Last Updated on December 31, 2023 by Oktay Sari
July 2022
IMPORTANT UPDATE: Microsoft announced the sunset for Windows Information Protection! WIP will be discontinued over time. Support for Windows Information Protection Without Enrollment will end by the end of calendar year 2022. Please read the official announcement and more on the following 2 sites:
- Announcing the sunset of Windows Information Protection (WIP)
- Support tip: End of support guidance for Windows Information Protection
If you have plans to implement WIP, I suggest you rethink your strategy accordingly. I will follow-up on this and update the WIP posts I have when more information is released by Microsoft.
In this post I’ll focus on WIP-WE User Experience. Also known as Windows Information Protection without enrollment on Windows 10 devices. WIP Without Enrollment is a great solution for organizations supporting a BYOD solution. In addition, WIP-WE provides a degree of control to manage and secure corporate data on personal devices. If you want to know how to configure WIP-WE policies, read my previous post covering just that.
This post is part of a series I’m working on. Have a look at my other posts for more information about WIP.
- Introduction to Windows Information Protection
- Configuring MDM user scope and MAM user scope
- WIP-WE / MAM – Windows Information Protection without enrollment
- Windows Information Protection with Enrollment
- Windows Information Protection User Experience
- WIP-WE User Experience – WIP Without MDM enrollment (this post)
- Set up Azure Rights Management for WIP
- WIP Without Enrollment Selective Wipe
- Troubleshooting Windows Information Protection
- Monitoring and collecting WIP audit event logs
- WIP Learning mode
- Support Windows 10 BYOD with Microsoft Endpoint Manager and WIP-WE
Prerequisites
The first part of this document will be about the prerequisites, considerations and my test configuration setup to give you a better understanding about what I worked with. After that, I’ll dive into to the WIP-WE user experience.
Make sure you have the prerequisites in place;
- Intune enabled as the MDM authority
- Windows 10 1703 and above (Pro, Enterprise, Education)
- EMS E3 licenses (or at the very least Intune and Azure AD premium P1)
- Configure your MAM provider in Azure AD for WIP without enrollment
Configuring your MAM provider
Before you create your WIP-WE policy, you need to set up your MAM provider or the MAM URLs in Azure AD. Configure the MAM Discovery URL to enable WIP-WE for Windows 10 devices . In other words, without a MAM provider users cannot enroll into WIP-WE (MAM) management.
I dedicated another blog post on configuring MDM users scope and MAM user scope. Please read that post if you want to learn more about configuring MDM and MAM scopes.
WIP-WE Considerations
I suggest you have a whiteboard session before you actually configure and deploy WIP-WE for all your users. Think about what it is exactly that you want to accomplish on NON managed BYO devices. What degree of security are you looking for? Here are a few topics that you may want to consider:
- Can users Azure AD Join and MDM enroll personal devices?
- Can they install and use Office 365 desktop apps to access corporate data?
- Do you allow access only by using a browser (Online only)?
- Can users Sync OneDrive for Business on their personal Windows 10 devices?
- Is downloading corporate data allowed on personal Windows 10 devices? Think about downloading:
- E-mail attachments
- OneDrive files
- SharePoint Online
- Microsoft Teams
- Can users remove WIP protection from files?
MDM Device Enrollment restrictions
I configured MDM device enrollment restrictions. As a result I don’t allow personal devices to be Azure AD joined. If you do the same, make sure you understand the consequences and limitations. Please read the documentation about blocking personal Windows 10 devices.
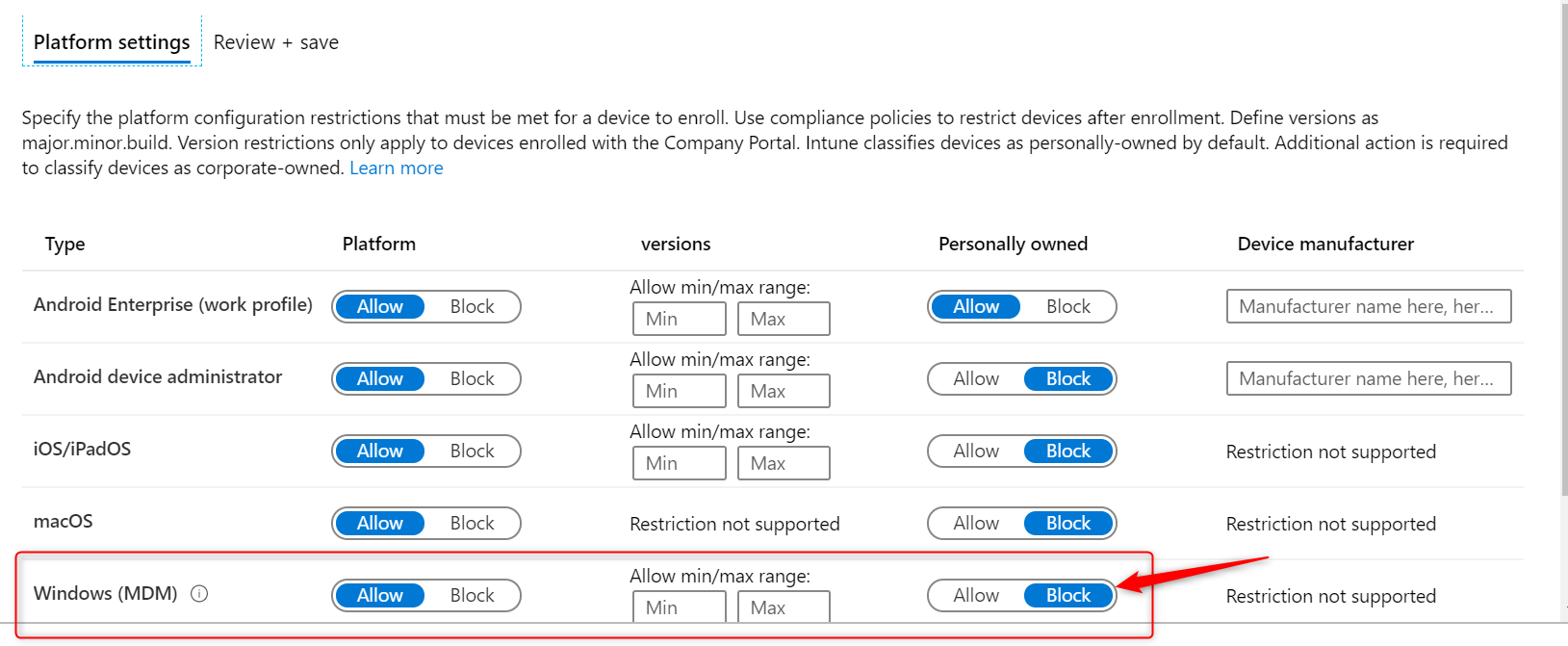
Windows Information Protection configuration
I’ve set the ‘Windows Information Protection mode’ to Block and the Network boundaries are configured as described in my previous post Windows Information Protection without Enrollment.
