In this topic we’ll be setting up Windows 10 1709 devices to Azure AD join and automatically MDM enroll to Microsoft Intune. I want to share my own experience migrating from Microsoft Intune Enrolled devices using the PC Client Software (Agent) to re-enrolling these devices using the MDM channel.
Current situation
- On-premise AD
- Devices are domain joined.
- Devices are managed by Microsoft Intune as computers using the PC Client Software
- Group Policies are deployed
- ADFS deployed (Federated)
New Situation
- On-premise AD
- Devices are domain joined.
- Devices are retired/removed from the old Intune portal
- Devices are automatically Azure AD joined
- Devices are automatically MDM enrolled and managed by Intune using the MDM channel (as mobile devices)
- Group Policies are deployed
- ADFS deployed (Federated)
Prerequisites
- Active Directory joined devices running Windows 10, version 1709
- Functional MDM Service
- Active Directory integrated with Azure AD
- Devices are Azure AD registered
Step 1: Azure AD Join
One of the requirements to make this all work, is that devices are Azure AD joined. We have an on-premises Active Directory environment and want to join our domain-joined devices to Azure AD. This can be accomplished by configuring Hybrid Azure AD joined devices. Microsoft already has a written an article about this so I won’t go into details. Read the documentation and make sure your devices register with Azure AD.
Verify joined devices:
You can check successful joined devices using dsregcmd.exe. On the test device run dsregcmd /status from the command line.
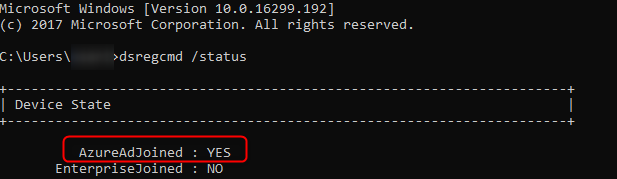
The AzureAdJoined value should be YES. Further below you will also see that the value for DomainJoined is YES.
AzureAdJoined : YES EnterpriseJoined : NO -------------//------------- DomainJoined : YES DomainName : yourdomainname
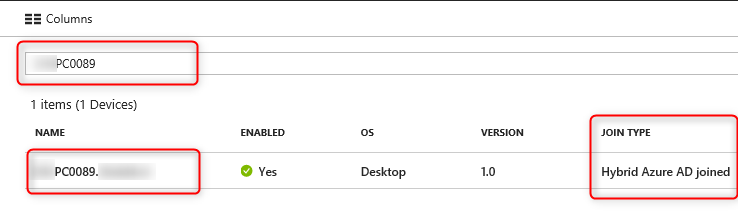
This means the device is Hybrid Azure AD Joined. You can also verify this in the Azure portal;
Navigate to >Azure>Azure Active Directory>Devices>All devices. Search for your device name
Good to know before you continue
Remember that in this scenario the devices are managed by Microsoft Intune and enrolled using the Intune Client Software. While registering the devices with Azure AD will work, before continuing, you will have to manually retire/remove the devices from the old Intune portal before moving on to the next step. The removal process can take a long time (even up to 12 hours) so be patient. If you do continue like I did, the devices will not automatically MDM enroll until the retire/remove task completes.
See the task scheduler as described here. The Last Run Result will show the error code 0x80180026 “Mobile Device Management (MDM) was blocked, possibly by Group Policy or the SetManagedExternally function.” The SetManagedExternally Indicates to the MDM agent that the device is managed externally (old Intune Portal) and is not to be registered with an MDM service.
