device scenario. This first post in the series will focus on Windows Information Protection.
- Introduction to Windows Information Protection (this post)
- Configuring MDM user scope and MAM user scope
- WIP without enrollment (WIP-WE / BYOD)
- Windows Information Protection with Enrollment
- Windows Information Protection User Experience
- WIP-WE User Experience – WIP Without MDM enrollment
- Set up Azure Rights Management for WIP
- WIP Without Enrollment Selective Wipe
- Troubleshooting Windows Information Protection
- Monitoring and collecting WIP audit event logs
- WIP Learning mode
- Support Windows 10 BYOD with Microsoft Endpoint Manager and WIP-WE
Data separation & Windows Information Protection
The main idea behind Windows Information Protection (WIP) is to keep work and personal data separate and protect corporate data. As a result, WIP can help reduce the risk of (accidental) data leaks through for example apps and email services like g-mail which are outside of the enterprise’s control. Therefore, WIP needs to know the difference between personal and work related data.
Corporate data
WIP adds a tag to corporate data defined by your corporate identity like contoso.com and network boundaries like contoso.sharepoint.com. Therefore data is automatically encrypted when saved from these corporate sources to your device using Windows Encrypting File System (EFS). In other words, WIP does not encrypt your files on SharePoint or OneDrive. It only encrypts corporate data saved to your device. Using WIP without enrollment (MAM), administrators can identify which apps are allowed to access corporate data and whether users can copy data from those files and then paste that data into personal documents.
Personal data
Performing a selective wipe will not delete personal files and when the user removes his or her workplace account only corporate data is removed. Protected corporate data will be revoked and inaccessible once a device is unenrolled from Azure AD. Administrators can also remotely wipe corporate data from the device while leaving personal data untouched.
Enlightened applications vs Unenlightened applications
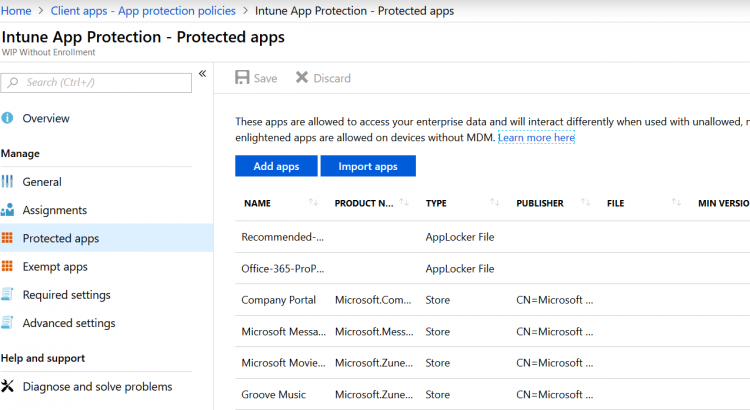
There are two kinds of applications you need to know about; Enlightened applications (MAM aware) and Unenlightened (MAM Unaware) applications. The difference is that enlightened apps can differentiate between corporate and personal data whereas unenlightened apps cannot. Office 365 ProPlus apps like Word, Excel, PowerPoint, OneNote, and Outlook are enlightened apps. Google Chrome, Firefox or Wordpad are examples of unenlightened apps.
If you want unenlightened apps to be able to access corporate data and encrypt files, you will have to add it to the WIP policy as an allowed (managed) application. When you do configure unenlightened apps as corporate-managed they will consider all data to be corporate, encrypting everything created or edited by default so think about this before you add unenlightened apps. Microsoft recommends only adding LOB apps to your allowed apps list.
App Protection Policies with WIP
You can configure two kinds of policies for Windows Information Protection (WIP) to ensure corporate data remains safe or contained in a managed app. WIP with Enrollment in Mobile Device Management (MDM) and WIP Without Enrollment in MDM. Choosing the right solution will help you target the right group of users. WIP with enrollment in MDM is for organizations managing devices using a MDM solution like Microsoft Intune. If you only want to manage the applications and data, you can use the mobile application management (MAM) solution where there is no need to fully MDM enroll devices. A policy can be a rule that is enforced when the user attempts to copy/past corporate data to a unsanctioned application or location.