IMPORTANT: Unlike Azure AD Joined and MDM enrolled devices, you have a lot less control over personal devices that are only Azure AD registered.
By setting your WIP protection mode to Allow Override, users are allowed to change file ownership and decrypt files. This action is written to the local event log. However, you cannot collect event log entries to Azure Log Analytics. To collect event logs, you need to install Microsoft Monitoring Agent. And since deploying apps to Windows 10 requires a device to be MDM enrolled, you cannot collect event logs. Therefore I set it to Block.
- I have configured and assigned WIP policies
- As before, In this scenario I did not configure Azure RMS
Windows 10 test device configuration
- I have a personal Windows 10 1909 Pro test-device available for this WIP-WE User Experience.
- The device is NOT managed with Microsoft Intune and is not registered with Azure AD.
- I have a personal OneDrive and Personal Dropbox configured
- Installed my Office 365 desktop apps from the Office 365 portal.
- OneDrive for Business is installed
Azure AD registration
WIP-WE works only when a device is Azure AD registered. This can be accomplished by adding a work or school account by going to Settings –> Accounts –> Access work or school, or after adding an account to one of the Office 365 apps. For example, In this post I’ll go for the Office 365 apps version to register my device in Azure AD. And when I start Office Outlook for the first time, I need to login with an account to activate my license.
Have a look at this next screen because this screen follows after you login to Office:
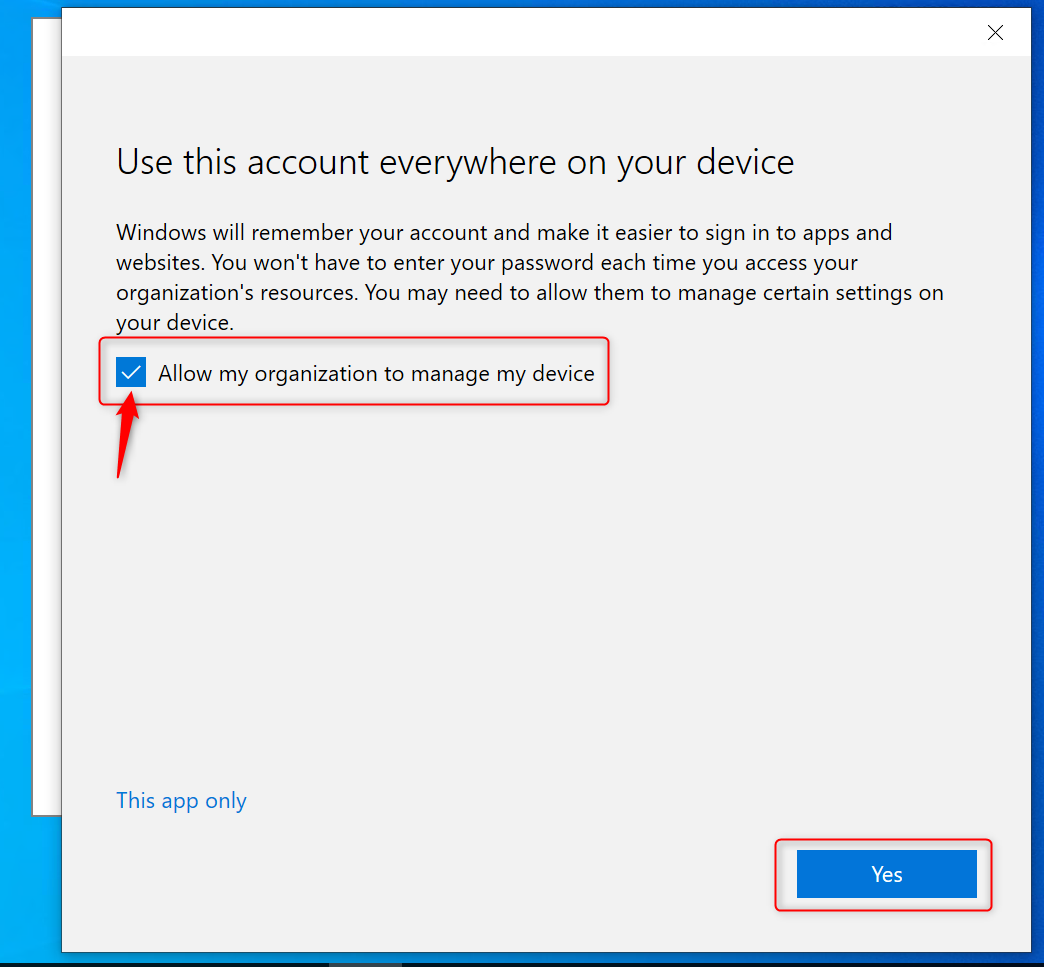
Most users will not pay any attention and just click on Yes without unchecking the check box “Allow my organization to manage my device”. As a result, the device will try to register in Azure AD. It also works wonders for SSO. For the purpose of this example I’m going to click on Yes and continue.
Assuming everything goes as planned and without errors, the device will complete the registration with Azure Active Directory.
Finally, click on Done and complete the setup for Office Outlook.
