Why is going passwordless such a thing and is it really safer than actually using passwords? When you find yourself asking this question, remember this; When it comes to passwords, human behavior is very predictable. Either a password is secure enough but hard to remember (%J5Uc#vN9s^hLg03P*ySE0Hca4!Ws$), or a password is easy to remember but not secure enough (P@ssWord2021). Guess what comes easy to most users…With that in mind, let’s see how we can get one step closer to eliminating passwords.
Is passwordless authentication safer?
Is passwordless authentication safer than using passwords? A question, I get asked a lot. I guess it all depends on your definition of safe. In my opinion passwordless is harder to crack and less prone to the most common attacks used by bad actors. Hackers can guess the passwords using brute force attacks and even an amateur hacker knows how to perform a dictionary attack these days. (You do use MFA right?) On the other hand there might be a hacker smart enough to find his/her way around your passwordless 😊. Finally, you’ll have to consider lost security keys, phones or hardware tokens, man-in-the-Browser attacks (trojan/malware), sim swapping and spoofing a biometric.
In the end, (like I said before) when it comes to passwords, human behavior is predictable and passwordless authentication, by its nature, eliminates this very problem (mostly). I guess passwordless is safer than passwords. But if you’re thinking that passwordless authentication will solve all your security problems, you’re missing the point.
Eliminating passwords
Eliminating passwords can be achieved in many ways and I’ve written a few other blogs about passwordless authentication. In my previous post I ended with Microsoft’s strategy on passwordless and the 4 steps to password freedom;
- Develop a password replacement offering
- Reduce user-visible password surface area
- Transition into a passwordless deployment
- Eliminate passwords from the identity directory
Although we cannot completely eliminate passwords for the time being, we can help users transitions to a passwordless future. One way to achieve this, is to remove the option to use a username-password combination when singing in to Windows 10 or Windows 11. And that is exactly what I’m going to do in this post.
Your mobile phone as a FIDO2 USB Security key
What options will users have when we remove the username-password option? They can sing in using Windows Hello for Business PIN, fingerprint or facial recognition. However, in this post I’m going to use another kind of FIDO2 security key. I’ve been using FIDO2 security keys from various vendors for a while and thought it’s about time to try out IDmelon and their somewhat different but yet, very innovative solution. You can use any kind of security key you might already have, but why not try out IDmelon yourself?
IDmelon is certified by the FIDO Alliance and also a member of the Microsoft Intelligent Security Association. Their passwordless authentication solutions enables corporate and individual users to use their mobile phone as a FIDO2 USB security key on a PC.
And if you want to try out FIDO2 passwordless solutions without spending money, then you’ll like their free version to start with. More about IDmelon later on in this post, but first let’s setup our lab environment.
Prerequisites
- Azure AD joined Windows 11 or Windows 10 devices
- MDM enrolled with Microsoft Endpoint Manager
- Windows 10/11 Enterprise edition (for configuration using the Settings Catalog)
- FIDO2 Security key
Credential Providers
Credential providers are the primary mechanism for user authentication and they are used to process and validate user credentials during logon or when authentications is required. When a user enters his/her credentials to sign-in or unlock the device, the credentials are obtained by a Credential Provider. When users sign in using a password, the Credential Provider for passwords is used, if using Windows Hello for Business ( for example PIN), the Credential Provider for PIN is used.
Note: Microsoft provides a variety of credential providers as part of Windows. To check all credential providers, open up the registry and browse to the following location:
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers].
Here are some of the interesting credential providers:
| Credential Provider | CLSID |
| Smartcard Reader Selection Provider | {1b283861-754f-4022-ad47-a5eaaa618894} |
| Smartcard WinRT Provider | {1ee7337f-85ac-45e2-a23c-37c753209769} |
| PasswordProvider | {60b78e88-ead8-445c-9cfd-0b87f74ea6cd} |
| PasswordProvider\LogonPasswordReset | {8841d728-1a76-4682-bb6f-a9ea53b4b3ba} |
| FaceCredentialProvider | {8AF662BF-65A0-4D0A-A540-A338A999D36F} |
| Smartcard Credential Provider | {8FD7E19C-3BF7-489B-A72C-846AB3678C96} |
| Smartcard Pin Provider | {94596c7e-3744-41ce-893e-bbf09122f76a} |
| WinBio Credential Provider | {BEC09223-B018-416D-A0AC-523971B639F5} |
| IrisCredentialProvider | {C885AA15-1764-4293-B82A-0586ADD46B35} |
| PINLogonProvider | {cb82ea12-9f71-446d-89e1-8d0924e1256e} |
Reduce user-visible password surface area
If you want to reduce the user-visible password area, the first step to take is to disable the ability for using passwords to sign in. You can do this by removing (disabling) the password credential provider at the Windows logon screen.