Step 2: Prepare for automatic MDM enrollment
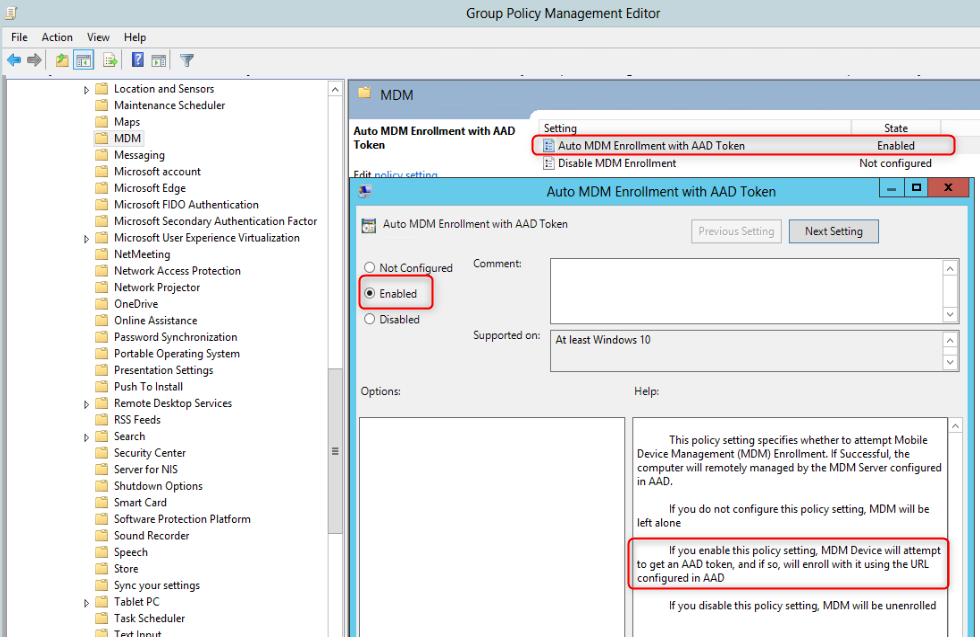
Have a look at the prerequisites above and when all requirements are met continue on. With Windows 10 1709 you can use a Group Policy to trigger auto MDM enrollment for Active Directory (AD) domain joined devices. When the auto-enrollment Group Policy is enabled, a scheduled task is created that initiates the auto-MDM enrollment. You can test this with a single device using local policies but I recommend you continue with the Group Policy Object in your AD.
- You can find the GPO at: Computer Configuration>Policies>Administrative Templates>Windows Components>MDM;
- Open the Auto MDM Enrollment with AAD Token setting, select Enabled and click OK;
- Don’t forget to link the GPO to the correct OU and set the Security Filtering to a security group with devices you want to auto-MDM enroll.
Note:
If you do not see the policy you’ll most likely don’t have the ADMX installed for Windows 10 1709. I’m assuming you know how to install them so go ahead and do so. You can find the ADMX here.
When your device is retired/removed from the old Intune portal, the scheduled task will complete and your device will automatically MDM enroll.
Verify auto MDM enrollment
There are a few locations where you can verify a successful automatically MDM enrollment.
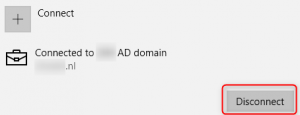
1. The first place to look for is Settings>Accounts>Access work or school.
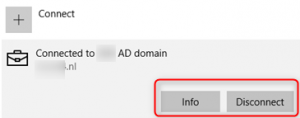
When a device is Domain joined it will show the device is connected to your AD domain and only the Disconnect button;
When a device is Azure AD joined it will show the device is connected to your Azure AD and the Info & Disconnect buttons;
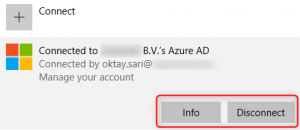
Hybrid Azure AD joined, registered with Azure AD and auto MDM-enrolled will show the device is connected to your AD domain and the Info & Disconnect buttons;
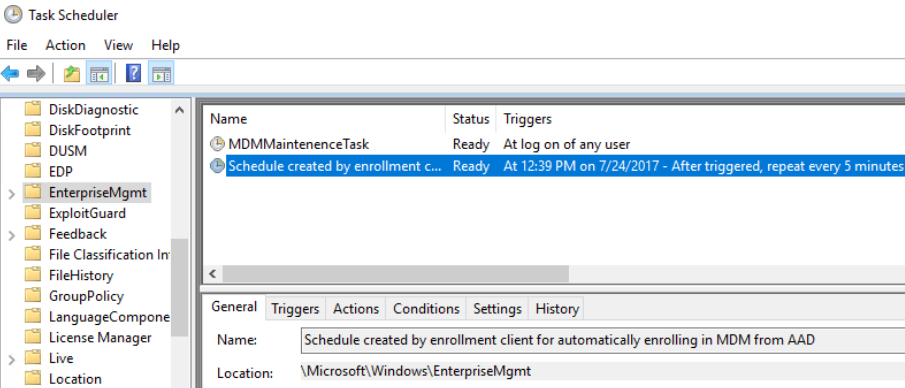
2. The second one is the Task Scheduler. Check the location for device management tasks at \Microsoft\ Windows\EnterpriseMgmt. The schedule created by the GPO should be deleted after a successful auto-MDM enrollment and a folder with a GUID should be there.