Check your Azure AD registration
You can check and see if your work account was added by going to Settings –> Accounts –> Access work or school
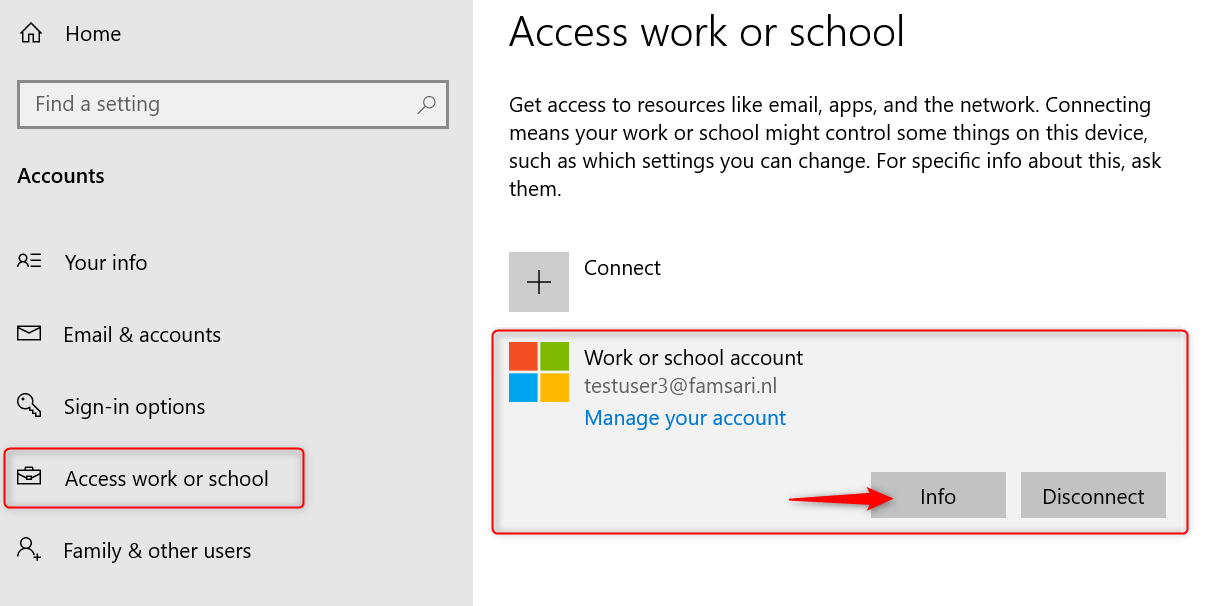
Click on Info to see more about the connection. The management Server Address shows https://wip.mam.manage.microsoft.com:444/checkin.
Also have a look at Azure AD devices:
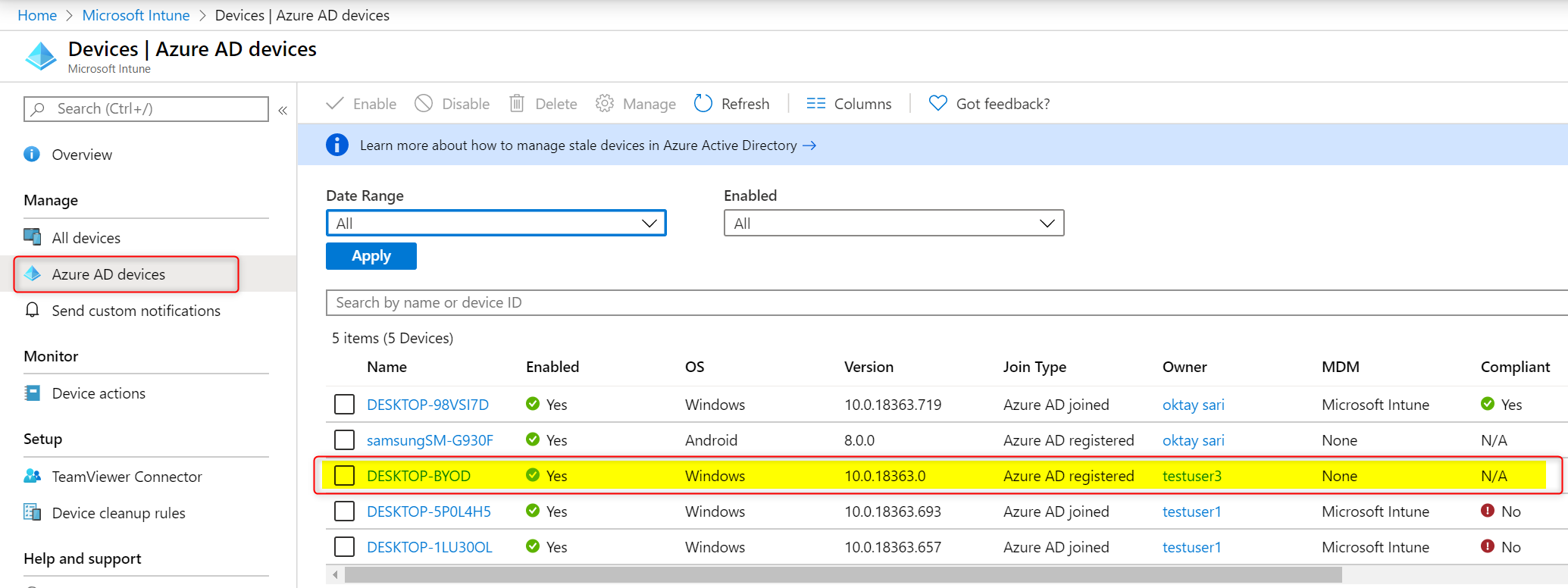
The device is Azure AD registered, not managed by MDM and therefore, does not need to be compliant. Can’t explain it any better than Microsoft, and I quote:
“The goal of Azure AD registered devices is to provide your users with support for the Bring Your Own Device (BYOD) or mobile device scenarios.” Read more about Azure AD registered devices on Microsoft’s website.
WIP-WE User experience
The WIP-WE user experience is almost the same as with MDM enrolled devices like I wrote about in my previous blog Windows Information Protection User Experience. However, there are some things to keep in mind:
- WIP protection mode is set to Block and as a result users are not allowed to change file ownership. Also copy/paste to unprotected apps or unprotected locations is not allowed. Most importantly, WIP protection cannot be overruled.
OneDrive for Business works the same as with WIP with enrollment. Consequently, you’ll see there is an extra column “File ownership”. And all the files have famsari.nl (my test tenant) set as the File ownership. The same is true for all the synced files from SharePoint. File encryption based on EFS only occurs when downloading files locally on your device. That is to say, data is not encrypted online!
Have a look at the screenshot below. You’ll see that all file icons have an extra symbol in the form of a suitcase. This is yet another indication that these files are corporate data. You can enable or disable this icon overlay by setting the WIP configuration option “Show the enterprise data protection icon” to On or Off.
