Last Updated on April 2, 2020 by Oktay Sari
In this topic we’ll have a look at how to manage BYOD with Intune MAM to enable a bring-your-own-device (BYOD) scenario for your organization without the need to fully enroll devices into MDM. BYOD will raise some concerns about devices and applications that are being used by employees to access corporate data.
Therefore we need to protect corporate data on iOS and Android devices using Microsoft Intune app protection policies while making sure employees can be productive on devices they prefer. App protection policies work independent of any MDM solution. If you want to manage Windows 10 BYOD scenario’s without enrollment to MDM read my blog Windows Information Protection without enrollment.
Protecting company data with App Protection Policies
Microsoft Intune supports the following Mobile Application Management (MAM) scenarios manage BYOD:
- Fully enrolled in Intune (company owned devices).
- Managed by a third-party MDM solution (company owned devices).
- Devices not managed by any MDM solution (BYOD).
Note:
App protection policies only work for Office mobile apps that connect to Office 365 services. Apps that connect to on-premises Exchange, Skype for Business,or SharePoint are not supported. Furthermore, Windows devices are not supported in the MAM without enrollment scenario’s but you can use Windows Information Protection (WIP) to do the same for Windows 10 devices.
The difference between MDM and MAM
While Intune MDM protects at the device level, Intune MAM and App Protection policies protect at the application level. For example, with MDM you can force a PIN to access the device or fully encrypt the device, and with MAM you can require a PIN before users can access their corporate e-mail. with MDM enrolled devices you can also manage Windows updates and push software like Office 365 ProPlus.
Configuring Intune MAM without enrollment
Let’s have a look at how to configure Intune MAM without enrollment and App Protection Policies. When all is in place, we’ll also have a look at the end user experience on a mobile device.
App Protection Policies
Configure Intune App Protection policies before using app-based conditional access policies. App Protection Policies can be accessed and configured from two places:
- Intune>Mobile Apps>App Protection Policies
- Intune App Protection>App Policy
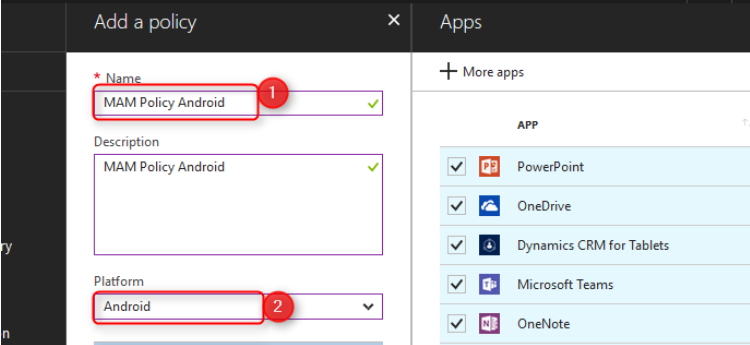
Choose the blade you prefer and click on Add Policy:
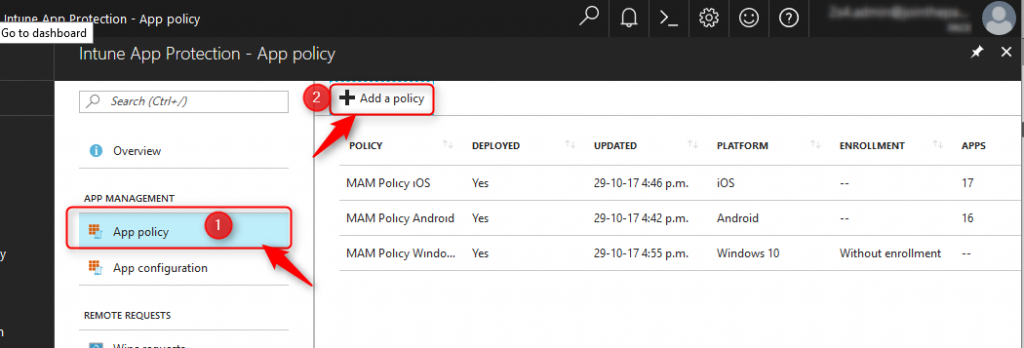
Fill in the blanks, choose a platform and click on Apps; Select required apps and choose the apps you want to protect.
