Do you still prefer the password madness? While shared windows 10 scenario’s are excellent for passwordless, most users still sign in with their username and password which is old-school these days right? Besides using passwords, most will complain about long lasting logon times, low disk space due to many users and updates that install during work or class time. Well, Let’s see if I can change your view on Shared Windows devices, since many improvements to managing shared devices have been made since the beginning. Let’s continue our passwordless journey in this post by going passwordless on shared Windows devices.
There are a lot of blogs out there about managing and configuring shared Windows 10 devices using Microsoft Endpoint Manager (MEM / Intune). Therefore I will not cover every aspect in detail but instead, focus on going passwordless on shared devices.
In my previous post I showed you how to use the IDmelon Authenticator app and pairing tool on a user assigned Windows 10 device. To start using your smartphone as a security key, you need to either pair your smartphone with your PC or have an IDmelon Reader. In this post I’ll use the IDmelon Reader to show you how going passwordless on shared Windows 10 / 11 devices can make things less complicated.
At the end of this blog, you will have deployed a shared windows device, and signed in with multiple user accounts without a password.
Requirements for passwordless authentication:
- Azure AD Multi-Factor Authentication
- Enable Combined security information registration
- Compatible FIDO2 security keys
- For Azure AD joined devices the best experience is on Windows 10 version 1903 or higher.
- Hybrid Azure AD joined devices must run Windows 10 version 2004 or higher.
- Passwordless authentication methods enabled in Azure AD
- passwordless security key sign in to Windows 10 enabled
Demo setup
- I have enrolled a shared Windows 10 device
- Two test user accounts in Azure AD
- Two test mobile phones (one for each test user)
- Installed the IDmelon app on both phones
- SET a PIN or BIOMETRIC on both phones
- One IDmelon reader
If passwordless is new to you, you might want to start with another blog first: Passwordless authentication with windows 10 and Azure AD
Your mobile phone as a FIDO2 USB Security key
FIDO2 security keys provide strong password-less authentication with an optional PIN or Biometrics that serves as an additional factor. Within Azure active directory, successful authentication using security keys satisfy two-factor authentication.
IDmelon is not a physical security key as most of us know, but rather turns your smartphone into a (somewhat big) security key you’ll probably always have with you.
So to continue you’ll need the IDmelon Reader, and the IDmelon app installed on your phone.

IDmelon Reader
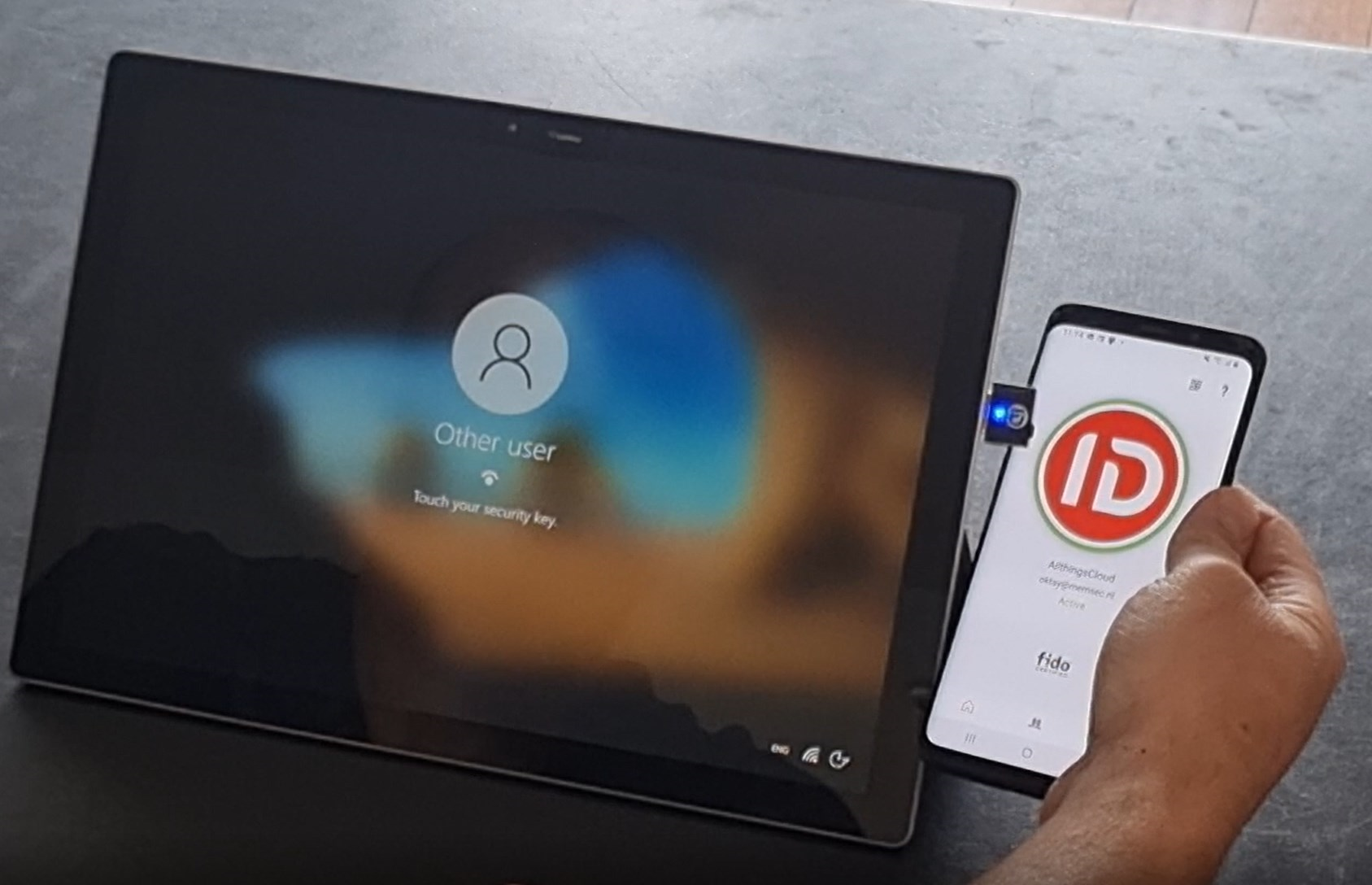