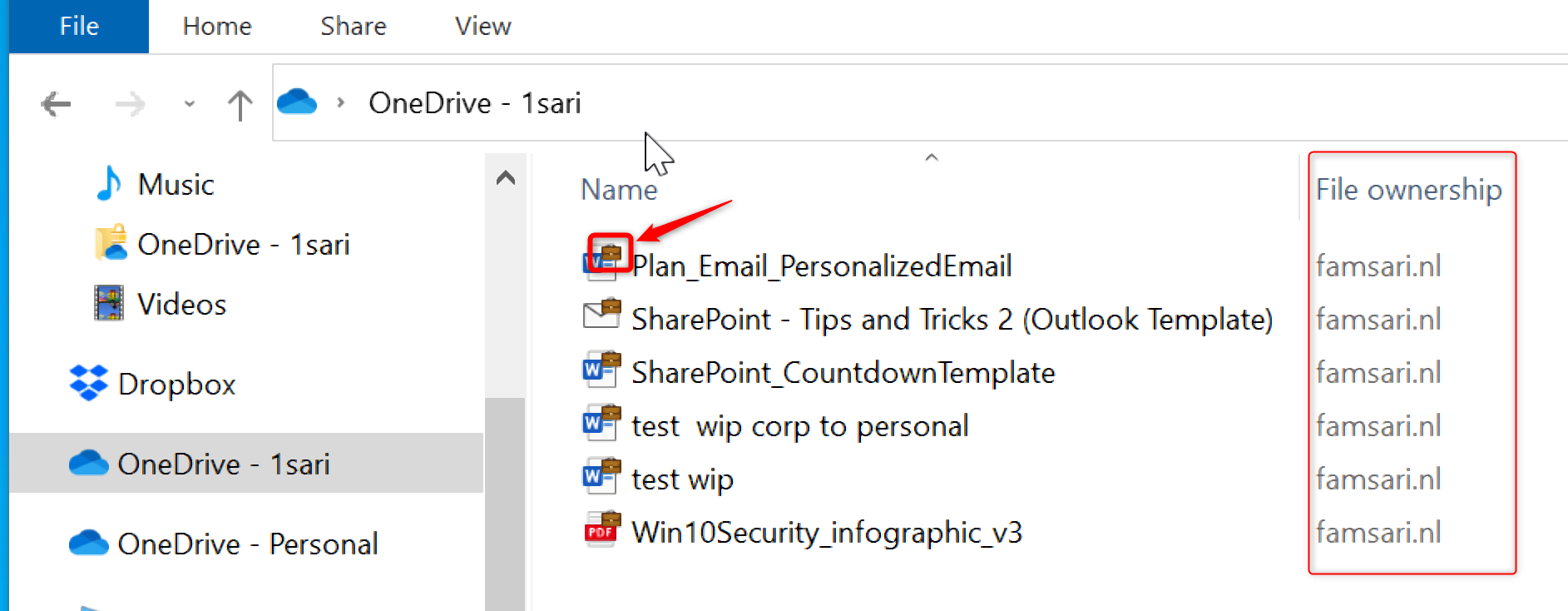
Copy paste restrictions between applications
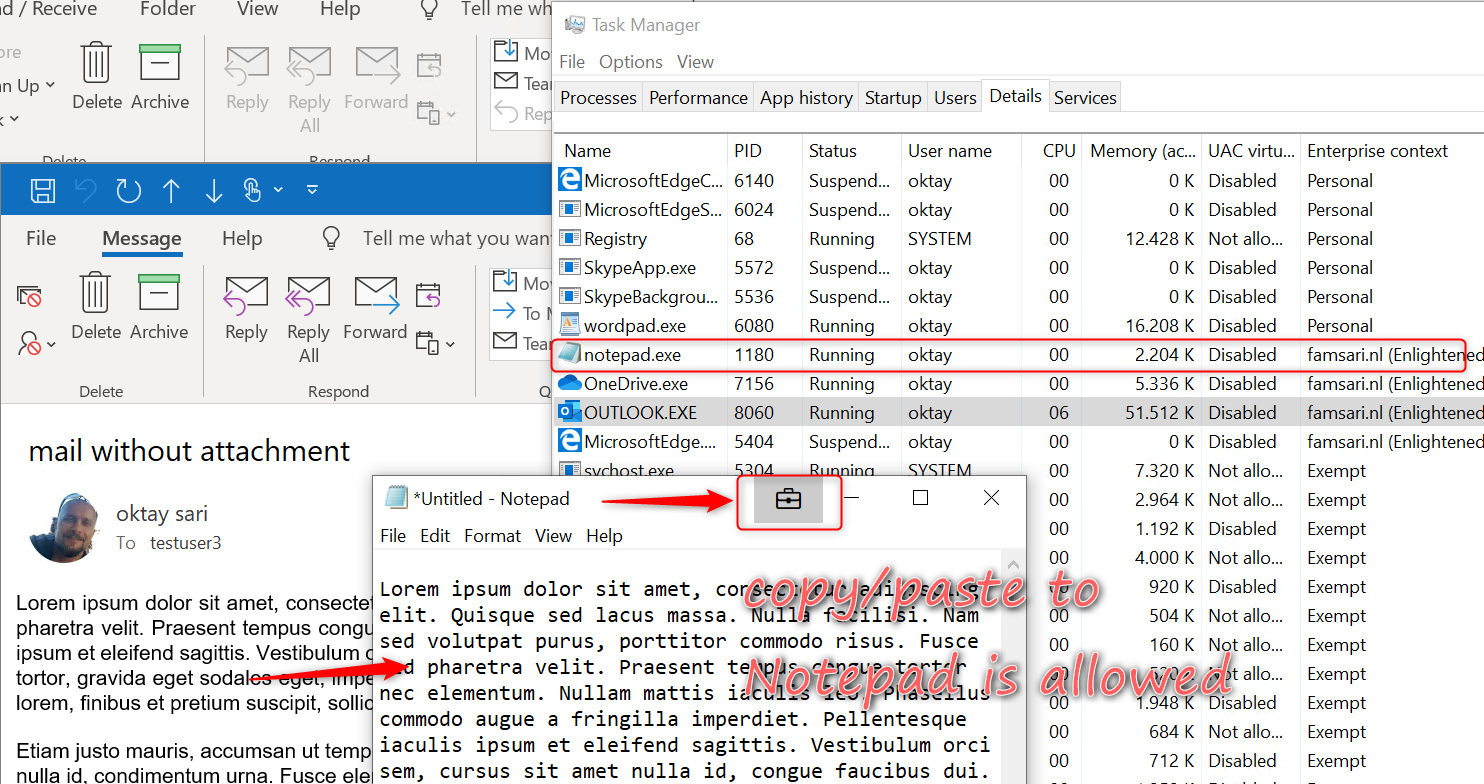
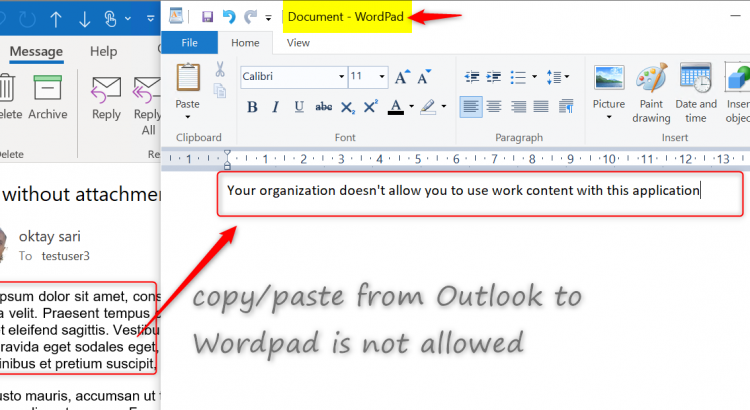
Just like before, the restrictions for copy/paste actions from managed to unmanaged application depend on the targeted applications you have configured for the WIP-WE policy. When I copy data from Outlook (managed application) to Wordpad (unmanaged application), instead of pasting the information I copied, an error message is pasted; “Your organization doesn’t allow you to use work content with this application”
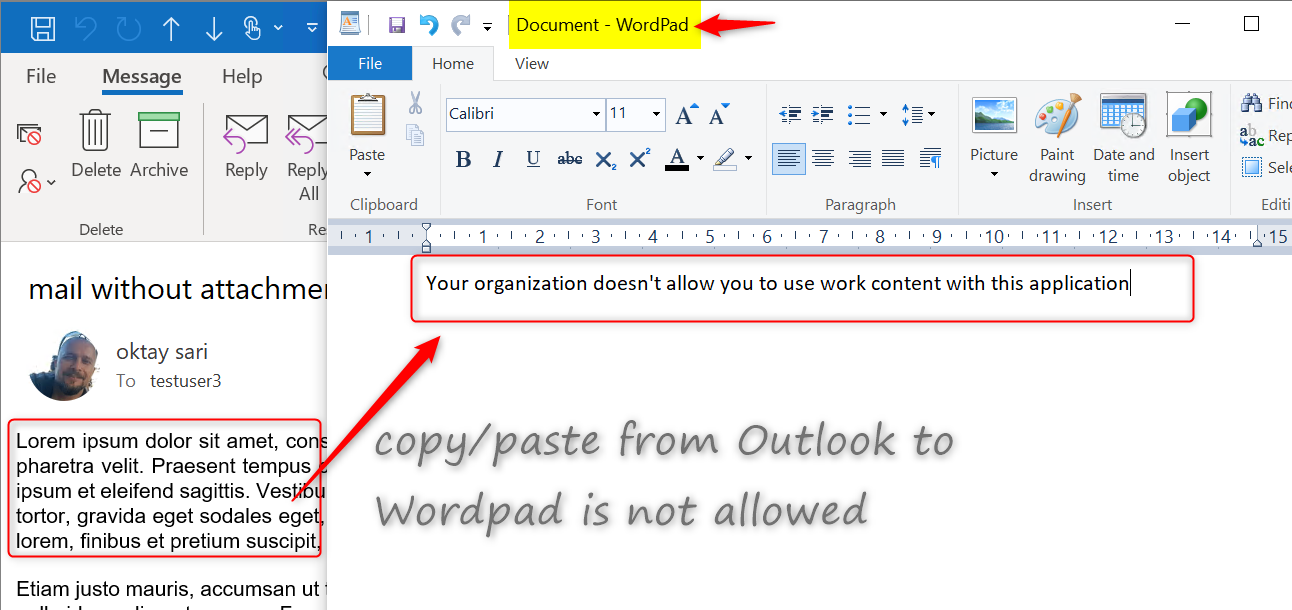
Notepad is configured as a managed application and the Task Manager shows the Enterprise context is set to famsari.nl. Managed (enlightened) applications