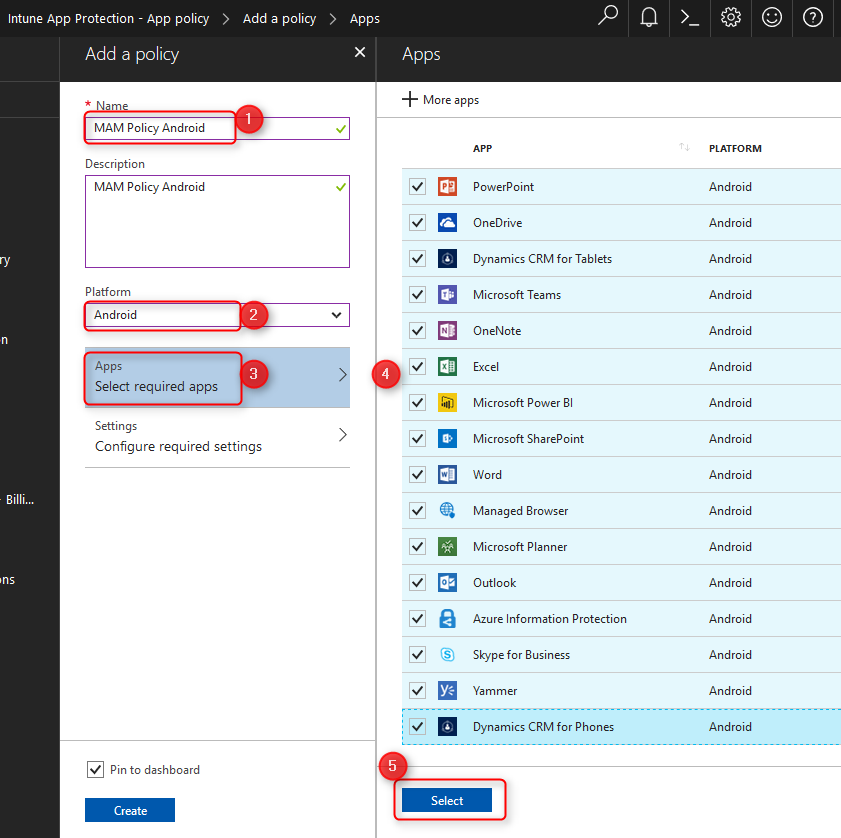
Now click on Settings; Configure required settings. There are two sections with settings to configure. Data relocation and Access.
Data Relocation
When you use apps without restrictions, corporate data can accidentally or knowingly be saved on for example personal Dropbox accounts causing data loss. You can use app protection policies to restrict data relocation to untrusted resources that are owned by the individual users. In the example below, you can see the Data relocation settings.

Info: The Allow app to transfer data to other apps will affect the the behavior of web content and only allow URL’s to open in the Intune Managed Browser. That is why I also set the Restrict web content to display in the Managed Browser setting to Yes. You can read more about this here.
Access settings
Then there are Access policies you can configure to enforce settings like PIN for access and Block screen captures. Configure the settings to your liking and click on OK and finally click on Create.
Back on the App Protection Policy blade, click on your newly created policy and assign it to the right user group.
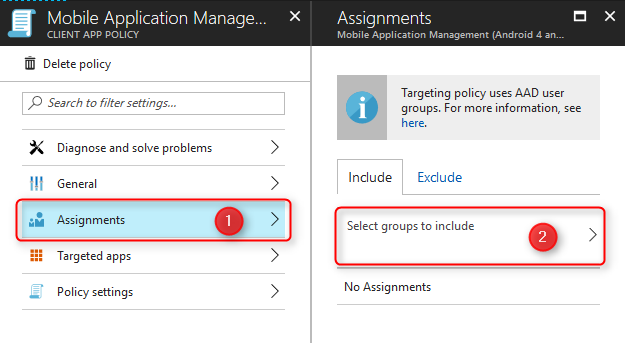
Now that you’ve created your first App Protection Policy, go ahead and create another one for iOS devices. The policies only take effect when users in assigned groups check in using protected applications.
