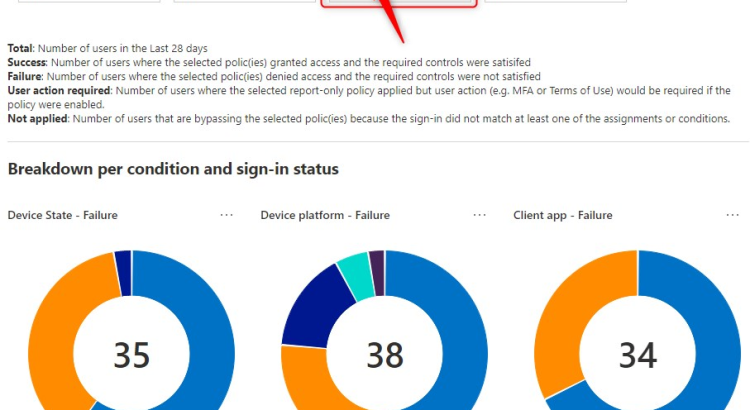
Conditional Access policies in Report-only Mode…Now what? Conditional access policies in Report-only mode allow you to evaluate the impact of Conditional Access policies before you enable them. For instance, you can see conditional access policies in Report-only mode in the Azure AD sign-in logs, but there’s more to it and that’s what this post is […]
Author: Oktay Sari
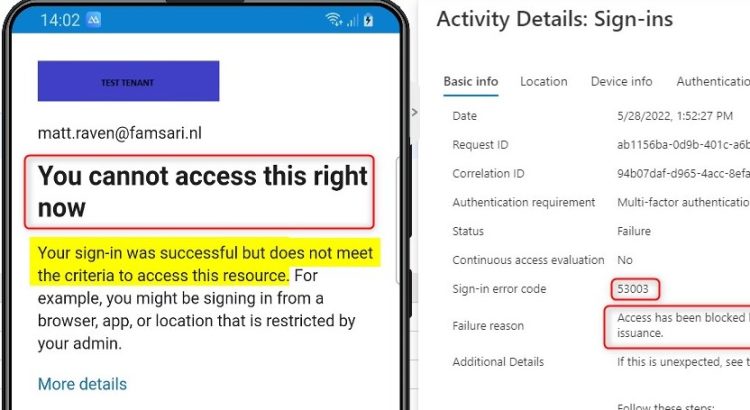
Blocking access to Microsoft 365 outside the Android for Work Profile with Endpoint Manager
This post is about blocking access to Microsoft 365 outside the Android for Work Profile with Endpoint Manager. After seeing a question on techcommunity I thought I might as well do a quick post on this topic. Please note: Normally you would block access to Microsoft 365 resources by using a combination of device compliance […]

What Zombies can teach you about Security Baselines
This month, we had a company event at Rapid Circle and I did a presentation about Security Baselines vs Endpoint Protection templates vs Settings Catalog vs device configuration policies. Yeah… that’s a mouth full. For a change, I didn’t want to do a technical deep dive, but instead, talk more about some best practices and […]
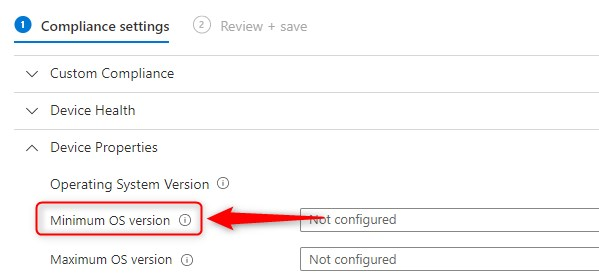
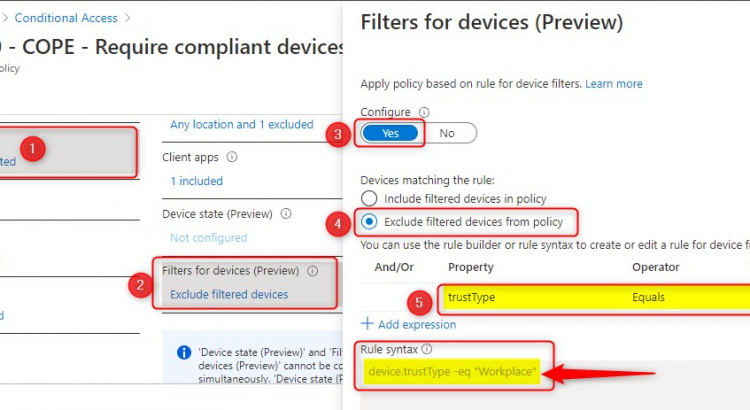
Blocking BYOD based on unsupported OS versions
A couple of days ago, a colleague asked me if it was possible to Block BYOD based on unsupported OS versions from accessing Microsoft 365 resources like Exchange Online or SharePoint Online and Teams, when using the desktop apps on unmanaged devices with older OS versions. In this scenario, BYOD’s are not allowed to MDM […]
Android Enterprise Personally owned devices with a work profile and device PIN
When you configure Android Enterprise Personally owned devices with a work profile in Microsoft Endpoint Manager (Intune) to support BYOD, you probably configured the option for a Work Profile Password like the example below. If you did, and your wondering why some users complain they have to set a device PIN, the device PIN they’ve […]