Caution!
A word of caution! Disabling credential providers also impact UAC and RunAs authentication dialog boxes as well as the Remote desktop connection app. Basically it comes down to this; Everything that relies on the password credential provider (username-password) can’t be used anymore. Pilot before you deploy to all users!
Pilot eliminating passwords
Please read the passwordless strategy document from Microsoft. You will want to start eliminating passwords with a pilot group of selected users. The idea is to learn about all the scenarios in which users need to enter a username and password. Microsoft talks about the Work persona and advises to avoid starting with work personas from the IT department because IT workers have multiple credentials, run a multitude of scripts and custom applications. Be sure you fully understand the needs of users. Perhaps this option is not suitable for all persona.
Disable the password credential provider
Now that you know what the impact is, let’s go ahead and configure the exclusion of the password credential provider using Microsoft Endpoint Manager and the Settings Catalog. If you are using anything else then Windows 10/11 Enterprise, than you might want to use PowerShell. Here’s the link to ADMX backed policy CSP; ADMX_CredentialProviders/ExcludedCredentialProviders
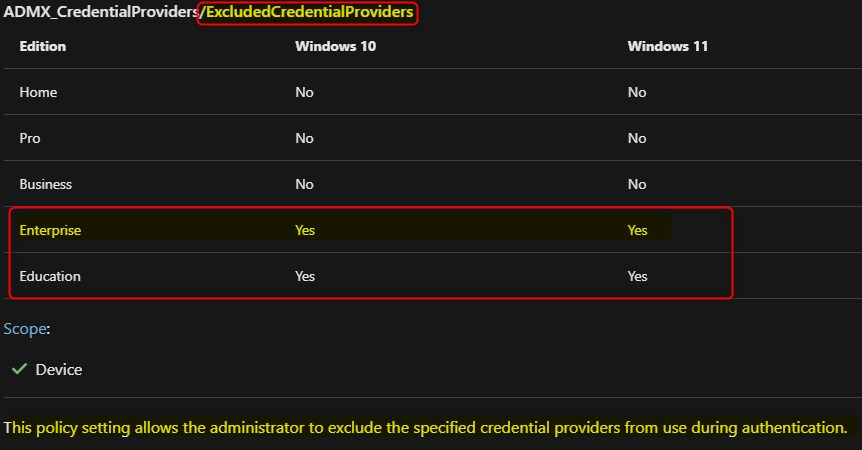
- Browse to your Microsoft Endpoint Manager admin center portal and navigate to Devices > Windows > Configuration profiles
- On the Configuration profiles blade, click Create profile
- Platform: Select Windows 10 and later
- Profile: Select Settings catalog
- Give your policy a name and description and click on Next
- Click Add settings and search for Exclude credential providers
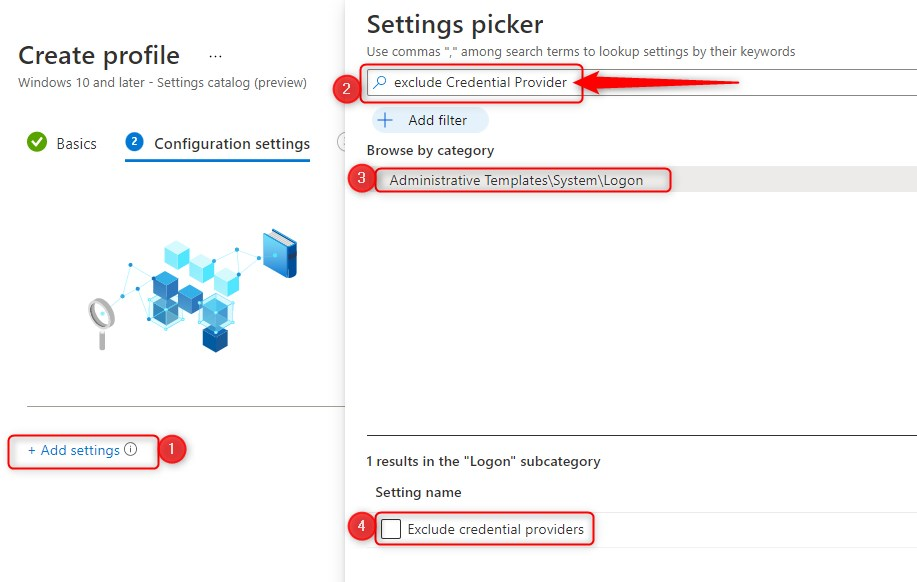
- Click on Administrative Templates\System\Logon
- Select Exclude credential providers as setting
- Switch the slider to Enable
- copy/paste the CLSID for the password credential provider from the table above
- {60b78e88-ead8-445c-9cfd-0b87f74ea6cd}
- click on Next
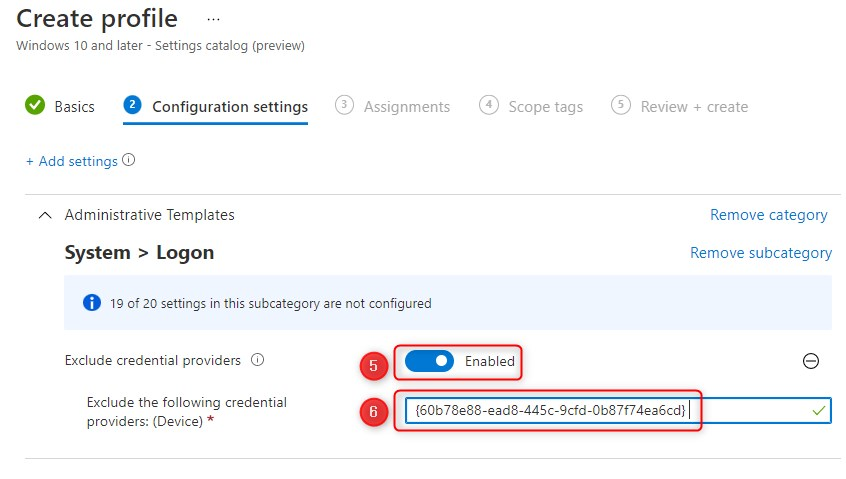
- Finally assign the policy to your PILOT user or device group, click Next and click Create
Note: When you want to disable multiple credential providers separate the CLSIDs with a comma. Also make sure you leave at least one of the system credential provider as a fallback option. For example, do not disable Windows Hello For Business (PIN, Fingerprint, Face). You could find yourself in a situation where users cannot sign in because the lost/forgot their phone or security key and there is no other way to sign in.