Have a look at the status of the app policy for a user in the App protection user report that is available in the Intune App Protection area:
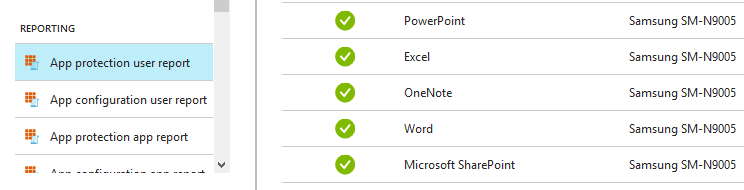
App Based Conditional Access Policies.
We can only protect company data on MAM enabled or MAM aware applications. Native apps on iOS and Android are not MAM aware and therefore need to be denied access to corporate e-mail and data.
Navigate to >Azure>Intune App Protection. Below the Conditional Access section click on Exchange Online>Allowed Apps. Select “Allow apps that support Intune app policies” and click on Save.
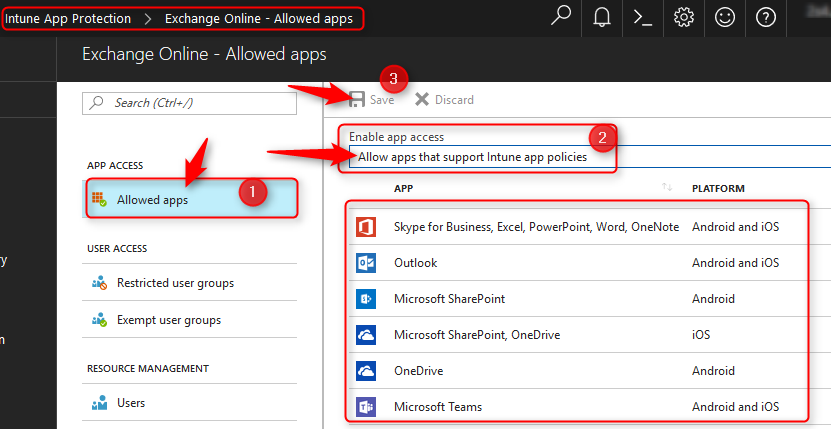
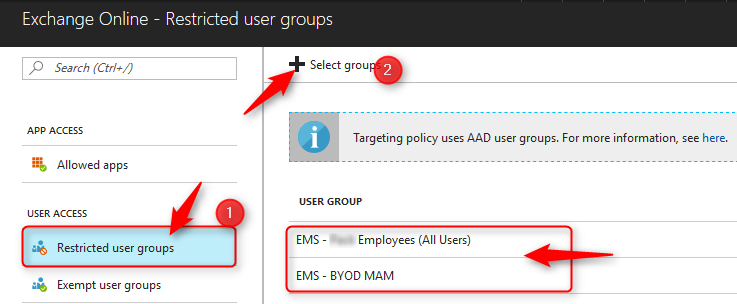
Continue and click on Restricted User Group>Select group, and select the user groups the policy applies to. If need be, you can even Exclude some of the users but personally I would go for all users.
Back on the Intune App Protection Blade do the same for Sharepoint Online.
Remove company data without touching personal data
For the final part in this blog let’s have a look at selective wipe and BYOD. When you manage BYOD with Intune, you’ll have the option to selectively wipe corporate data. When a device has gone missing or when the user leaves the company and there is no need to access data anymore, you can remove corporate data from the mobile device, without ever touching personal data. Once initiated, the device begins the removal process and upon completion, all corporate data is deleted. When a device is MDM enrolled a full wipe is also possible.
Navigate to >Intune App Protection>Wipe requests and click on New wipe request.
