Last Updated on December 29, 2020 by Oktay Sari
In a previous blog I wrote about the basics on Windows Information Protection (WIP). If you did not read that post, I suggest you go back and read it for a complete understanding before continuing. If you’re here to learn more about MDM User scope and MAM user scope, then I hope this post will be of add value for you too.
This post is part of a series and in upcoming post I’ll also write about Microsoft Cloud App Security, Limiting Access to Exchange Online or SharePoint on unmanaged devices, and Azure AD Conditional access policies. Combining the power of these tools, will give you the best possible solution to enable a bring-your-own-device scenario. This post will focus on configuring Intune MDM user scope and MAM user scope.
- Introduction to Windows Information Protection
- Configuring Intune MDM user scope and MAM user scope for Windows 10 (this post)
- WIP without enrollment (WIP-WE / MAM)
- Windows Information Protection with Enrollment
- Windows Information Protection User Experience
- WIP-WE User Experience – WIP Without MDM enrollment
- Set up Azure Rights Management for WIP
- WIP Without Enrollment Selective Wipe
- Troubleshooting Windows Information Protection
- Monitoring and collecting WIP audit event logs
- WIP Learning mode
- Limiting Access to SharePoint Online on unmanaged devices
- Limiting Access to Exchange Online on unmanaged devices
Prerequisites
Make sure you have all the prerequisites in place;
- Intune enabled as the MDM authority
- Windows 10 1703 and above for testing
- EMS E3 licenses (or at the very least Intune and Azure AD premium P1)
Configuring MDM User Scope and MAM User Scope
There seems to be a lot of confusion when it comes to configuring the MDM users scope or MAM user scope and what these scopes do or which one to use. I hope to shed some light on these setting before we actually configure the WIP-WE (MAM) policy in another post. These settings/scopes only apply to Windows 10 devices. Therefore iOS and Android devices are NOT affected.
To configure your MDM and MAM user scope go to:
Microsoft Intune> Device enrollment> Windows enrollment> Automatic Enrollment
Note: if the MAM Discovery URL is missing,or you’re not sure if it’s correct select “Restore default MAM URLs”
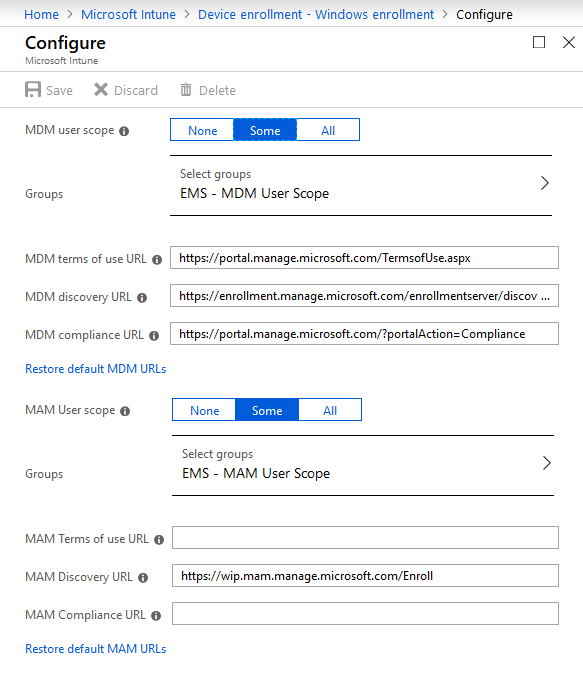
In this example I’ve set both scopes to Some and selected a user group for the purpose of this blog post.
MDM users scope
The MDM user scope is configured to enable Windows 10 automatic enrollment for management with Microsoft Intune. When users in this scope Azure AD join a device or register a work or school account, the device will automatically enroll into MDM management with Microsoft Intune. When you don’t enable automatic MDM enrollment, you still can enroll the corporate device in Intune manually. In other words; The MDM user scope can be used to roll out automatic MDM enrollment with Microsoft Intune to only a select group of users, giving you the option to perform phased roll-outs of the feature.
The screenshot below shows a device that has been Azure AD joined and automatically MDM enrolled while going through the OOB experience. The join type is Azure AD joined and MDM has been set to Microsoft Intune.