End user experience
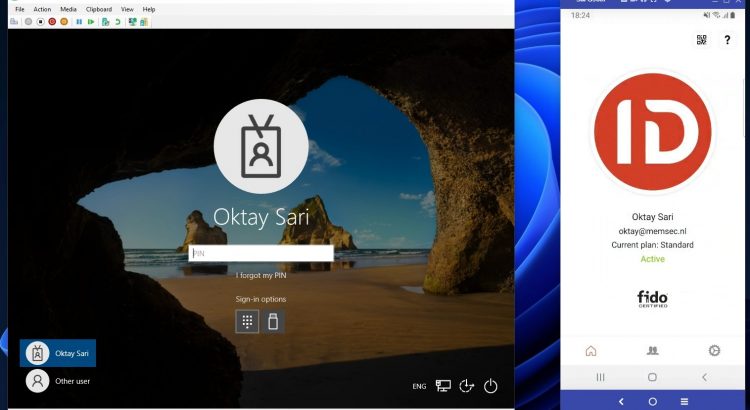
Here’s my Windows 10 login screen where I still have the option to use a username-password combination:
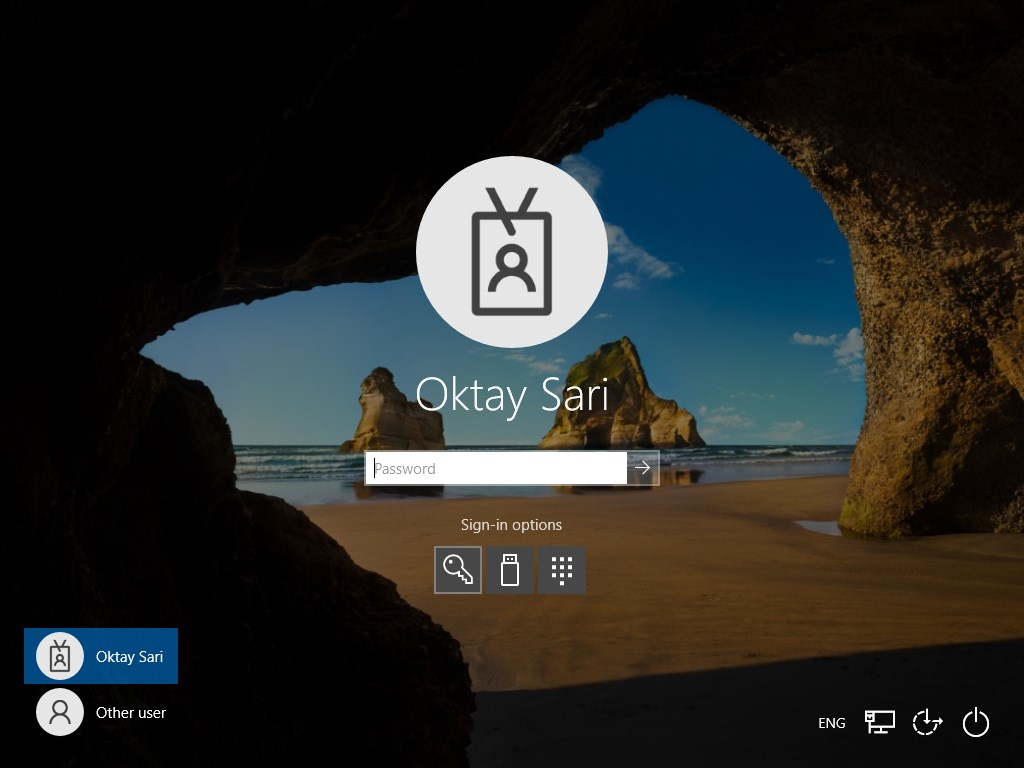
When the policy is applied to the device, the next time the device reboots, the password option is no longer available:
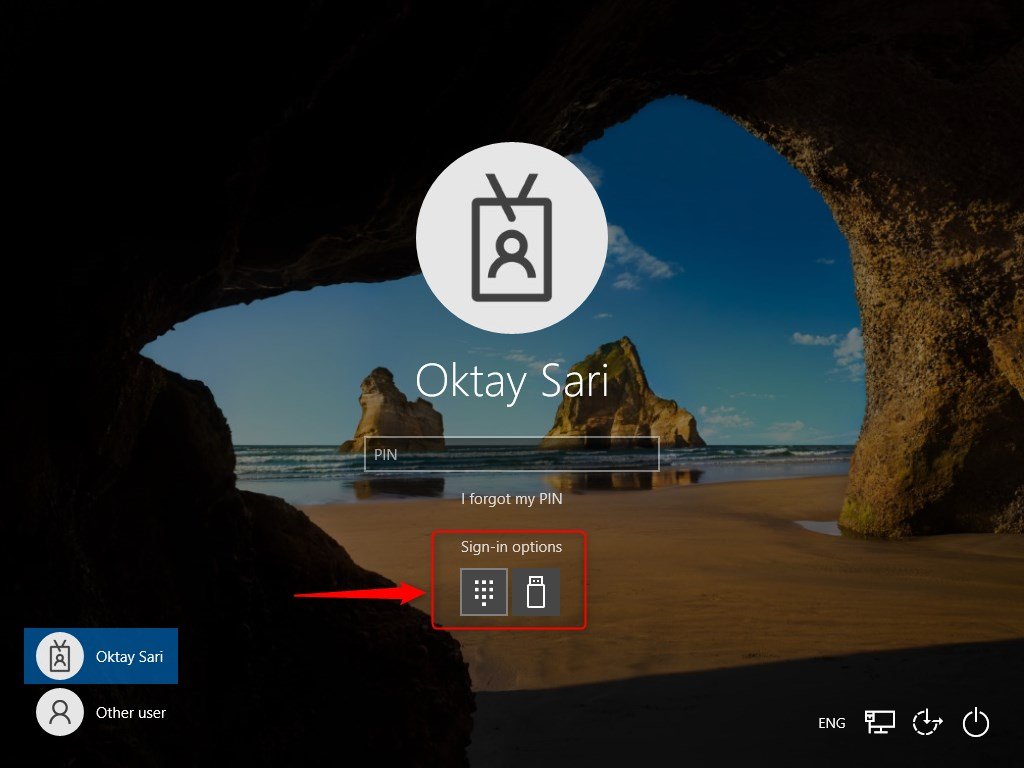
IDmelon
Like I said before, I’ve been using FIDO2 Security keys from various vendors and while researching I came across IDmelons website a few times but something was holding me back. I guess I was used to all my tiny USB FIDO2 security keys and using a mobile phone as a FIDO2 security key seemed odd. Time to prove me wrong 😉
IDmelon supports two use cases;
- Individual Users
- Shared PCs
To start using your smartphone as a security key, you need to either pair your smartphone with your PC (using the IDmelon Pairing tool) or have an IDmelon Reader. Each method of use has its own benefits and your user personas and policies will help determine what to use. Besides the option to pair your smartphone, IDmelon has 2 other options;