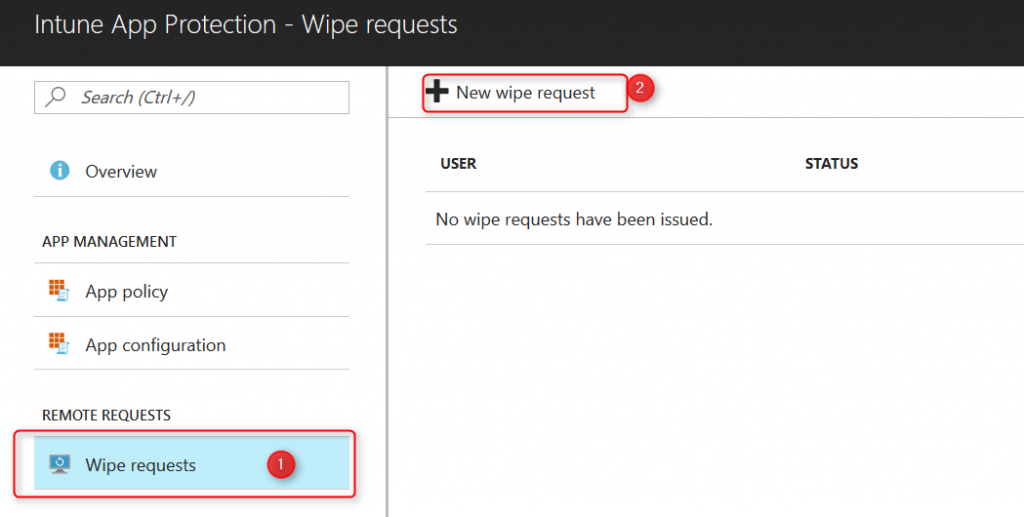
Click on User; Select the user and find the user. Click on Select.
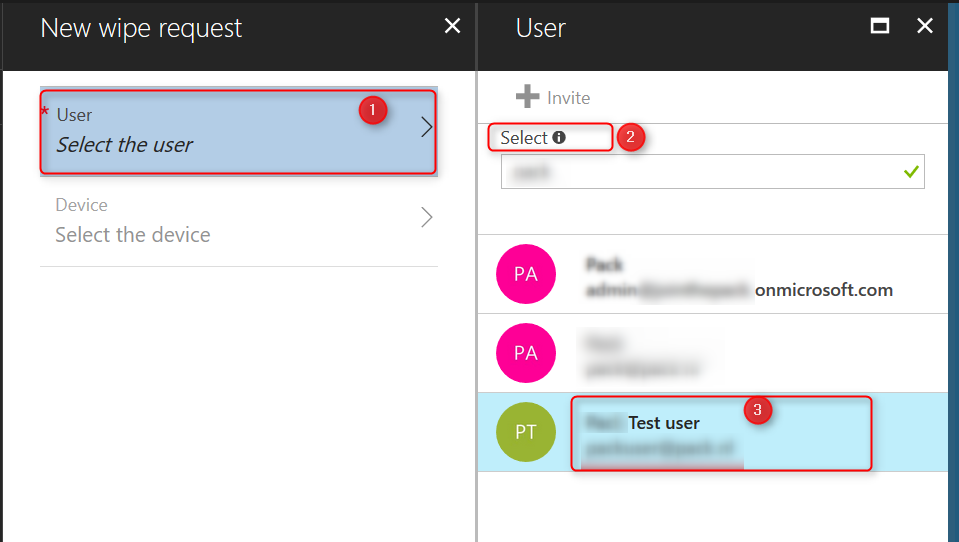
Next click on Device; Select the device. A list of devices registered for the user will show. Select the device you want to wipe and click on Select.