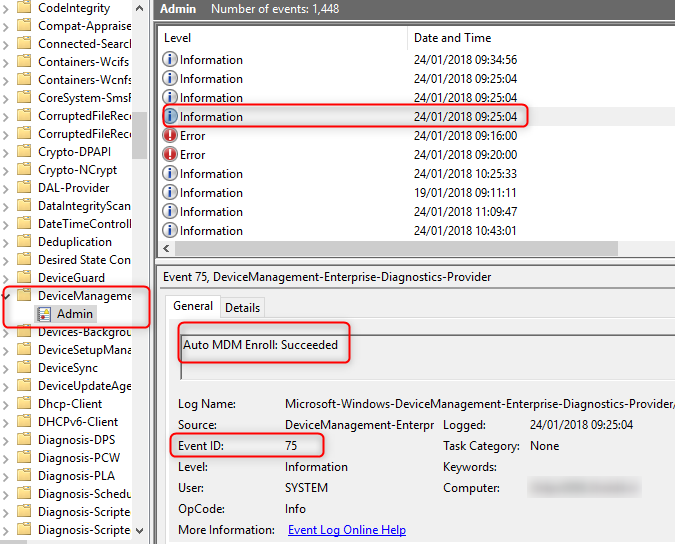
3. The Eventlog should show an Event ID:75 Auto MDM Enroll: Succeeded. Look for the event at Applications and Services Logs/Microsoft/Windows/DeviceManagement-Enterprise-Diagnostics-Provider/Admin
Buggs and inconsistencies auto MDM enrolled devices
Although everything looks just fine, Diving a little deeper it looks a little buggy and shows some inconsistencies.
- Navigate to Azure Portal>Intune>Devices>All Devices and look for your auto MDM enrolled device
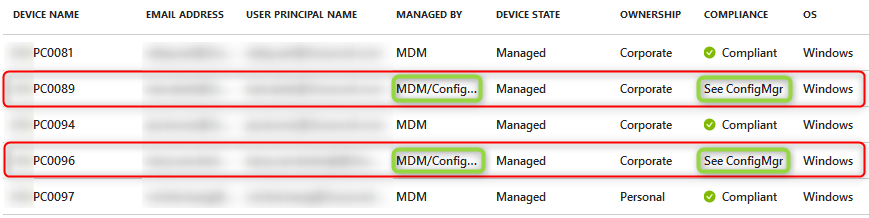
The Manage By will show MDM/ConfigMgr and the Compliance will show See ConfigMgr
- Navigate to Azure Portal>Azure Active Directory>Devices>All Devices
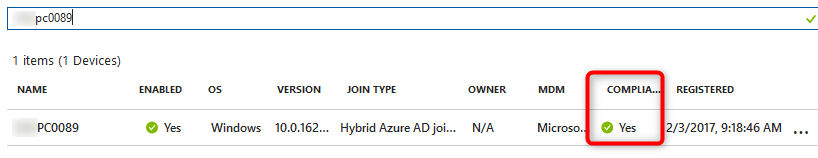
Here the Compliance will show Yes, stating the device is compliant.
- Open your old Intune portal at https://manage .microsoft.com and navigate to Groups>Devices and search for the device once more:
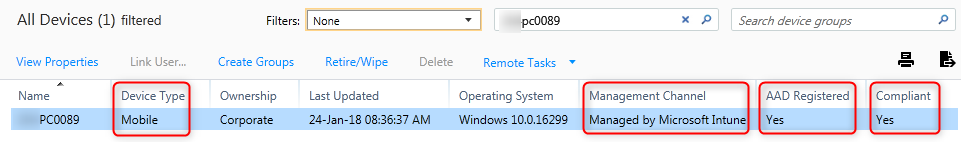
It will show the device is managed by Intune as a Mobile device, is Azure AD registered and compliant.
- Using Powershell and the Get-MsolDevice cmdlet:
# OS Version Numbers:
# 1709 = 10.0.16299
# 1703 = 10.0.15063
# 1607 = 10.0.14393
# 1511 = 10.0.10586
import-module MSOnline
connect-msolservice
Get-MsolDevice -all -ReturnRegisteredOwners | Where-Object { $_.DeviceOsVersion -like "*16299*"} | Format-Table DisplayName, DeviceTrustType, DeviceTrustLevel, DeviceOsType, DeviceOsVersion, DeviceID, RegisteredOwners, ApproximateLastLogonTimestamp -AutoSizeThe filter your looking for is DeviceTrustType and DeviceTrustLevel.