- IDmelon Reader
- In combination with the App installed on your phone, you’ll have a seamless experience of Tap & Login. You just tap your smartphone on an IDmelon Reader and it will log you in passwordless. This option is ideal for a shared PC scenario. If you want to have a backup option to login passwordless on a personal device, this might also be an option.
- IDmelon Key
- This is a FIDO2 USB/Bluetooth hardware security key like any other
IDmelon Individual Users
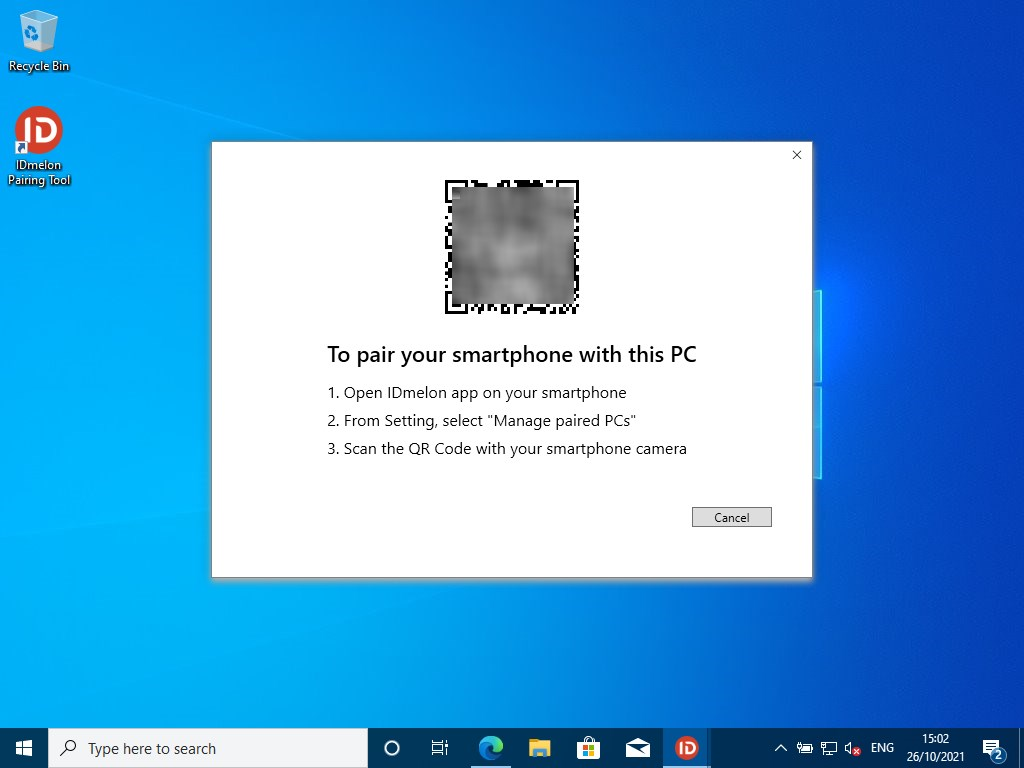
I don’t have the reader for now so I’ll focus on the individual user scenario. Download the App on your mobile phone and the IDmelon Pairing Tool on your Windows device. Next, follow the instructions to activate your security key. I’m not going to explain the full install procedure here because it really speaks for itself. You will need to provide an e-mail account. If the link does not work on your mobile phone, scroll down to the activation code. Then in the IDmelon app, click on Activate with code.