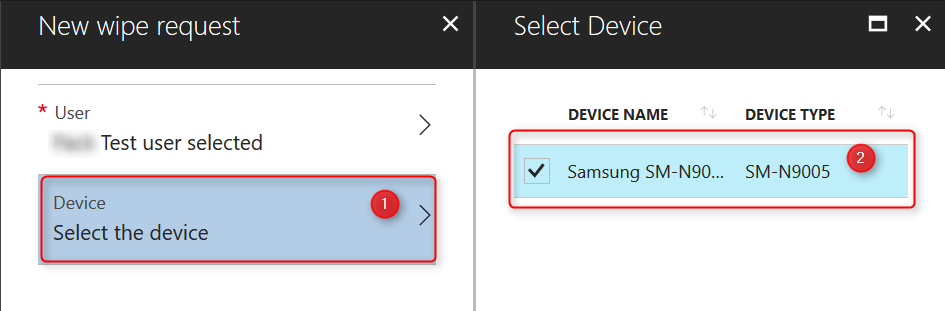
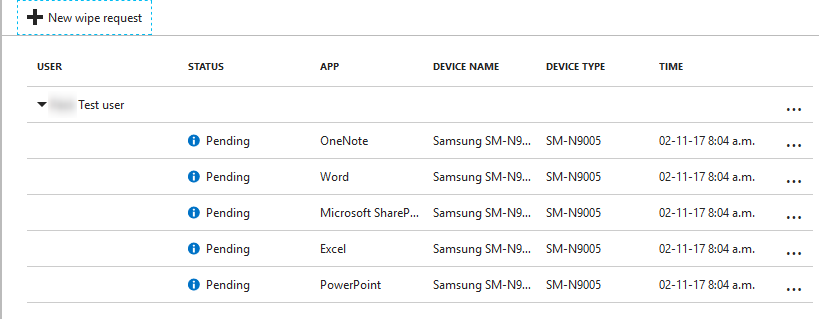
After selecting user and registered device, click OK to start the wipe process. The screen will show the apps and wipe status. Upon completion, the list will be empty again.
Note:
Before you delete a user from Azure Active Directory, make sure you Remove corporate data or fully wipe all devices registered with that user. If you delete users with managed devices, you can no longer issue factory reset or remove corporate data.
When the wipe request has finished you can also delete the device from Azure AD. Go to >Intune>Devices>Azure AD Devices. Search the device and delete it.
This concludes the Administration part in the Azure portal. Now let’s have a look at the user experience from A to Z.
User Experience
Remember we setup App Based Conditional Access for Exchange online and Sharepoint? In this example we’ll have a look at how the native e-mail client responds after adding a corporate account. I’ll skip the part where you configure the account. Go ahead and configure an account on your mobile and try to login and read your e-mail.
User Experience; Native e-mail application
 As you can see, Conditional Access rules are very easy to setup and deploy to your organization. You have effectively restricted access to corporate e-mail using the native e-mail client. Conditional access can ensure that only authenticated users, and approved apps, have access to your corporate data. In this case users need to download the Microsoft Outlook App to read corporate e-mail.
As you can see, Conditional Access rules are very easy to setup and deploy to your organization. You have effectively restricted access to corporate e-mail using the native e-mail client. Conditional access can ensure that only authenticated users, and approved apps, have access to your corporate data. In this case users need to download the Microsoft Outlook App to read corporate e-mail.
User experience; Managed Apps
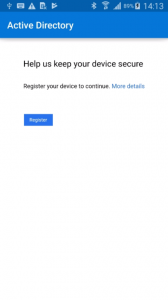
Go ahead and install Microsoft Outlook. Once the app is installed, configure your corporate e-mail account. You will be forwarded to the Office 365 portal to login. Once logged in, you will see the following message “Help us keep your device secure”
Intune MAM works together with (and relies on) the Intune Company Portal App. You should be familiar with it because you also need this to MDM enroll devices to Intune. There is one difference though. Since we’ll be managing applications only and without enrollment, the user does not need to sign in within the Company Portal App. For MAM, the Company Portal app just needs to be installed on the device. The Microsoft FAQ provides a little more info.
Click on Get the app and install the Intune Company Portal app. Once the app is installed you can continue with Microsoft Outlook. This time the app will request you to register your device to continue. Once registered, Outlook will open and you can access corporate e-mail.