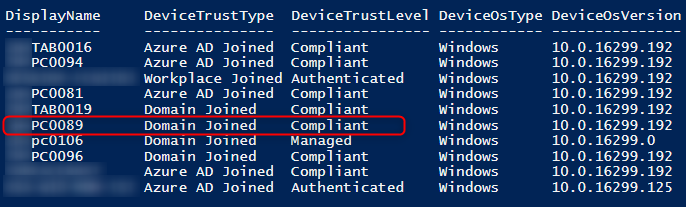
MDM DeviceTrustType:
- Domain joined devices have a value of Domain Joined
- Azure AD joined devices have a value of Azure AD Joined
MDM DeviceTrustLevel:
- Authenticated devices are Workplace Joined devices that are not enrolled in MDM.
- Managed devices are registered devices that are enrolled with MDM
- Compliant devices are registered devices that are not only enrolled with MDM but also compliant with the MDM policies .
It will show the device is Domain Joined and Compliant. Nothing more.
- Intune Graph API and PowerShell
I’ve downloaded the Powershell Intune sample scripts from GitHub to manage Intune using Graph API. There are many useful scripts here and one of them is the Check_lastSyncDateTime.ps1 script. I won’t go into details about using Intune Graph API. Peter van der Woude @ More than just ConfigMgr has a great blog about this topic.
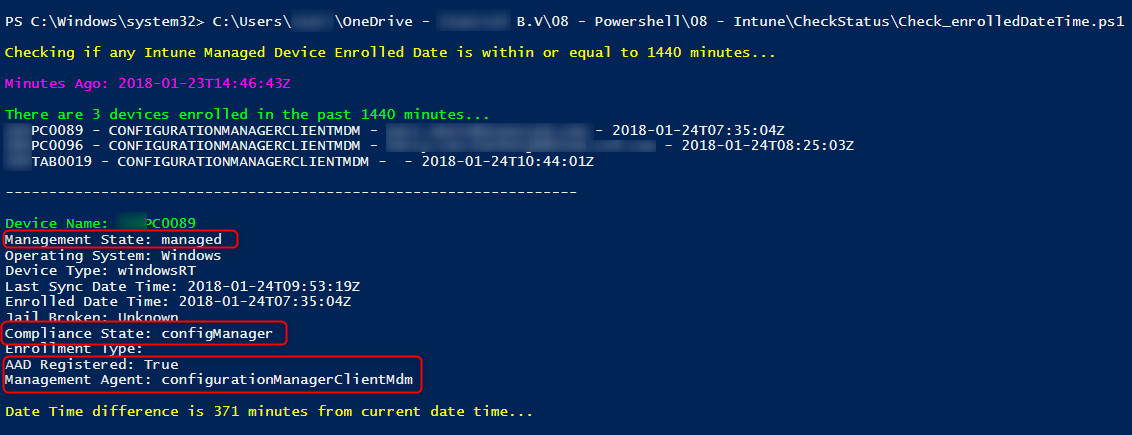
Just like the GUI the Intune Graph API shows the device is managed and the Compliance State is ConfigManager.
Auto MDM Enroll Windows 10; Summary
In this blog we have taken the necessary steps to migrate from the old Intune portal where devices are managed as computers, to the new Azure Intune portal using the MDM channel where devices are managed as mobile devices. I’ve also explained the inconsistencies I’ve seen during the migration and consequently created a support request with Microsoft and will keep you informed about the outcome. If you do want to refer to the case you can use the support request number: 118012417521948
More about:
- How to configure hybrid Azure Active Directory joined devices
- Enroll a Windows 10 device automatically using Group Policy
- MDM Registration Error Values
- SetManagedExternally function
- Administrative Templates (.admx) for Windows 10 Fall Creators Update (1709)
- Using the Microsoft Graph API to access data in Microsoft Intune
- Use PowerShell and Microsoft Graph to access data in Microsoft Intune

Excellent guide! First time I get a complete explanation. Well done!
Good to hear it’s appreciated. You’re most welcome!
Excellent article and guideline, very detail. Thank for your sharing.
I had configured successfully Hybrid Azure AD Joined Devices. Just note, the client slow update and if you have enable MFA when registering device, the system will prompt and user need verify it.