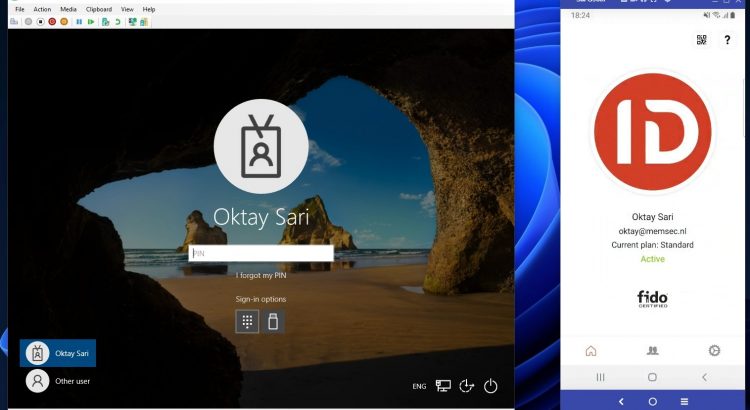
going passwordless on shared Windows devices
Do you still prefer the password madness? While shared windows 10 scenario’s are excellent for passwordless, most users still sign in with their username and password which is old-school these days right? Besides using passwords, most will complain about long lasting logon times, low disk space due to many users and updates that install during […]
Eliminating passwords
Why is going passwordless such a thing and is it really safer than actually using passwords? When you find yourself asking this question, remember this; When it comes to passwords, human behavior is very predictable. Either a password is secure enough but hard to remember (%J5Uc#vN9s^hLg03P*ySE0Hca4!Ws$), or a password is easy to remember but not […]

Password Freedom
What does going passwordless mean to you? Think about that for a minute. It’s a long journey and we can’t get there in a few clicks. I’ve seen a lot of different implementations, but to me, going passwordless means password freedom. It means I no longer need to remember a complex string of letters, numbers, […]
Support Windows 10 BYOD with Microsoft Endpoint Manager and WIP-WE
July 2022 IMPORTANT UPDATE: Microsoft announced the sunset for Windows Information Protection! WIP will be discontinued over time. Support for Windows Information Protection Without Enrollment will end by the end of calendar year 2022. Please read the official announcement and more on the following 2 sites: Announcing the sunset of Windows Information Protection (WIP) […]
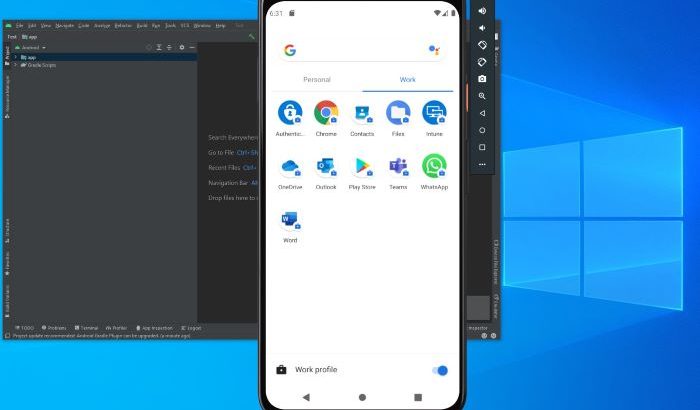
Testing virtual Android Devices with Microsoft Endpoint Manager
When you’re testing Microsoft Endpoint manager, chances are, you’re using a virtual Windows 10 device to do most of your testing. For Windows 10, there are many virtualization platforms like Hyper-V, VMWare or Virtual Box. But when it comes to Android, it’s a different ballgame. There are emulators out there, but I find that most […]