The IDmelon Reader is a USB dongle, Bluetooth Smartphone reader and enables users to use their smartphone as a security key. Users on a shared Windows 10 / 11 device can simply enjoy the passwordless login experience with a single tap with their smartphone on the reader.
The Reader actually supports 3 different working modes each with different capabilities and designed for a specific use case:
- Smartphone BLE Reader
- FIDO2 USB Security Key (like any other FIDO2 security key)
- Paired Smartphone mode (dedicated single user devices)
For now, I’m going to work with the Smartphone BLE reader mode. In this mode the dongle works as a Bluetooth reader and can distinguish the tap of a user’s phone (reading the security key). The only thing you need to do, is install the app, and turn on Bluetooth. And the best thing is… You only need one IDmelon reader on a shared windows 10 / 11 device. It supports an unlimited number of users to use their phones as a security key to sign in to Windows.
Just in case you wonder…No, I do not get paid to review IDmelon. I’m simply exploring the many different vendors, their FIDO2 security key solution, and hope to help others by sharing the knowledge. I’m a curious kind a guy.. 😉
More on IDmelon later. Let’s have a look at how to configure Shared Windows 10 / 11 devices.
Shared Windows 10 / 11 device
A Windows 10 device in shared PC mode is designed to be management- and maintenance-free with high reliability (comes straight from the Microsoft site 😉) . In shared PC mode, only one user can be signed in at a time and when you configure Shared PC mode, it sets pre-defined policies to configure the device. Some of these are configurable using the shared pc mode options with the Windows 10 configuration profile. Microsoft recommends you don’t configure extra settings or keep it at a minimum (for example for Windows Updates). Please read the Microsoft documentation for the configuration steps. I’m also using a Windows Autopilot profile in Self-Deploying (preview) mode for shared devices.
Pre-defined policies for Shared Windows 10 / 11 devices
Like I said before, when you configure Shared PC mode, it sets pre-defined policies to configure the device. Here are some of the interesting ones;
Admin Templates>Windows Components>Biometrics
| Allow the use of biometrics | Disabled |
| Allow users to log on using biometrics | Disabled |
| Allow domain users to log on using biometrics | Disabled |
Admin Templates>Windows Components>Windows Hello for Business
| Use phone sign-in | Disabled |
| Use Windows Hello for Business | Disabled |
| Use biometrics | Disabled |
Why are these interesting? Well, they all have to do with sign-in options. Notice that Windows Hello for Business is disabled by default for Shared Windows 10 / 11 devices. This is because Windows Hello for Business can support a maximum of 10 users on one PC.