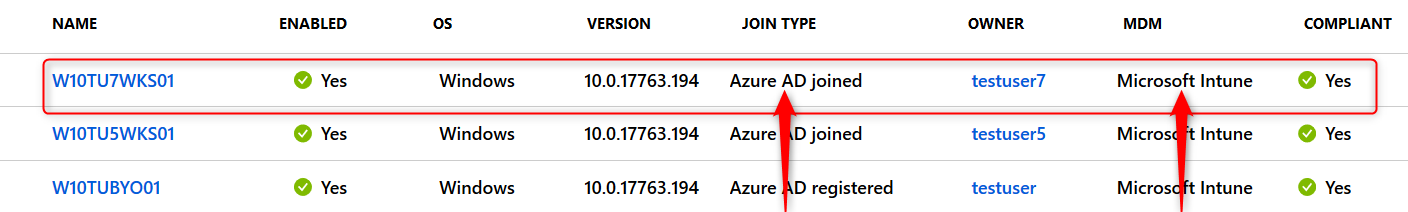
The same thing happens when this user adds a work or school account by going to Windows Setting> Accounts> Access work or school> Connect> Setup a work or school account. The join type will then be Azure AD registered and MDM will again be set to Microsoft Intune.
You can verify MDM policies apply by going to Windows Setting> Accounts> Access work or school> then select your work account and click on the Info button
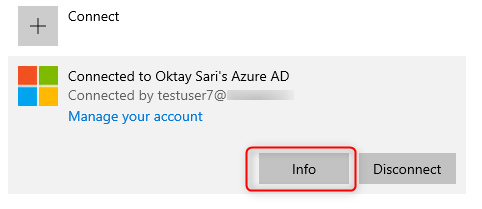
Scroll down to the Connection info part and have a look at the configuration. The Management Server Address should be something like this:

Another way is to use the cmd command dsregcmd /status. The Device State section will show AzureADJoined: YES. There will also be extra information about the device and the tenant.

MAM users scope
When users in this scope add a Work or School Account the device doesn’t get enrolled in Intune but it will be registered in Azure AD. If you have configured Windows Information Protection, only WIP without Enrollment (MAM policy) is applied. However, before creating your WIP-WE policy, you need to set up your MAM provider or the MAM URLs in Azure AD. To enable WIP-WE for Windows 10 devices, the MAM Discovery URL must be configured. Without it the users cannot enroll into MAM management.