After installing the IDmelon Pairing Tool on your Windows device, you can scan the QR code with your phone to complete the pairing process.
Then give your smartphone a name and click on OK.
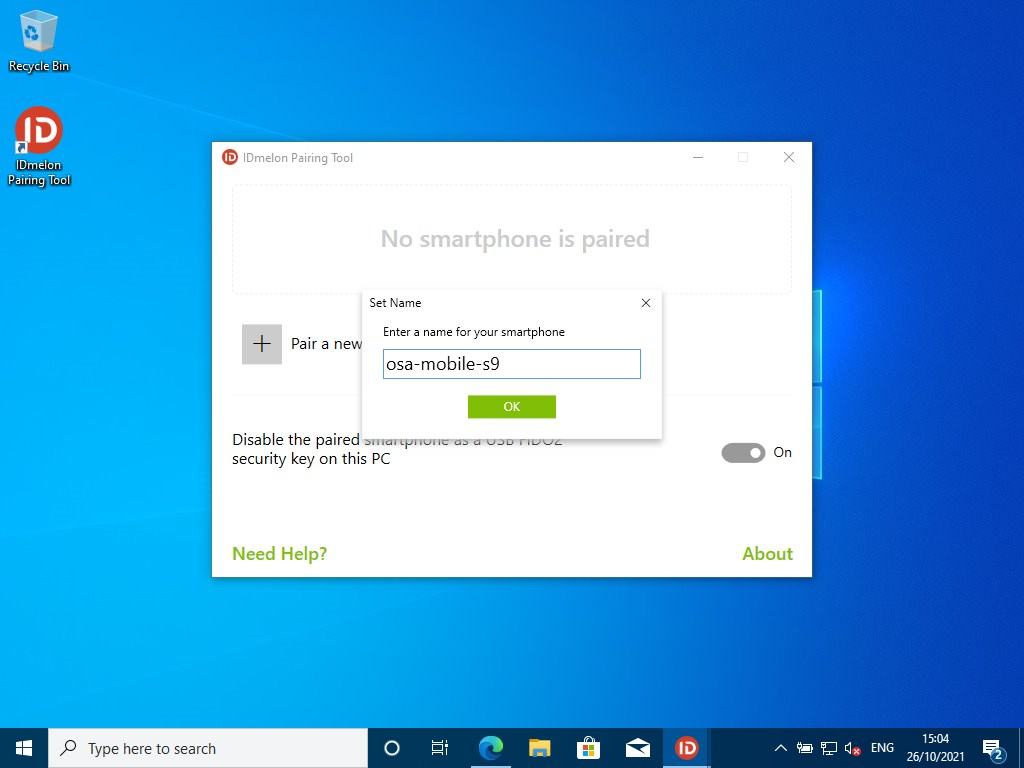
Congratulations! You’ve paired your smartphone and Windows device. IDmelon is almost ready for use!
Adding a Security key
You can go to https://aka.ms/mysecurityinfo to setup your IDmelon security key in Azure. If you’ve never done that before, read my previous blog about passwordless authentication with Windows 10. Although you don’t have a hardware security key, just set it up as a USB security key. The procedure is exactly the same but instead of touching your security key, you’ll approve the sign in using your smartphone app and biometrics.