Note: I would recommend that you exclude shared devices from any WhB policies you have configured, just to make sure there are no conflicts.
Shared multi-user device configuration profile
I’m configuring Windows to be in shared PC mode using Microsoft Endpoint Manager (Intune). Shared PC mode is enabled by the SharedPC configuration service provider (CSP). To setup a shared device policy for Windows in Intune, go to Devices > Windows > Configuration profiles > Create profile. Select Windows 10 and for the profile Templates > Shared multi-user device.
Here is my Shared multi-user device configuration profile:
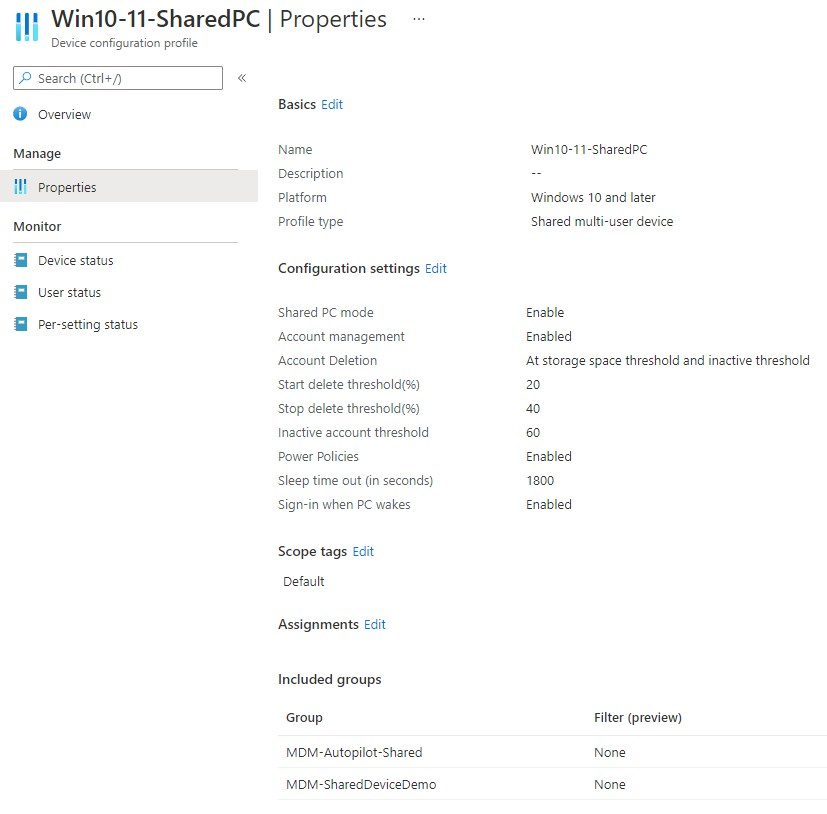
The password credential provider
This is a Proof of Concept! I’m going to disable the password credential provider and only allow Security keys to be used when users sign in. Remember that Windows Hello for Business, phone sign in and biometrics are disabled for shared devices!
Warning: Please keep in mind that after disabling the password credential provider, you will have no other way to sign in to your Windows device, except for FIDO2 Security keys. Do NOT deploy this in a production environment before you pilot and evaluate the desired outcome!
Please read my previous blog if you want to learn more about Credential Providers.