In addition, Group Policy need configured two policy as you explain above.
Best practice troubleshoot is read Event Log and using dsregcmd /status to analyze.
Thx for the feedback Huy. Much appreciated! Eventlog can certainly help out! You can also enable Analytic and debug logs in the Event viewer. This will give you an extra log (Debug) that you can enable under Application and Service Logs–> Microsoft-Windows–> DeviceManagement-Enterprise-Diagnostics-provider –> Debug.
I use autoenrolment scenario for domain joined computer. Intune is set up to standalone. My device is joined to ad azure (connect type Hybrid Join) with success, device is enrolled to Intune but without user assigment. When I open company portal I see “This device hasn’t been set up for corparate use yet….” . When I try assign I see message that “device is already beging managed by an organization “. In Intune console I see this device and MDM is enabled. What can I do to assign user to device? My previous expirence is that after auto enrolment I… Read more »
Hi Radek, Just to make sure I understand: Do you mean you can no longer choose a Device Category? This would make sense since the device is automatically enrolled to Intune MDM. You will have to install the company portal app to the device. When you start the company portal app, the user should automatically log-in. From there the you can choose the category upon log-in. You can also assign the category from the devices pane in Azure Intune. Did you try dsregcmd /status and what was the result? It’s strange there’s no user assigned to the device. You can… Read more »
How does this work with shared devices? For example, would this scenario work in a computer lab where people are constantly logging in/out of the computer?
Sorry for my late response 🙁 Still trying to find a good balance between projects and my blog 🙂 In this scenario I’m Automatically MDM enrolling devices to Azure so I think it’s not going to work for you. It is an interesting scenario and hope the info below will help: If the PC has been joined to Azure Active Directory, anyone within the same tenant can log in as a standard user and only the user who joined the device to Azure AD will be a local administrator. You can however use Intune to add more local admins when… Read more »
I am having an issue where SCCM detects my Hybrid AAD Joined machines as plain Azure AD Joined. Any help appreciated!
https://www.windows-noob.com/forums/topic/16319-sccm-1802-co-management-not-properly-detecting-hybrid-azuread-joined-devices-shows-as-azuread-joined/
Alexandros informed us that he has worked with MS Intune support and this has now been verified as an SCCM bug. The case has been assigned to the SCCM team. Thanks for keeping us informed Alexandros!
Hi Oktay,
Can I set on Intune any policy to the user can log in only in a determinated computer and cannot log on in others computers of company?
Hi Danilo, To my knowledge, the only option in Intune to come close to this is using the KIOSK mode but I don’t think this is what you are looking for. On a domain joined computer there is a GPO to Allow logon locally or deny logon locally. However,I have not found a similar option in Intune.
Hi There, Thank you for sharing your experience. this is indeed good stuff.
I am running in an situation where we have over 4000 windows 10 device to be enrolled to Intune for encryption roll out but the problem is we have Win10 version 1703.
Do we have anyone who has completed enrollment with version 1703.
Any leads would be highly appreciated, Thanks!
Regards,
PM
Hi Pankash,
If I understand correctly, you want to enroll W10 1703 to Intune and auto configure Bitlocker. Have a look at https://blogs.technet.microsoft.com/cbernier/2017/07/11/windows-10-intune-windows-bitlocker-management-yes/ It will not be 100% auto config/encryption and requires a little user input but might help you out.
Hi if you are moving from old on premise Intune to Azure Intune during your documented steps it doesn’t mention anything around the local Intune Connector on premise .. is that connector required still once you run through your process to completely Azure AD join and Enroll devices into Azure Intune standalone .. can the on premise Intune Connector be deprecated ?
Hi all, Nice article. I do have question about possible scenario. I am doing HybridAzureAD join with Autopilot with localIT account. I am caching end user credentials and sending laptop to the user. In a meanwhile I am deleting device from Intune and forcing GPO to autoenroll device. End user is receiving his laptop and connecting via VPN to company resources. GPO is applied and machine is again enrolled to Intune. Is it doable? I know that it’s againt Autopilot idea, but we need to use localIT account in the process. It works fine with Autopilot, but there is a… Read more »
Hello,
Kindly suggest on which OU should link GPO ?
[…] 5. Automatically MDM Enroll Windows 10 devices using Group … […]
[…] 5. Automatically MDM Enroll Windows 10 devices using Group … […]