User Experience; App Protection Policies
In most cases Microsoft Outlook will show a message about IT protecting your corporate data. It might take a little longer but when you restart the app, your data is protected.
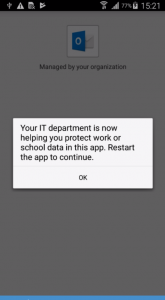
The app protection policies you configured are now enforced. One of the settings we configured was under the Data relocation section:
Setting: Restrict cut, copy, and paste with other apps
Value: Policy managed apps with paste in.
This setting restricts data from managed apps to be copied to unmanaged apps and prevents data relocation. Let’s see how this looks like for the end user.
Open any e-mail, select some text, right click and copy te text to your clipboard. For this example I’ll use the native Note app on Android and try to paste the data there:
“Your organization’s data cannot be pasted here”. You are not allowed to do so. When you copy data between managed apps, it will allow you to continue without restrictions.
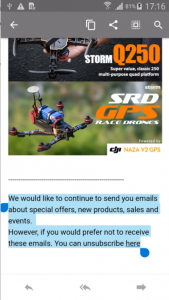
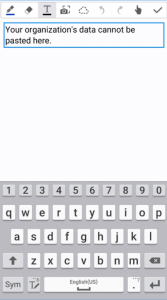
This applies to all managed apps. When a user tries to copy/paste a word document from Onedrive for Business to dropbox, he or she will receive a similar notification.
User Experience; Selective Wipe
In the final step we’ll have a look at the user experience when an administrator initiates a selective wipe for a device. In most cases, it will only take minutes for the device to start removing corporate data. Administrators can also disable logins to make sure the user can’t login, unless the account is re-enabled. The user can now continue to use the apps for personal data and e-mail.
Summary
In this blog we have setup Intune app based conditional access and app protection policies to manage BYOD with Intune and prevent corporate data from leaking when it is accessed by users on personal devices. The users do not have to fully MDM enroll their devices, which is more appealing as they don’t need to allow 100% control over their own devices by corporate IT.
More about managing BYOD with Intune:
- What are app protection policies
- Protect app data using app protection policies with Microsoft Intune
- Understanding the capabilities of unmanaged apps, managed apps, and MAM-protected apps
- Get started with Intune device compliance policies
- Enable BYOD with Intune
- Set up app-based conditional access policies
- Block apps that do not use modern authentication (ADAL)
- Manage BYO Windows 10 devices with Windows Information Protection without enrollment
UPDATE:
Conditional Access policies for Intune are now available in Azure AD. Read more about this change update.
I’m not sure you’re correct about needing to target MAM iOS and Android BYOD users in the Azure AD Configure (MDM and MAM) area. Once you create an application protection profile, you have to make an Assignment for the policy to take affect. That’s done on a policy by policy basis and would seem to be the better place to set MAM scope. Thoughts?
Hi Bill, First of all, I’d like to thank you for sharing your thoughts. Much appreciated! Second, you are right and I have updated the post accordingly. The MDM and MAM User scope settings are there to enable Windows 10 automatic enrollment as explained in https://docs.microsoft.com/en-us/intune/windows-enroll . I apologize for any confusion and hope the (updated) post is informative and of value for you.
Hi Oktay, thanks for writing this article it was extremley useful. However, I am running into a small issue at the App Based Conditional Access Policies section. When I click on Exchange Online under conditional access, I get a message that says: “App based conditional access is now a capability of Azure Active directory (Azure AD) that enables you to control how authorized users access your cloud and client apps. While the purpose is still the same, the release of the new Azure AD portal has introduced significant improvements to how app based conditional access works. The conditional access policies… Read more »
Hi Robert, Glad to hear I could help. I would expect this message in the old azure portal but think you’re working in the new portal. I’ve tested this today in 3 different tenants and all work as described in this blog so I’m a bit lost. Did you receive any links with the error and can you give me some more information about whats happening? I’m assuming you can’t configure the policy at all.