Disable the password credential provider
Now that you know what the impact is, let’s go ahead and configure the exclusion of the password credential provider using Microsoft Endpoint Manager and the Settings Catalog. If you are using anything else then Windows 10/11 Enterprise, than you might want to use PowerShell. Here’s the link to ADMX backed policy CSP; ADMX_CredentialProviders/ExcludedCredentialProviders
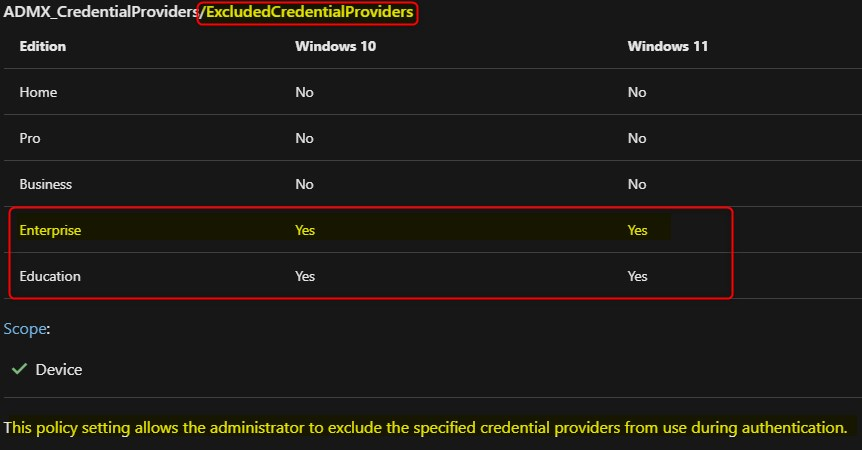
- Browse to your Microsoft Endpoint Manager admin portal and navigate to Devices > Windows > Configuration profiles
- On the Configuration profiles blade, click Create profile
- Platform: Select Windows 10 and later
- Profile: Select Settings catalog
- Give your policy a name and description and click on Next
- Click Add settings and search for Exclude credential providers
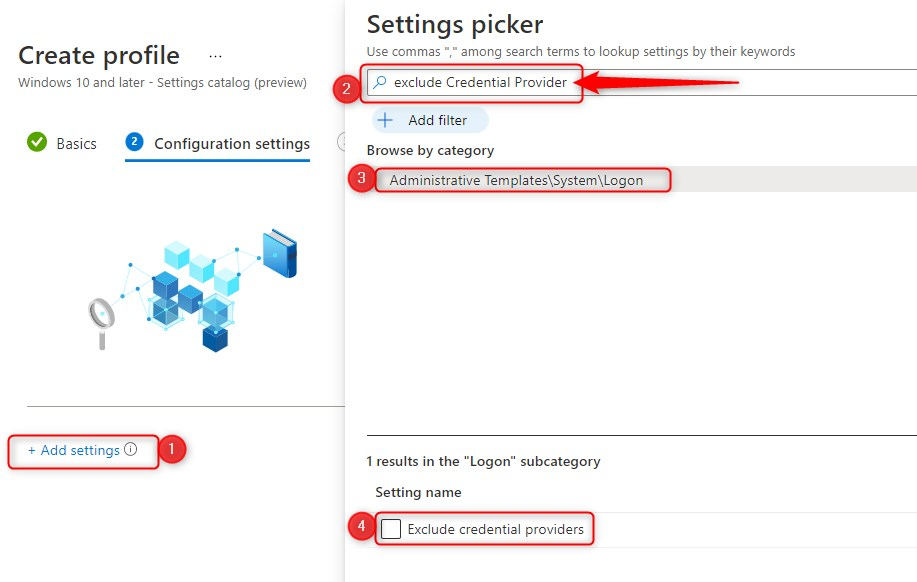
- Click on Administrative Templates\System\Logon
- Select Exclude credential providers as setting
- Switch the slider to Enable
- copy/paste the CLSID for the password credential provider
- {60b78e88-ead8-445c-9cfd-0b87f74ea6cd}
- click on Next
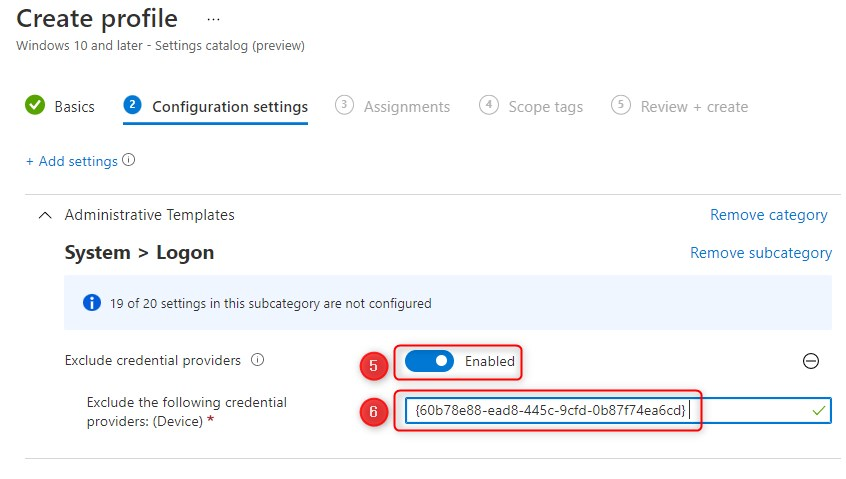
- Finally assign the policy to your PILOT user or device group, click Next and click Create
Recap so far
- configured a Shared multi-user device configuration profile in MEM/Intune
- a Windows Autopilot profile in Self-Deploying (preview) mode
- enrolled a shared Windows 10 device
- checked if policies are applied
- Installed the IDmelon app on my smartphones
- Plugged in the IDmelon reader in my Windows 10 device
Here’s a sneak peak:
IDmelon Admin Panel
Let’s go ahead and configure IDmelon. For the purpose of this demo, I’ve created some users in Azure and manually added them to the IDmelon Admin panel. Please read my previous blog where you can read more about IDmelon for individual users.