Demo passwordless sing in using IDmelon
After adding a security key in Azure, you are ready to use your smartphone as a FIDO2 Security key! Let’s see how this actually work. One other thing that is worth mentioning; Normally, you cannot use a virtual machine on Hyper-V with security keys. At least, I still have not found a way to use my USB security keys with Hyper-V. But since we use the IDmelon pairing tool it will work just fine 😊
Good to know
When you install the IDmelon Pairing Tool on Windows, it installs a service that runs in the background and a GUI is available where you can see the paired smartphones and you can pair a new one. The IDmelon App on your phone also works in the background and needs access to your camera (to scan the QR code) and also needs access to enable Bluetooth (when using the reader).
Caveats
When you use the Pairing tool and your smartphone, remember that you will always need an internet connection on both the PC (Sending the notification) and your smartphone (receives the notification and approves authentication). If you don’t have an active internet connection, you can always fall back to your backup authentication method; e.g Windows Hello for Business or a backup hardware security key.
Final thoughts on IDmelon
IDmelon eliminates the burden of carrying an extra physical object, i.e. a security key. Although I was used to have a security key or 2 with me all the time, I’m finding myself using IDmelon more and more. Simply because my phone is one thing I almost never forget. Smartphones have become part of our identities. You will have to find out yourself if this solution fits your needs or not.
Resources:
- Credential Providers in Windows 10 – Win32 apps | Microsoft Docs
- Policy CSP – ADMX_CredentialProviders – Windows Client Management | Microsoft Docs
- Passwordless Strategy – Windows security | Microsoft Docs
Hi Oktay,
Did you compared the IDmelon vs MS Authenticator app Phone Sign-in feature or do you have any thought about the one or the other as they work, for an end user perspective, almost the same.
Regards,
Bas
Hi Bas, Thx for your feedback. I did compare it. I agree, the user experience looks the same, but it is a different type of authentication. First I want to mention that the MS Authenticator Phone Sign-in feature is (sadly) still in preview and not to be used in production. Some say it is only for bootstrap scenarios to setup other authentication methods. It also seams to be restricted to use scenario’s in combination with TAP. There is very little documentation available but have a look at the comments in this MS blog. Read the feedback from user Ravennmsft The… Read more »
[…] Eliminating passwords. Why the hell would anyone want to abolish passwords? Okay, you forget that we humans are pretty predictable animals. We use the same password in several places. And that’s a very dangerous thing to do, so it’s better to have no passwords than to have bad passwords. How? Read it in the article. […]
Hey Oktay,
I have set this of Exclude the password setting but we got a Error 65000. Do you know what is going wrong we got this with a Windows 10 Enterprise workstation.
We got this error in the Event Viewer
MDM ConfigurationManager: Command failure status. Configuration Source ID: (63E8868D-9A2E-4894-848D-2D1D9D354467), Enrollment Name: (MDMDeviceWithAAD), Provider Name: (Policy), Command Type: (Add: from Replace or Add), CSP URI: (./Device/Vendor/MSFT/Policy/Config/ADMX_CredentialProviders/ExcludedCredentialProviders), Result: (The system cannot find the specified file .).
Hi Gerrit. It means it can’t set the policy. First check your policy and make sure there are no spaces before or after {60b78e88-ead8-445c-9cfd-0b87f74ea6cd}.
You can also create the required registry key manually to see if that works just to make sure:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System
Value Name : ExcludedCredentialProviders
Value Type : REG_SZ
Value : {60b78e88-ead8-445c-9cfd-0b87f74ea6cd}
Hallo Oktay,
I have set the password manuelly than it is working. But with te setting catalog in Intune it Does not work.
Hi Gerrit, What version of W10 are you running? Is it 21H1/H2? If not, are you able to test on the latest update? Also check out KB5005101. Comes with 1400+ MDM policies if your not able to update to the latest W10 version. I’m thinking your missing the ADMX files. Please check C:\Windows\PolicyDefinitions and see if you have the CredentialProviders.admx file. If this is a dead end, You can always fall back to using proactive remediations but then I would also open a case with MS just to make sure it’s not some sort of bug or other misconfiguration issue… Read more »
[…] my previous post I showed you how to use the IDmelon Authenticator app and pairing tool on a user assigned Windows […]