The screenshot below shows a device that has been registered in Azure AD but not MDM enrolled in Microsoft Intune. The join type is Azure AD registered and MDM has been set to None. The user registered the device by going to Windows Setting> Accounts> Access work or school> Connect> Setup a work or school account. This device also does not need to be compliant and therefore shows N/A.
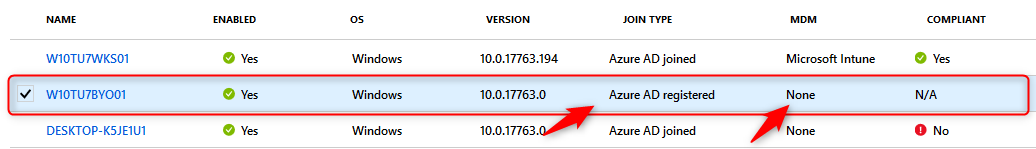
You can verify only MAM policies apply by going to Windows Setting> Accounts> Access work or school> then select your work account and click on the Info button
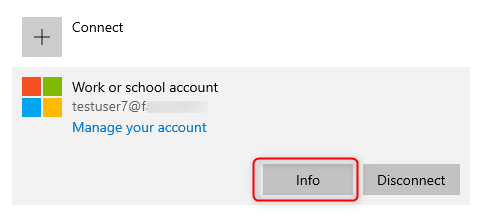
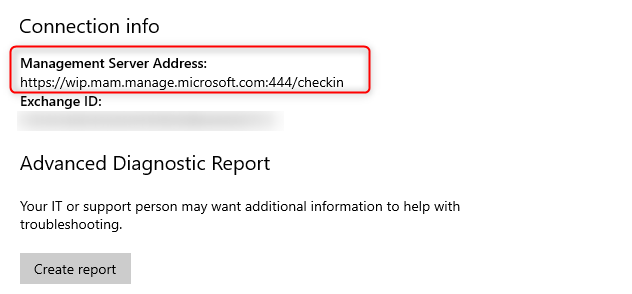
Scroll down to the Connection info part and have a look at the configuration. The Management Server Address should be http://wip.mam.manage.microsoft.com:444/checkin
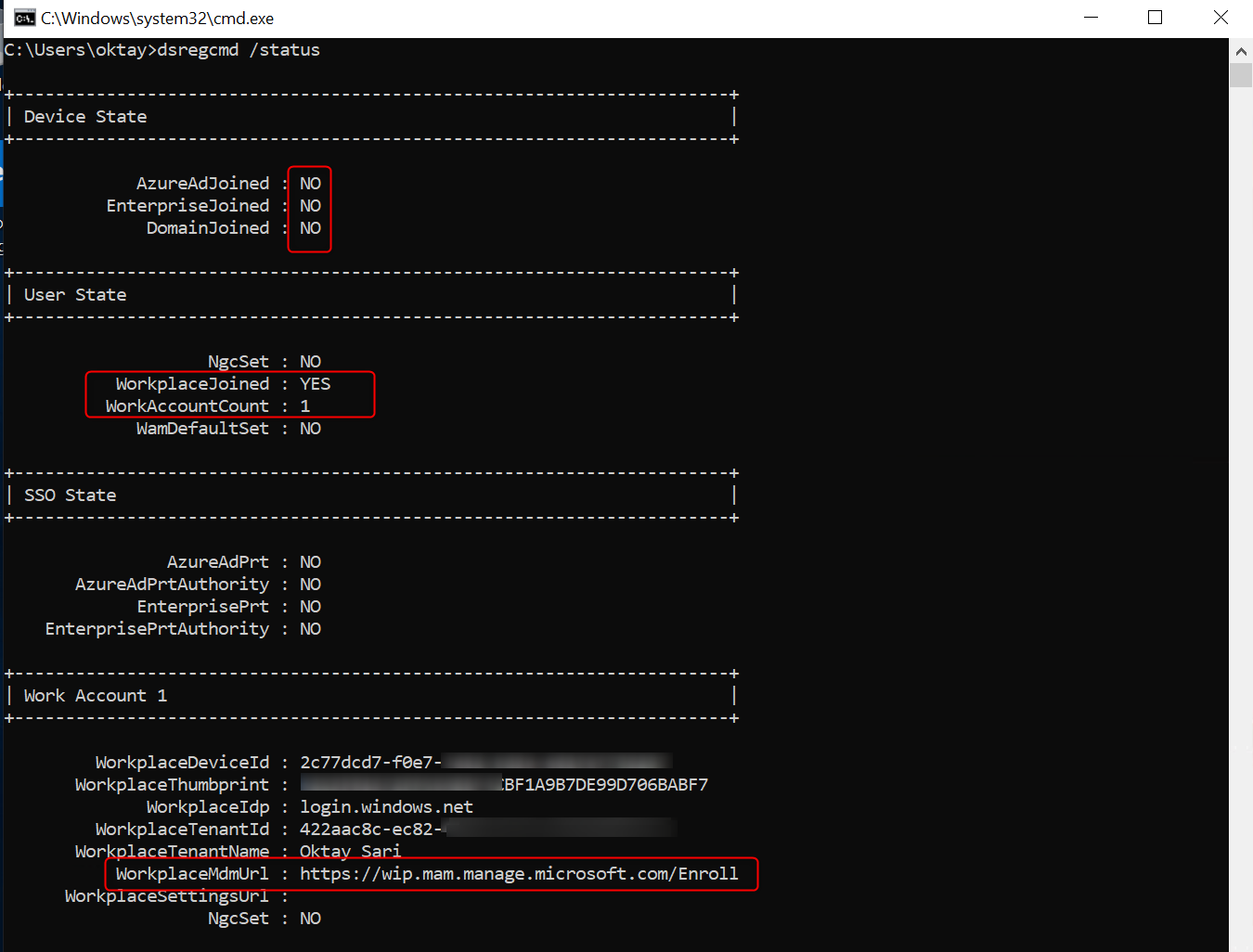
Another way is to use the cmd command dsregcmd /status. The User state shows WorkplaceJoined: YES. Also note the WorkplaceMdmUrl. This is the MAM discovery URL from your MAM user scope settings.