Note: Keep in mind that this is a license based and paid service. There is a trial for one month only and it comes with 5 user licenses .
Also note that I did not read the manual and just started my journey. Most of the configuration is very straight forward. If you do have any issues, you’ll have to mail IDmelon support.
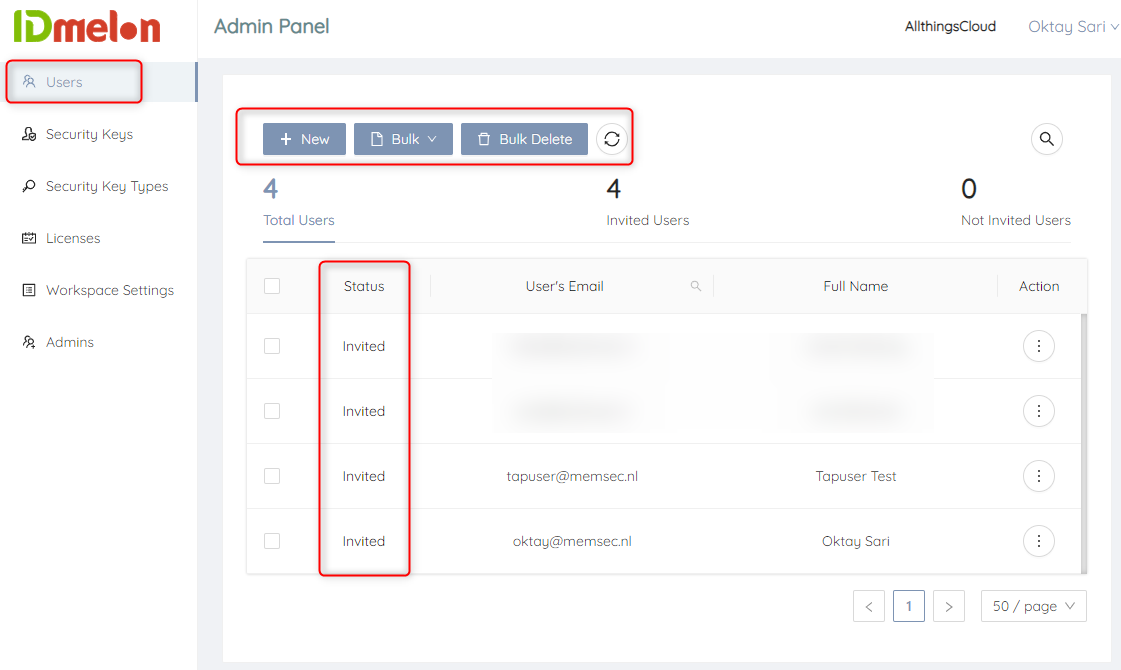
Adding new users to IDmelon
The first thing you want to do is add a new user. Have a look at the VIDEO BELOW for a step by step instruction. I have added and invited two users for my shared Windows 10 login experience;
- tapuser
- oktay
When you add users, they receive an invitation e-mail similar to the one when individual users register for IDmelon. Uplon receiving this e-mail, users can activate their security key on their mobile phones.