can differentiate between corporate and personal data. First I’ll open Notepad and just start writing. Have a look at the upper right corner (minimize, restore, close). This file is handled as a personal file and saved without WIP protection.
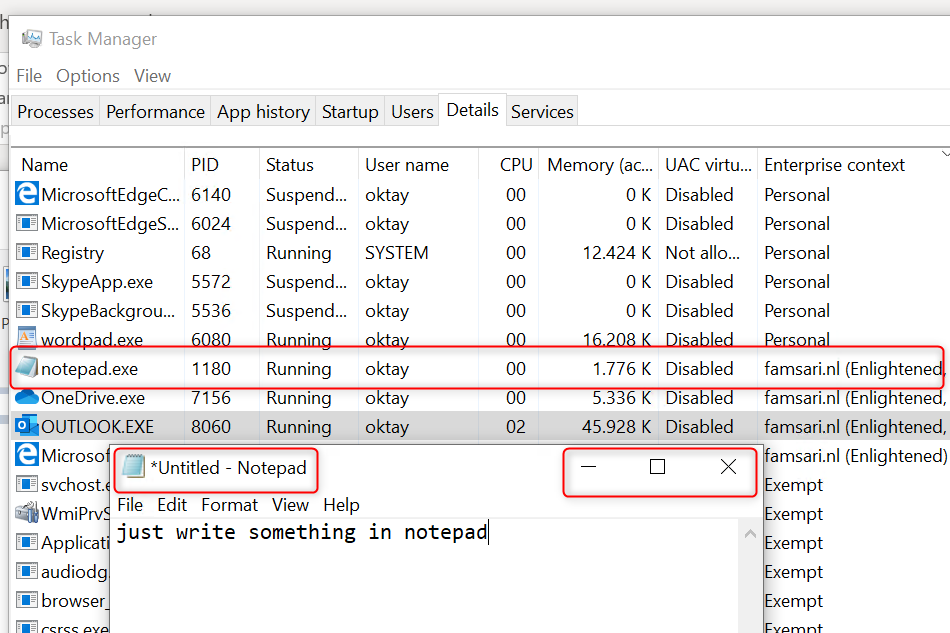
When I copy/paste corporate data from Outlook to Notepad, it knows this is corporate data and shows this with an extra symbol in the upper right corner. Notepad is a managed application and therefore I’m allowed to paste data.
Unapproved browsers
Just as with WIP with MDM enrollment, unapproved browsers like Google Chrome will not allow to copy/paste information from documents. In addition, uploading documents is not allowed. There is no option to overrule the WIP-WE protection.