Misconceptions about MDM and MAM user scope
Don’t confuse Azure AD domain join or registration with Intune MDM enrollment. They often go hand in hand but don’t need to. You need to figure out, which user’s you need to automatically enroll to MDM so you can control the devices and apps using MDM and which user’s need to enroll only to MAM so you can control the apps they use, but don’t require the device to enroll to MDM. The latter one is obviously for BYOD scenario’s.
What if you have users with corporate devices that need to be MDM enrolled but at the same time, these users have the need to use personal devices (BYOD) as well, without fully MDM enrolling their BYOD in Microsoft Intune. In other words; you want the same user or group of users to be in both the MDM users scope as well as the MAM user scope.
Here is a quote from the Microsoft website:
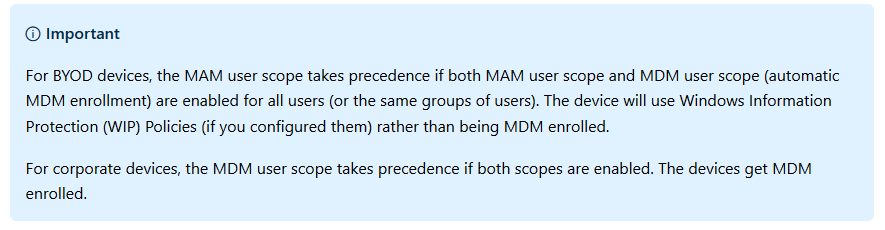
Simply put; You can have the same user or group of users in both the MAM User scope and MDM user scope. If you don’t have a specific use case for it like a phased rollout or a pilot, you can set both these scopes to All Users and be done with it. You will however need to understand the impact of this kind of setup.
Identifying devices as corporate-owned
The real question you should ask yourself is how and when a device is identified as corporate or personal. For a Windows 10 device to be identified as corporate it needs to be;
- Azure AD Joined (OOBE / Windows AutoPilot / User driven)
- Enrolled with a DEP account
- Set as corporate in the device properties (in Intune, after enrollment)
Corporate device
If a user is in both the MAM user scope and MDM user scope and the device is Azure AD Joined it will be identified as corporate and the device will automatically enroll in Intune.