Hi Oktay,
Thanks for replying.
Something very strange is happening, as I have just tested it with our live tenancy and I get the screens as expected (as per your previous screenshots), but my new test O365 tenancy which I setup a month ago doesn’t allow me to configure this.
I tweeted about this, but the responses back haven’t helped but the screenshot of what I get is on there: https://twitter.com/robm82/status/951492603471712258
Hi Robert, Same thing happened at my own tenant just this morning. I’ve had a bad fever and done nothing for a week (sorry for my late response) but this morning the same error message showed up for Sharepoint Online. Exchange online is still working. Have a look in your Azure portal: (Test with a select group of users before deploying to all users) 1- Go to Azure Active Directory 2- under section security click on Conditional Access. 3- Create a new policy and name it ‘Exchange Online CA’ 4- Assignment; assign it to a test user group 5- Cloud… Read more »
Just wondering if others experience “an error occurred” in Outlook after the Device Registration process takes place. This happens to me and it seems like a time-sensitive matter where retrying right away doesn’t help, but retrying in about 20 minutes the issue is resolved. Every time for me.
[…] when trying to open a URL? Then I hope this post helps a little. In a previous post I wrote about managing BYOD devices with Intune MAM policies and I suggest you read that if all this is new to […]
Hello – I’ve set up app protection policies and conditional access policies to only allow exchange 365 access through outlook on BYOD devices using MAM (not fully enrolled in MDM). But I’m not able to figure out how to remove or selectively wipe company data. I seem to only be able to do that for fully enrolled devices in MDM. Am i missing something?
Hi Ron, When you retire a BYOD device, all company data will be removed without deleting personal data. The same happens when you delete a device. See https://docs.microsoft.com/en-us/intune/devices-wipe for more on that.
You can also create a wipe request to selectively delete company data from managed apps. These apps should be targeted by app protection policies you created. See https://docs.microsoft.com/en-us/intune/apps-selective-wipe. Also read the FAQ on this site because there are a few requirements you’ll need to have in place.
Hope this helps
Well written, managing corporate data is easy with BYOD solution like MobiLock Pro, which requires no IT knowledge!
Hello, First of all thanks for this very detailled and usefull article. I have a question about Windows 10. You write that MAM cannot be used for Windows 10 like on Android or IOS and you speak about WIP. Is always true at this time in January 2019 ? i can’t find any informations about how to managae BYOD Windows 10 device. We plan to allow BYOD device for remote work at home in my companiy and i want to use MAM instead of MDM that it too intrusive. Do i need to use WIP only ? Do you know… Read more »
Hello Nicolas, Thank you for your feedback! Windows 10 in BYOD scenario’s can be managed with Intune. For this, you will need to configure WIP. Windows Information Protection can target devices with enrollment and also devices without enrollment. The last one is also called WIP-WE or sometimes Mobile Application management without enrollment (MAM-WE) For BYOD you will configure WIP-WE policies. This will enable you to manage corporate data in enlightened applications. WIP can work standalone or combined with other options for BYOD scenario’s. I’m currently working on a series of posts and hope these will help you further. I expect… Read more »
Hi Nocolas, Have a look at https://allthingscloud.blog/windows-information-protection-without-enrollment/. I hope this will help you further.
hi Oktay,
how to enable different policies for the same user? depending on what he chooses.
for ex, if he choose personal ~~ i want the personal byo policies to get applied to him
if he chooses corporate, he must get the corporate device policies applied to him
Can this be done for Company Portal on windows devices? I am trying to run Company Portal on non-enrolled BYOD
Hi Adam, I’m not sure if I understand your question. Could you give me a little more info about what it is, you’re trying to achieve?
[…] 5. Manage BYOD with Intune MAM Without Enrollment – […]
Can we get this process updated for the new Endpoint Manager? Some of these are a bit off and I am getting held up implementing this.
Thanks so much for this! it’s really helped me get started, only question I have is regarding assignments. Will it conflict if I use the same BYOD group for iOS, Android, AND WIP?