WIP with Enrollment
When you enroll a device in a mobile device management solution like Microsoft Intune you can manage the device from a central management portal. In most cases MDM enrolled devices will be corporate. These devices are targeted with WIP policies for enrolled devices (WIP With Enrollment) and you will have full control over these devices.
WIP without Enrollment (WIP-WE)
Users find full device management for BYO devices somewhat intrusive and rather prefer a less intrusive method where only the data in applications are managed. Assuming you don’t have automatic MDM enrollment enabled for your tenant, upon adding a work account the device will register in Azure AD and you will be able to manage corporate data without the need to fully manage the device with Microsoft Intune. These users can be targeted with WIP Without Enrollment (WIP-WE).
Windows information protection without enrollment is sometimes referred to as WIP-WE or MAM-WE. Mobile Application Management protects an organization’s data within an application. With MAM without enrollment (MAM-WE), an app that contains corporate data can be managed on corporate devices or personal devices in bring-your-own-device scenarios. MAM only manages the data in applications, where MDM can manage a device.
Prerequisites for WIP
To get you going you’ll need to have the following in place;
- Intune enabled as the MDM authority
- Windows 10 1703 and above (Pro, Enterprise, Education)
- EMS E3 licenses (or at the very least Intune and Azure AD premium P1)
- Configure your MAM provider in Azure AD (for WIP without enrollment)
Good to know
- Windows Home edition supports WIP for MAM-only
- WIP doesn’t support multi-identity. Only one managed identity per device
- WIP protects enterprise data locally and on removable media
- WIP gives admins the ability to revoke corporate data, while leaving personal data alone
Next steps
Read about Configuring MDM user scope and MAM user scope or skip to configuring Windows Information Protection without Enrollment (WIP-WE)
Links:
- Get ready to configure app protection policies for Windows 10
- Protect your enterprise data using Windows Information Protection (WIP)
- Limitations while using Windows Information Protection (WIP)
Great post! In fact, I hired an enterprise mobility management service recently and will share this knowledge with my team as well. Keep up the good work.
Thx Brian, always good to read my post are of added value
Hi Oktay,
First of all, just wanted to say a great job on these posts, they’re really clearly written and easy to follow.
I’m just curious to see when you’ll be finishing off this series?
Thanks,
Alex.
Hi Alex, Thank you! I’ll be starting next week with the rest of the series. I know it’s been a while and feel bad about it. Keep coming back 😉
[…] Introduction to Windows Information Protection […]
[…] Introduction to Windows Information Protection […]
Hey Oktay,
Regarding revoking access to files with work ownership, how does this play out? In my lab scenario, I have a number of files downloaded to a WIP-WE device with ownership set to the tenant. I then set this device in AAD to ‘disabled’ (emulating the scenario of a lost laptop). I expected access to be revoked here, but it’s not. What exactly can be done to revoke access from the admin’s point of view; or is this only when the user removes their work account via Settings?
Thanks!
Hi Ruairidh, Disabling a device does not delete data stored on a device. It only denies authentication and users cant access o365. If you want to delete corporate date you will have to issue a selective wipe from Intune. – Go to Microsoft Intune –>Client apps –>App selective wipe – Create a wipe request by clicking the “+ Create Wipe Request”button on top – Select User and device – Create the wipe request This will revoke access on all WIP protected documents and the user will no longer have access to those documents.The file ownership will show revoked. Hope this… Read more »
Got it 🙂 Thanks so much.
you’re welcome! Have a look at my new post about WIP selective wipe. I think you’ll like it 😉
Hi, thanks for this series of posts – very useful. So being able to manage our data on users personal windows 10 devices is exactly what we want to be able to do. I have set this up in a test environment and it is working well where we add the work account to windows 10 and enrol the device as a registered device. However, if we do not enrol the device the user is simply able to access all our data with no controls. How do we combine this WIP-WE and prevent non enrolled devices from accessing our data?… Read more »
your posts are incredible man, what a gem.
Hi Adam. Thank you! I am humbled by your words. So it’s been a while, but I finally pulled myself together and I’m working on the rest of the series. Keep an eye out.
[…] Introduction to Windows Information Protection […]
[…] Introduction to Windows Information Protection […]