Personal device
If a user is in both the MAM user scope and MDM user scope and the user adds a work or school account, the device will be workplace joined (Azure AD registered) and NOT automatically enrolled in Intune
Reasons to only manage the apps (MAM)
You might have a specific reason to only manage the apps with MAM. Obviously MAM without MDM enrollment is very popular for organizations that support BYOD and here are some of the reasons I come across when implementing Information Security and enabling a bring-your-own-device scenario.
Pilot:
Needless to say but you should start with a contained pilot user group.
Phased rollout:
You want to start with a subset of your users before deploying company wide. This way you can target specific departments or regions.
Compliance
You need to comply with policies that require less management capabilities on BYOD.
User experience
Less intrusive or alarming for users.
Different scenarios worked out
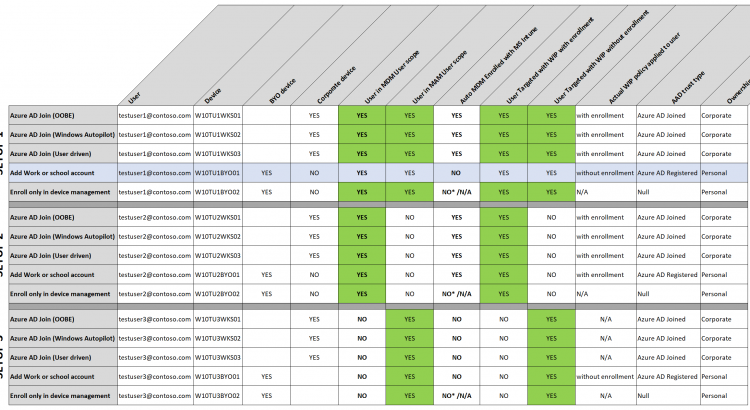
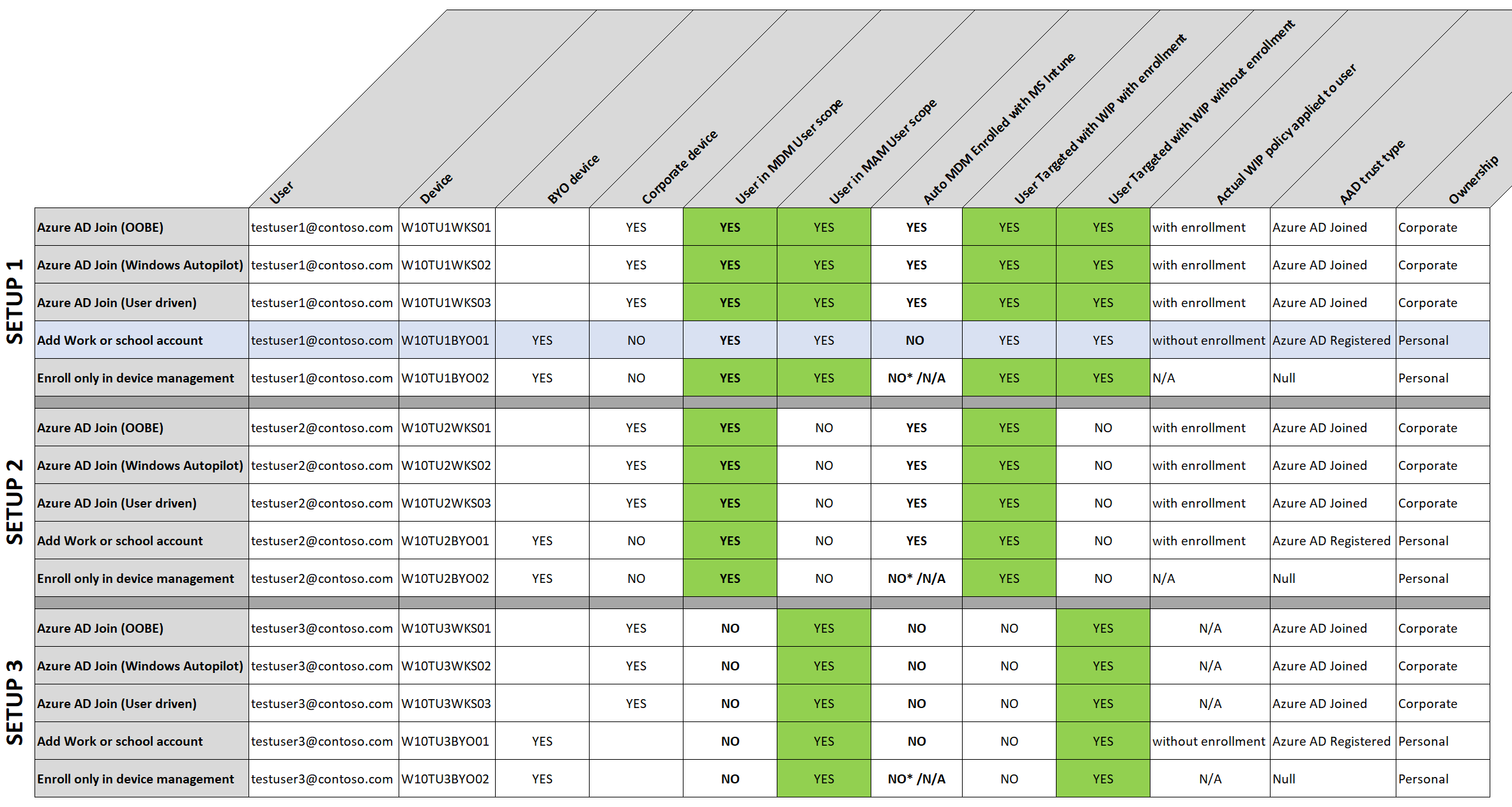
I’ve created a table where I also take Windows Information Protection (WIP) policies into account. There are 3 scenario’s (setups) here but feel free to play with your own scenario’s. I’m thinking SETUP 1 is a good solution in many occasions. You will have full control over corporate devices and users will have the option to add a work or school account on a BYO devices and be managed by MAM (WIP-WE) on their personal devices.
If you or the users need more control on BYOD, then the users can also enroll only in device management. In this case the user will have to enroll twice. First Adding a work or school account will Azure AD register the device, and followed by enrolling only in device management will also MDM enroll with Microsoft Intune.