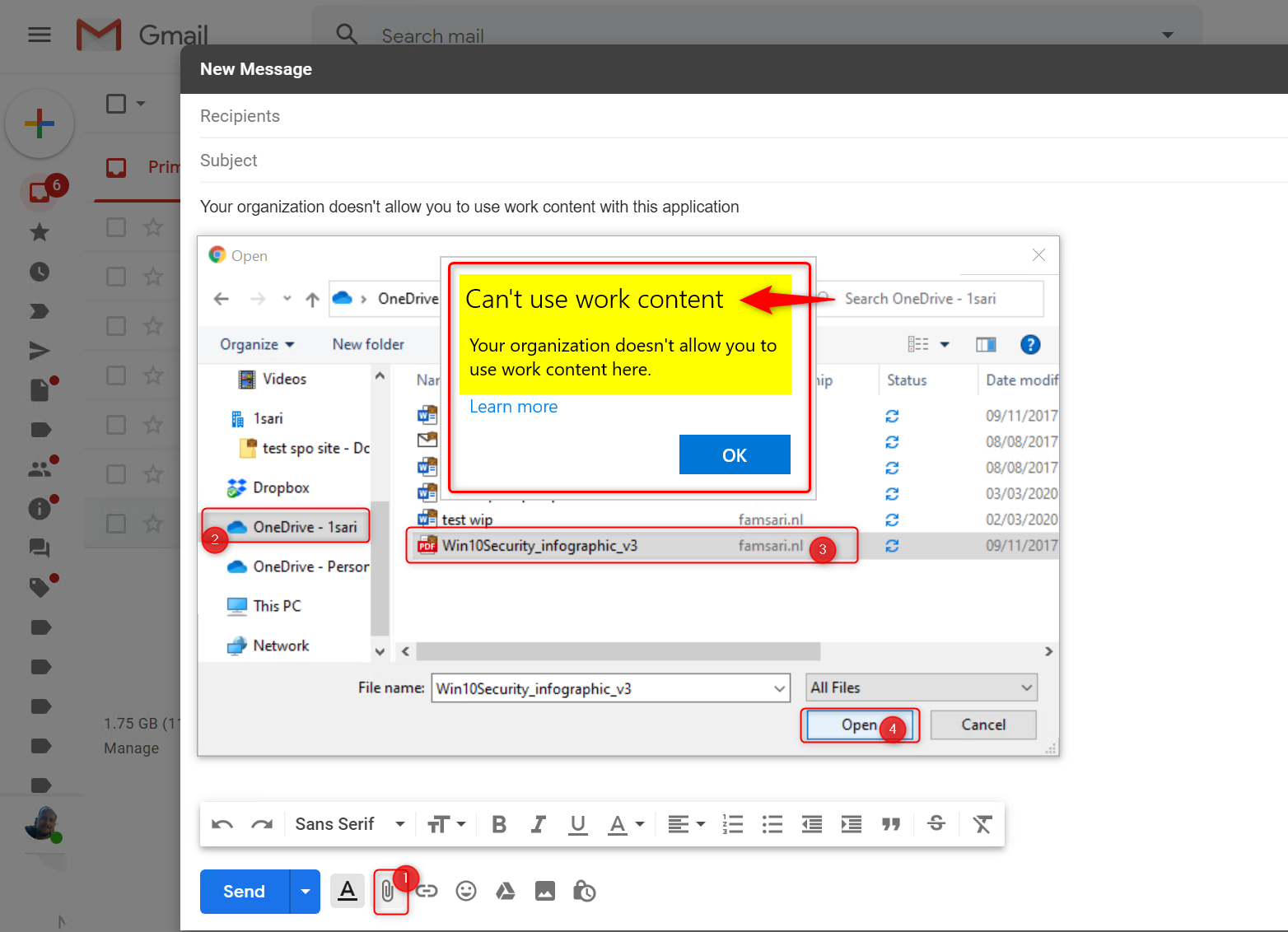
Approved browsers
Microsoft Edge legacy Browser supports WIP. However, WIP Protection mode is set to block and as a result my actions to copy/paste or upload an attachment to Google Gmail are blocked.
OneDrive for Business: Relocating protected files
WIP-WE will protect files when I copy and paste or move documents from OneDrive for Business to any other location on my device (like C:\Temp). You can double check this by looking at the File ownership property of your files.
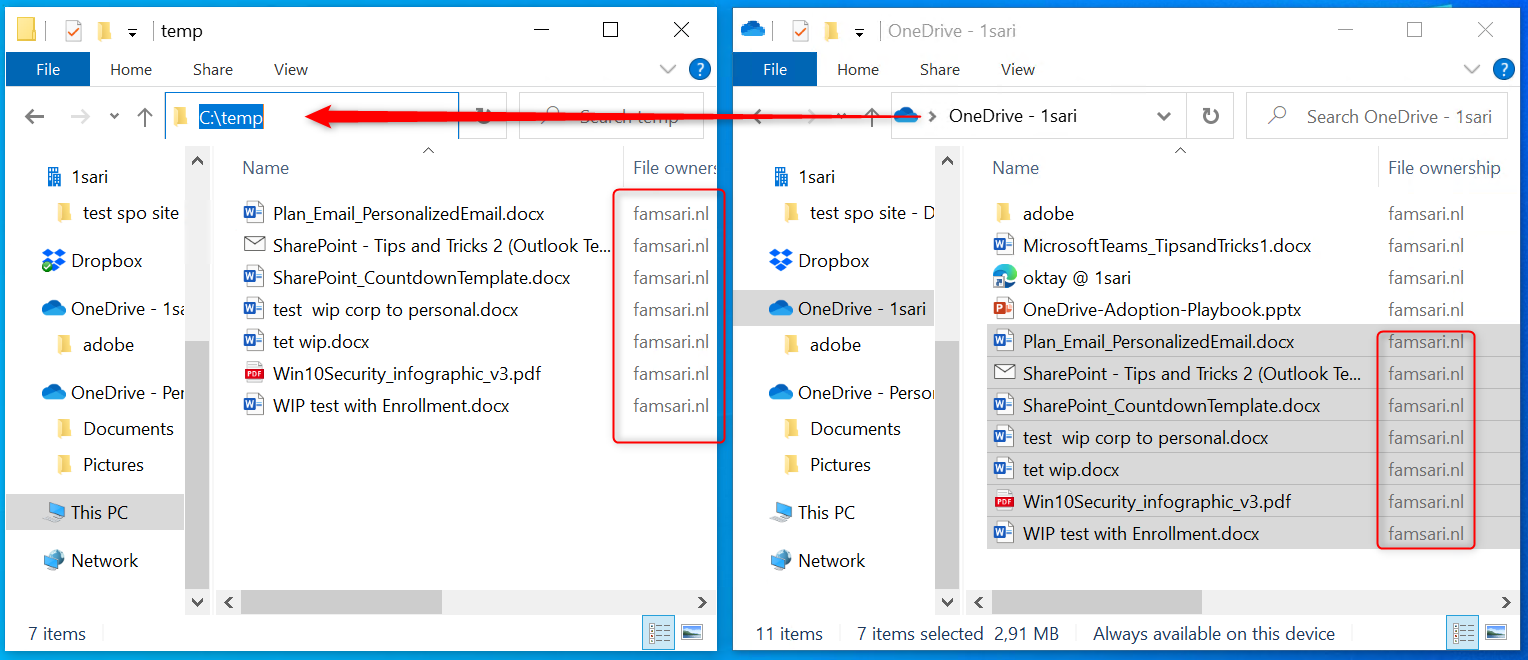
I can’t remove the WIP protection from these files. Right click on any of your files and click on File Ownership in the menu. Personal and Work options are greyed out.