Creating and choosing security keys
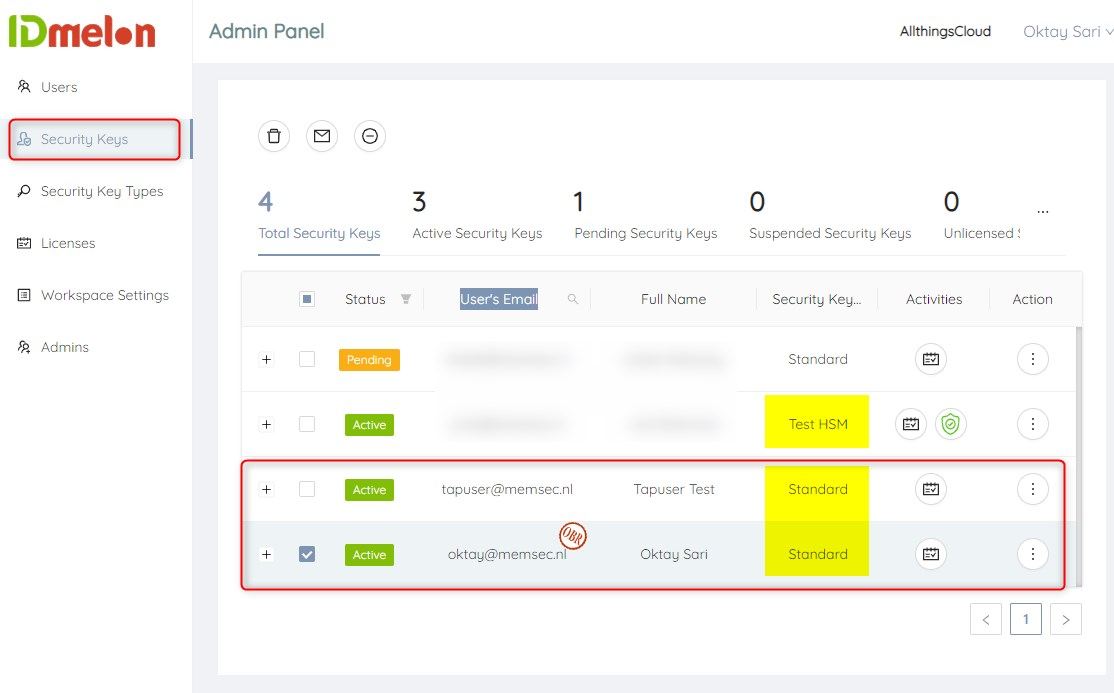
There are two types of Security keys you can create and assign to users:
- Standard – Generates and stores the credentials secret key on the smartphone
- HSM – Generates and stores the credentials secret key on the Cloud HSM services
- Cloud HSM can also be used to recover a previously registered credential when changing smartphones.
You can also choose how user verification should be performed for the security key:
- Biometric authentication using smartphone (default)
- PIN (similar to a standard FIDO2 security key without biometrics)
As you can see in the screenshot below, I’ve assigned both users a standard security key. Have a look at the status column. Both test users have already activated their security keys.
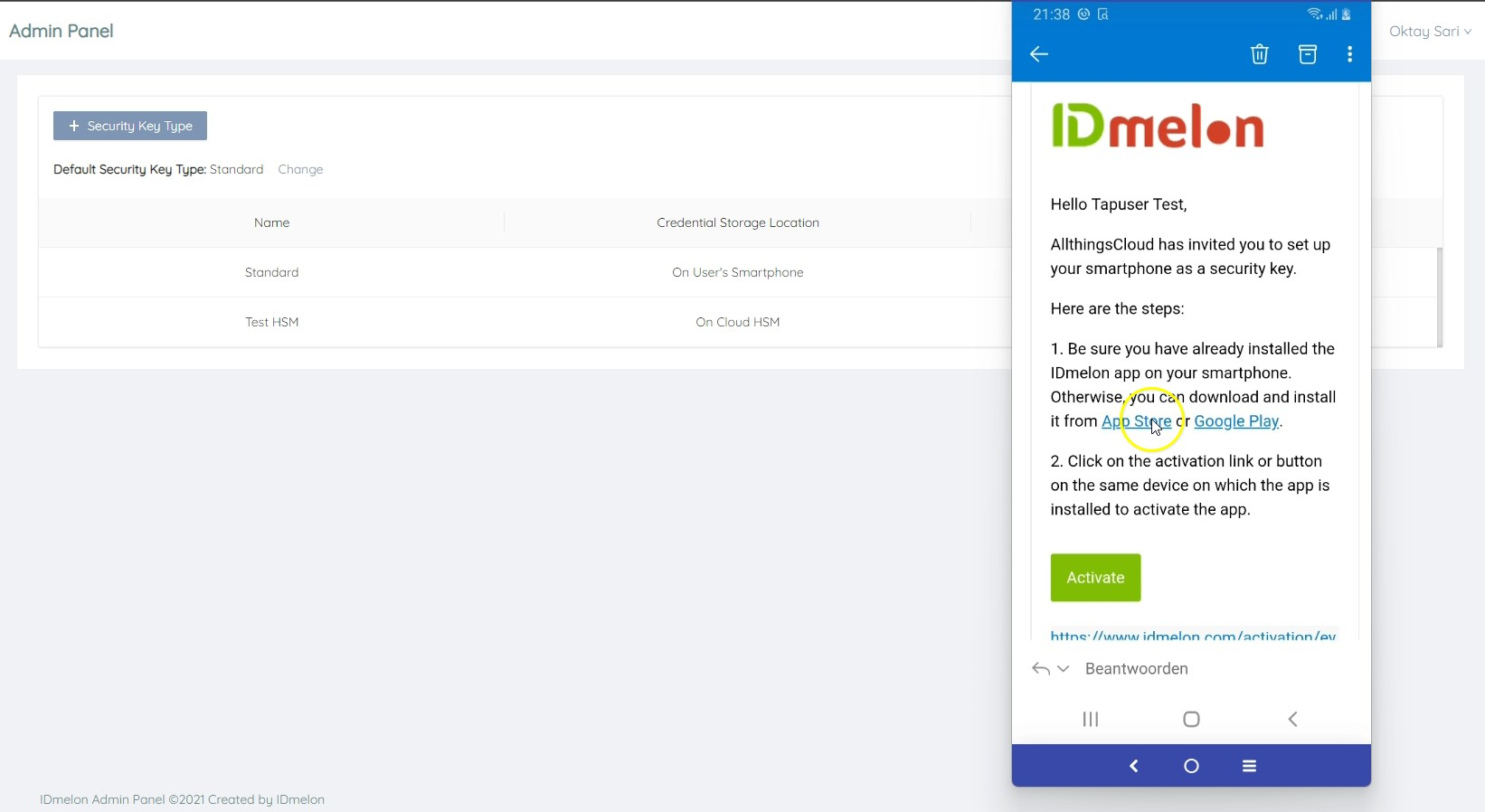
End user experience: Activating the security key on your smartphone
Upon receiving the activation e-mail you can click on Activate link on your smartphone. Make sure you’ve installed the IDmelon app. This will activate the security key.
Configuring a FIDO2 Security key for authentication with Azure AD
go to https://aka.ms/mysecurityinfo to configure your security key in Azure. This is where users can configure the methods they use to sign into their account. Please read Passwordless authentication with windows 10 and Azure AD for more information.
I’m going to assume you know how to add a security key to your Azure AD account.
Note: since we are not using the IDmelon pairing tool you will have to plug in the IDmelon Bluetooth reader to read your security key on your smartphone while adding the key to your Azure account.
Note: IDmelon has a feature called OBR (On behalf registration) that helps administrators to register security key on behalf of the users, so they can just start using the keys immediately. However, when I started this demo the first time, I was not aware of this and also did not know how to configure this.
If you did not configure a PIN or Biometric on your phone, you will not be able to register the security key in Azure AD. Obviously, you do not want anybody to pick-up your phone and have access to your security key without any form of protection.