Click on the image to open the original file
*enroll only in device management will obviously MDM enroll the device in MS Intune so auto enrollment is not applicable here.
Final thoughts
I didn’t think I could come up with this much to write about the MDM user scope and MAM user scope but I had fun writing it and hope it will be of value. If you have any thought you would like to share with me and other readers then please leave a comment below. While I wrote this post to the best of my knowledge I’m still human and make mistakes. If you happen to see an error then please let us know.
Next steps
Go ahead and read about Windows Information Protection without enrollment.
More reading material
- MDM enrollment of Windows-based devices
- Set up enrollment for Windows devices
- Identify devices as corporate-owned
- Configure the MAM provider
Hi,
I just want to pass on my appreciation and thanks for creating these documents.
I have read a lot of guides, step-by-steps and documentation regarding Microsoft InTune.
Your explanation and application on both MDM and MAM is by far the clearest and easiest to follow.
Keep up the great work,
cheers,
FultonZ.
Hi Fulton,
This is all that counts. There a lot of time, research, persistence and commitment involved in trying to keep a blog interesting and of added value. So when someone leaves his or her appreciation like you did, it’s all good. Thank you for your kind words, they mean a lot!
thanks buddy – great explanation on the MDM and MAM scope.
In your screenshot under MAM users scope I see a device that is Azure AD Joined but the MDM is none. This is the scenario I am running into. On these particular devices I selected “this device belongs to my organization” but for some reason they didn’t get enrolled. I’m thinking it’s because at the time, I did not have MDM enabled on the tenant yet. Can you address this third scenario – aad joined but mdm none. How can I get these joined devices to enroll in MDM? By the way, I love the article – it is very… Read more »
Hi Jesse, I see it’s been 10 months since you’ve posted your question. Have you figured this one out yet? You could try to install the company portal app and add your device using the app. Have a look at; https://docs.microsoft.com/en-us/intune-user-help/enroll-windows-10-device for more info.
Sorry for my very… very late response!
Hi,
There is a reason to my test user BYOD download an file from Onedrive Online, and copy and paste information to Twitter with no problem?
Other thing, in this same user and computer (BYOD) i have configured the Onedrive app with the company user. All files have the briefcase icon using Onedrive Desktop.
Download the same file from Onedrive Online doest not have the icon “Company Owner”
Download the same file from Onedrive Desktop Client with company user, the file have the icon “Company Owner”…
Hi Ruben, could you clarify this a little more?
Thank you very much! That’s all what needs to be said.
Hi Patrick,
Thx! Much appreciated
[…] Configuring MDM user scope and MAM user scope […]
[…] Configuring MDM user scope and MAM user scope […]
[…] Configuring Intune MDM User Scope and MAM User Scope for Windows 10https://allthingscloud.blog/configuring-intune-mdm-user-scope-and-mam-user-scope/ […]
Hi Oktay , Thank you very much for such article it was clear about mam and mdm scope. Much appreciated
Always happy to hear 🙂 Thanks for taking time and sharing your thoughts. Much appreciated!
Hi Oktay,
I have a query which i’m hoping you can help me with currently have a my windows 10 computer joined to my personal Azure AD.
I know need to connect to my works data which resides in SharePOint.
When i connect OneDrive to my work SharePoint the files don’t have the application policy applied( i.e. the suitcase and file owner doesn’t display on the files).
Two questions.
Can i register my computer/account with my work, while being joined to personal AzureAD?
How do i enforce all connection to SharePoint/OneDrive have application protect applied?
thanks in advance,
Fulton.
Hi Fulton,
I’ve missed your question. I know for sure your device can be joined and MDM managed in one tenant, and still be Azure AD registered in another (add workplace or school account). You cannot be Azure AD joined in 2 tenants and you cannot be MDM managed in 2 tenants.
However, I did not test this particular situation with WIP without enrollment. It is Interesting though so I might test this and get back to you later.
Did you find a solution yourself? Please share 🙂
This is super good! all that i have been trying to comprehend
However I do have a question, with the setup 1 indicated in the image, its not very clear on what is meant by “Add work or school account” and “Enroll only in device management”—
should this be interpreted as two separate scenarios or 2 steps of the same scenario
Hi Hemant, You can add a work account or choose the link to only enroll in device management from the settings->account->access work or school page. Check out this link for more info. So they are actually 2 different scenarios. Hope this helps.