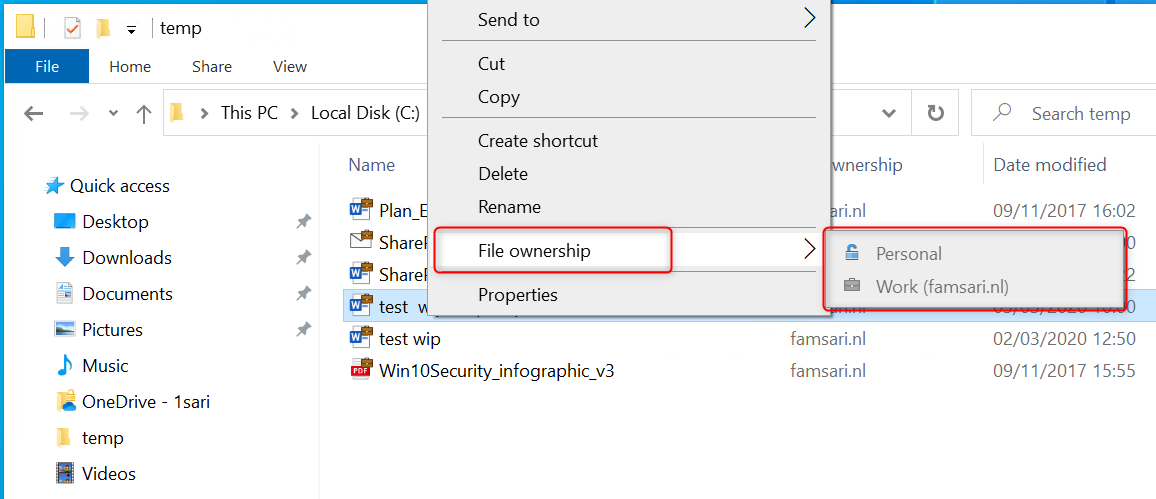
Relocating WIP-WE protected files to OneDrive Personal
I am not allowed to copy/paste or move files from OneDrive for Business and SharePoint Online to OneDrive Personal. The action is blocked by WIP-WE.
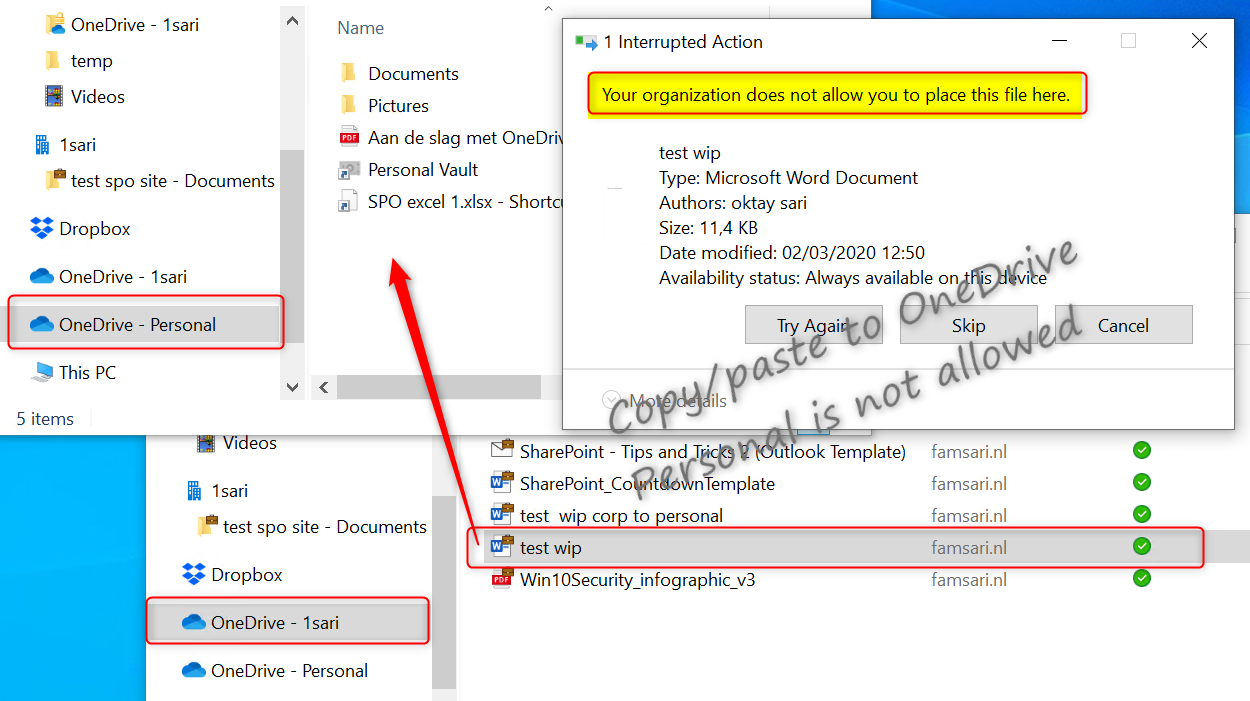
Relocating WIP-WE protected files to Dropbox
Copying WIP-WE protected files to Dropbox seems to work but again, files will not sync. Look closer and you will see that the files have the corporate file ownership tag and a red cross in the document icons. As a result, the files will not sync to Dropbox.