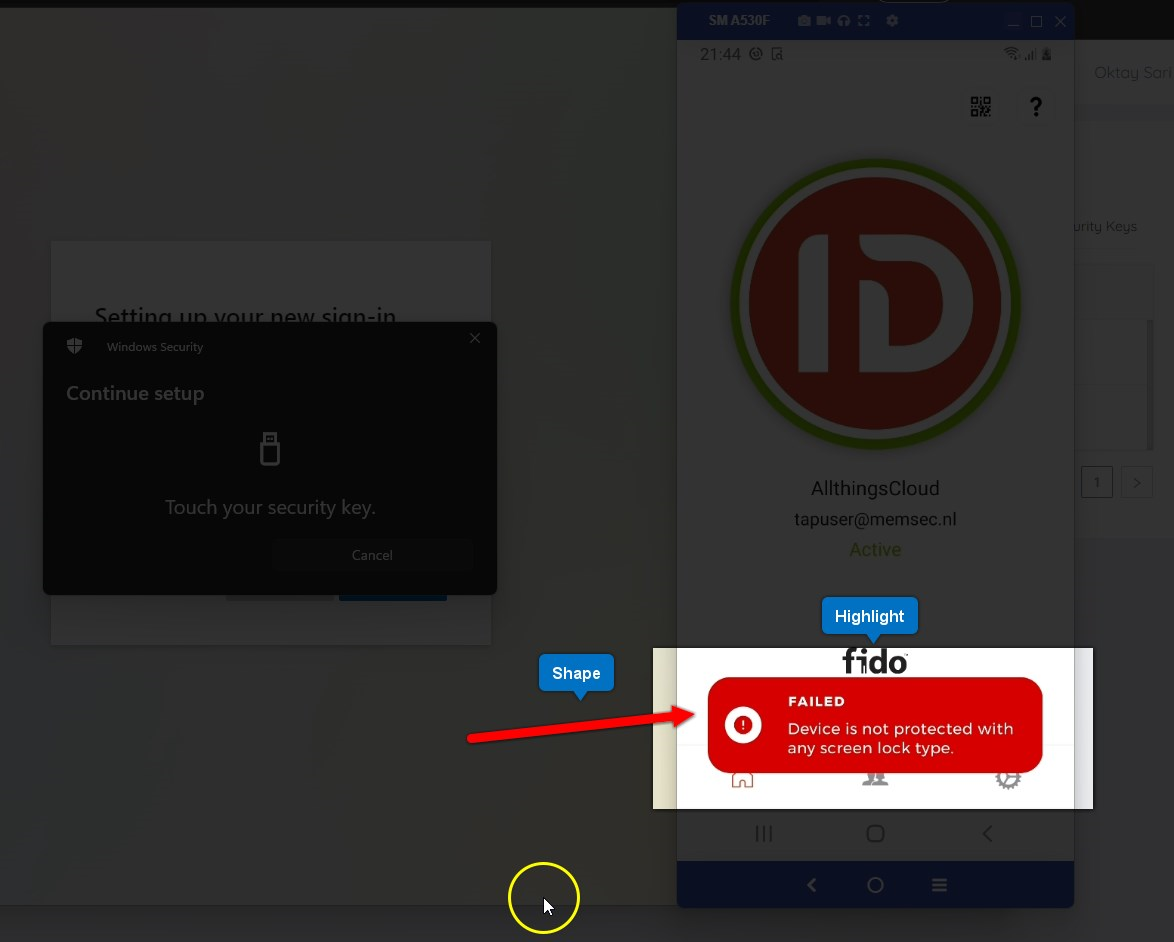
Recap once again…
- Added two users in IDmelon admin portal
- Send invitations to users to activate security keys on smartphones
- Activated security keys on smartphones
- Added security key in Azure AD as a authentication method for both users
Here is the video that shows you step by step, what I did in the IDmelon Admin portal, and how I configured/added the security key for my Azure AD test users.
End user experience on Shared Window 10 device
Finally let’s have a look at the user experience when going passwordless on shared windows 10 / 11 devices. After the device starts up, the user will see a normal login screen but when the users wants to sign in, he/she will only have the option to use a security key. This is where the user can enjoy the unique tap-n-go experience IDmelon has implemented. Just tap your phone on the reader and sign in.
Final thoughts
This was a fun proof of concept but I also believe it’s a very good solution for many scenarios. Yes, you could have done all this with any standard FIDO2 security key like Yubikey or Feitian. The process is almost the same, and it might even be a good backup solution while using IDmelon. However, I think IDmelon has something here that is worth exploring further. And hey, this whole process should also be fun for us techies right? Let me know what you think below.
Next up
What about going passwordless on mobile phones and tablets? In my next post I’ll have a look at some pretty cool Feitian security keys. We’ll explore what it’s like to work on mobile phones and (shared) tablets using the following security keys;
- Feitian Allinpass (Biometrics, Bluetooth, NFC and USB C)
- Feitian iePass K44

- Set up a shared or guest PC with Windows 10/11 – Configure Windows | Microsoft Docs
- Shared or multi-user device settings in Microsoft Intune | Microsoft Docs
- Passwordless authentication with windows 10 and Azure AD (allthingscloud.blog)
- Password Freedom (allthingscloud.blog)
- Eliminating passwords (allthingscloud.blog)
- Smartphone as a FIDO2 Security Key – IDmelon Technologies Inc.