Thank you very much , very nice article , simple but efficient , easy to understand
Thanks a million for your posts. I have benefited a lot from them (Thanks for all your efforts). One question: I have a user who is a member of both scopes (MDM and MAM). I have created a WIP policy without enrolment. The issue I am having is: The moment I joined my test VM to work or school account (Without joining the device to Azure AD), the device is automatically added to MDM (Which I don’t want this to happen). How can I avoid this? My main objective is to allow users to have the ability to use their… Read more »
Hi Omar, Thanks! This means a lot 🙂 Have a look at the image with different scenarios. Check out Setup2 and Setup2 (Add work or school account) Seems like it behaves like setup2. Are you sure it’s a WIP-WE policy you targeted? Otherwise check enrollment restrictions and block personally owned Windows 10 devices to enroll with Intune. Hope this helps
Only article that even comes close to explaining this topic in a way that makes sense.
Hey, very many thanks for all your very informative blog posts and I’m also very excited to read the coming ones, much appreciated! I was new to these scenarios and now I want to implement this in my company but I’m uncertain which method to use for recognizing company owned and personal owned devices. Currently our company laptops are not all Azure AD joined and we have no local domain anymore and these devices are not configured for autopilot atm but this will change next year. I think it’s the same problem as Omar has, how does Azure/Intune know that… Read more »
Hi Julian, there are a few ways to explore. Devices that are Azure AD registered are marked as Personal by default. You can change the device ownership from within Intune only. So if you want to change this for a Azure AD registered device, the device first needs to enroll with Intune. Once MDM enrolled, you could further segment devices using device categories. I’m not a fan of device categories but the come in handy at times. When devices Azure AD join and MDM enroll with Intune, All Autopilot enrolled devices are marked as corporate. Personally I would advise to… Read more »
We previously had a WIP App protection policy that was targeted for MDM enrollment. As I was one of the targeted users, I did see the management icon appear on my Office apps on my managed laptop. Now we’re testing WIP with MAM-WE for a test user with a VM only AAD registered. The management icon never appears and I can carefreely copy-paste data and save files wherever I want. For that specific app protection policy, its Apps column shows “–” unlike the app counts for Android or iOS app protection policies. Also, its overview page doesn’t show any similar… Read more »
[…] Click OK. Since it’s a blue button, this is where most users will just click without thinking. This will register the user’s device to Azure AD (Azure AD registered device) and possibly enroll to MDM or MAM, depends on what is the current state of this device and the configuration of MDM and MAM. This setting also remembers this user’s credentials on this device for other apps. More details of MDM and MAM scope, read about Oktay Sari’s post Configuring Intune MDM User Scope and MAM User Scope (allthingscloud.blog) […]
Really like your posts Oktay, noticeably clear and they have been of immense help. I don’t suppose you could clear up some confusion I have over the divide between WIP and MAM. I have a windows 10 laptop, WIP managed. That all works great. I want to enrol the device to allow a custom app to be protected. However, when enrolling, we don’t want all the same policies applied as we would do with managed devices. So, we’re trying to assign config and compliance policies using device-based security groups which dynamically assign members based on the device category chosen on… Read more »
[…] Configuring MDM user scope and MAM user scope […]
Thank you for taking the time to write this technical article. Thank you for sharing your knowledge!
You are most welcome 🙂
thank you for all this help, I understood and learned a lot of things but I still have a problem, I am in the case of setup2 device byod with addition of a pro or school account the position is well registered and it is well added in intune but the wip does not work (example no work icon displayed) I also have another case, which is that if I activate MAM, it is impossible to add a byod device in intune because it tells me that it is already part of an organization while it is just in joins… Read more »
[…] your MDM and MAM users scopes. Also check the Intune App Protection policy and the assigned groups. Make sure the user is in the […]
really well explained. Thanks for taking the time for others to learn from you. It is really kind of you.
Thabk you Luis, mich appreciated!
Thanks, man for all the work you’ve put into this series of explanations, you’ve helped some of us understand Intune in a much more detailed way.
Just want to say that this blog post cleared up the week of confusion I’ve had in just 20 minutes, you’re a legend
Now just to figure out how to utilise MAM!