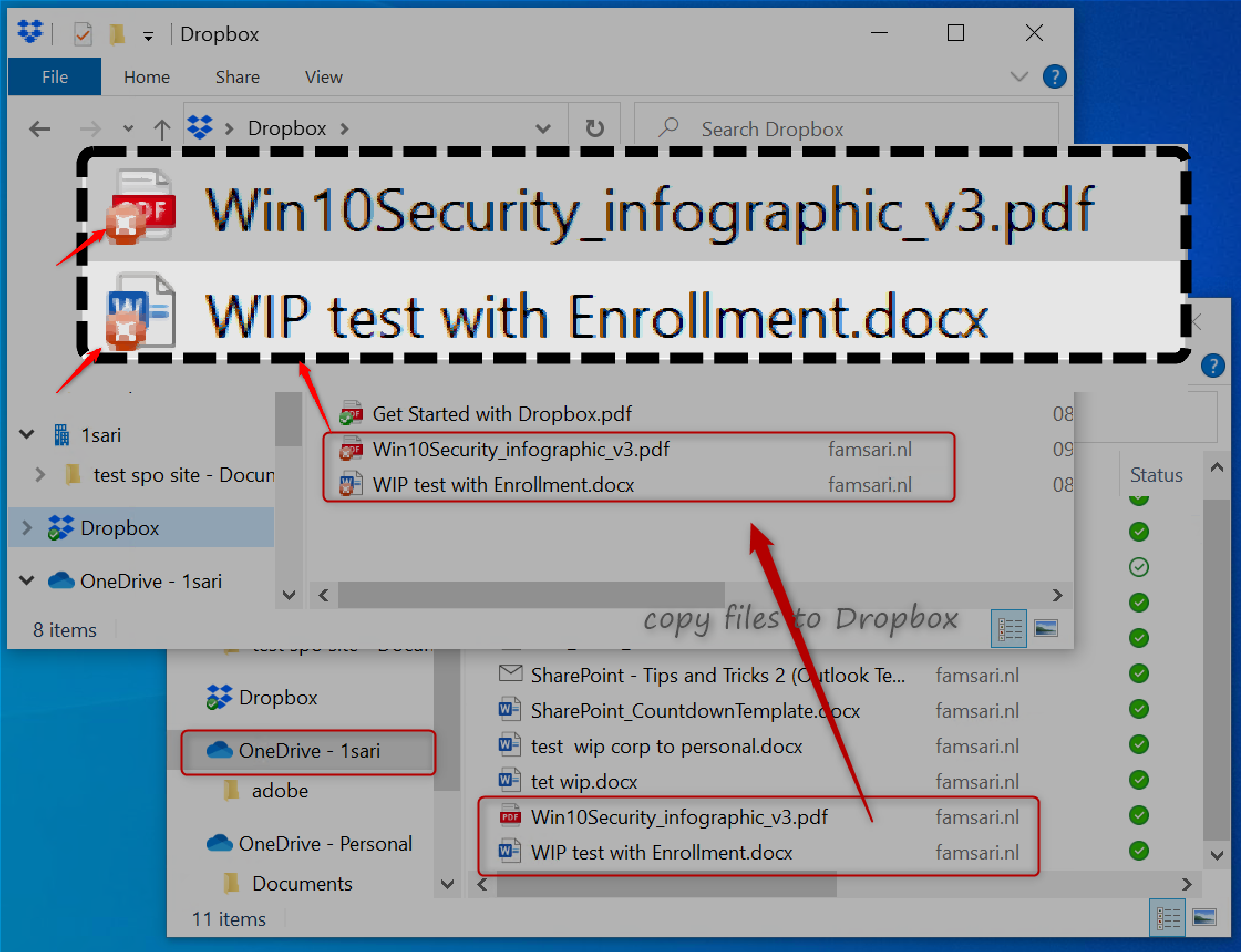
And again, I cannot change the File ownership from work to private because I have set the ‘Windows Information Protection mode’ to Block.
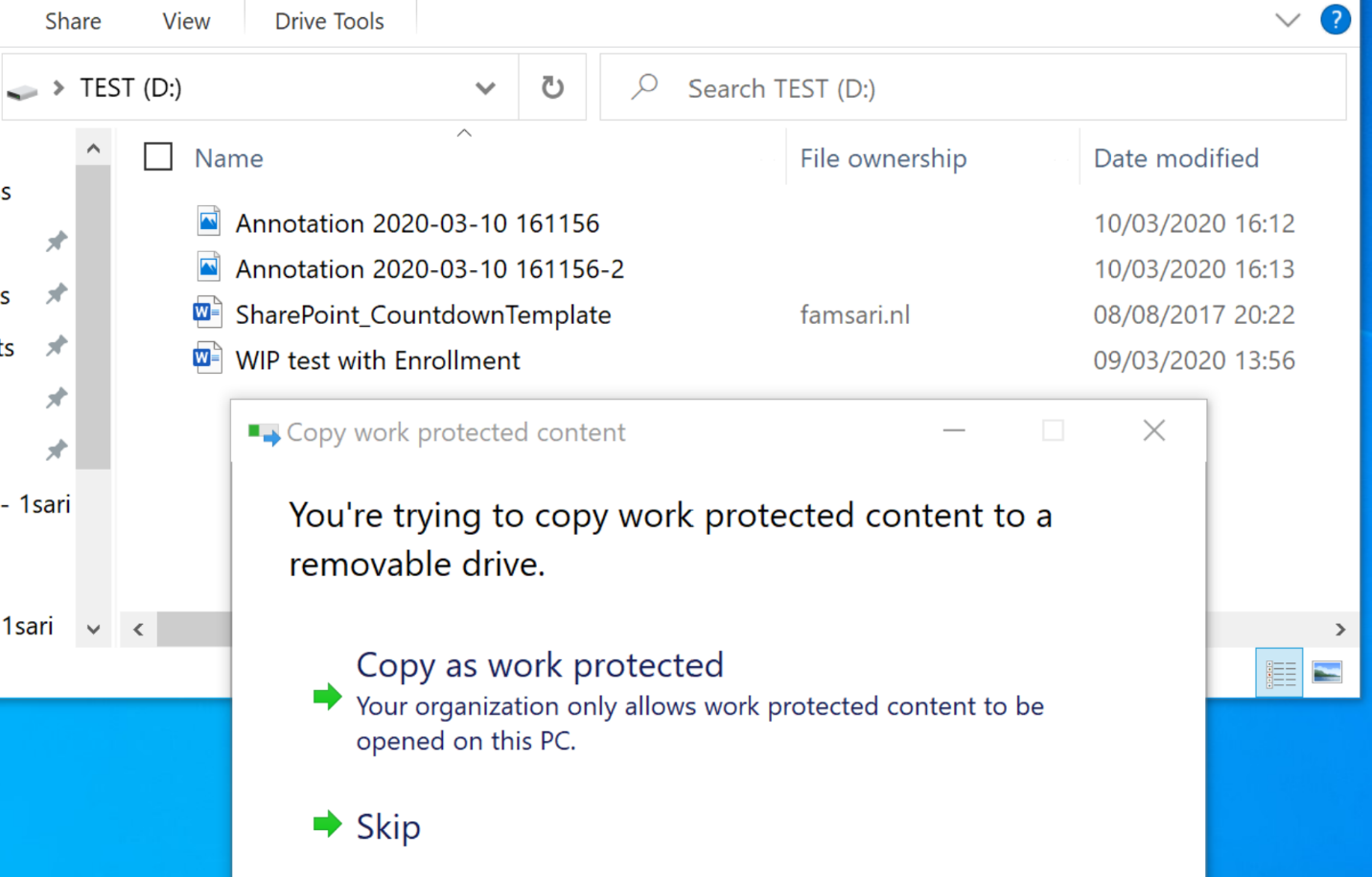
Relocating WIP-WE protected files to USB drives
When you set the ‘Windows Information Protection mode’ to Block, you will only have the option to copy data to a USB drive as work protected or skip the operation.
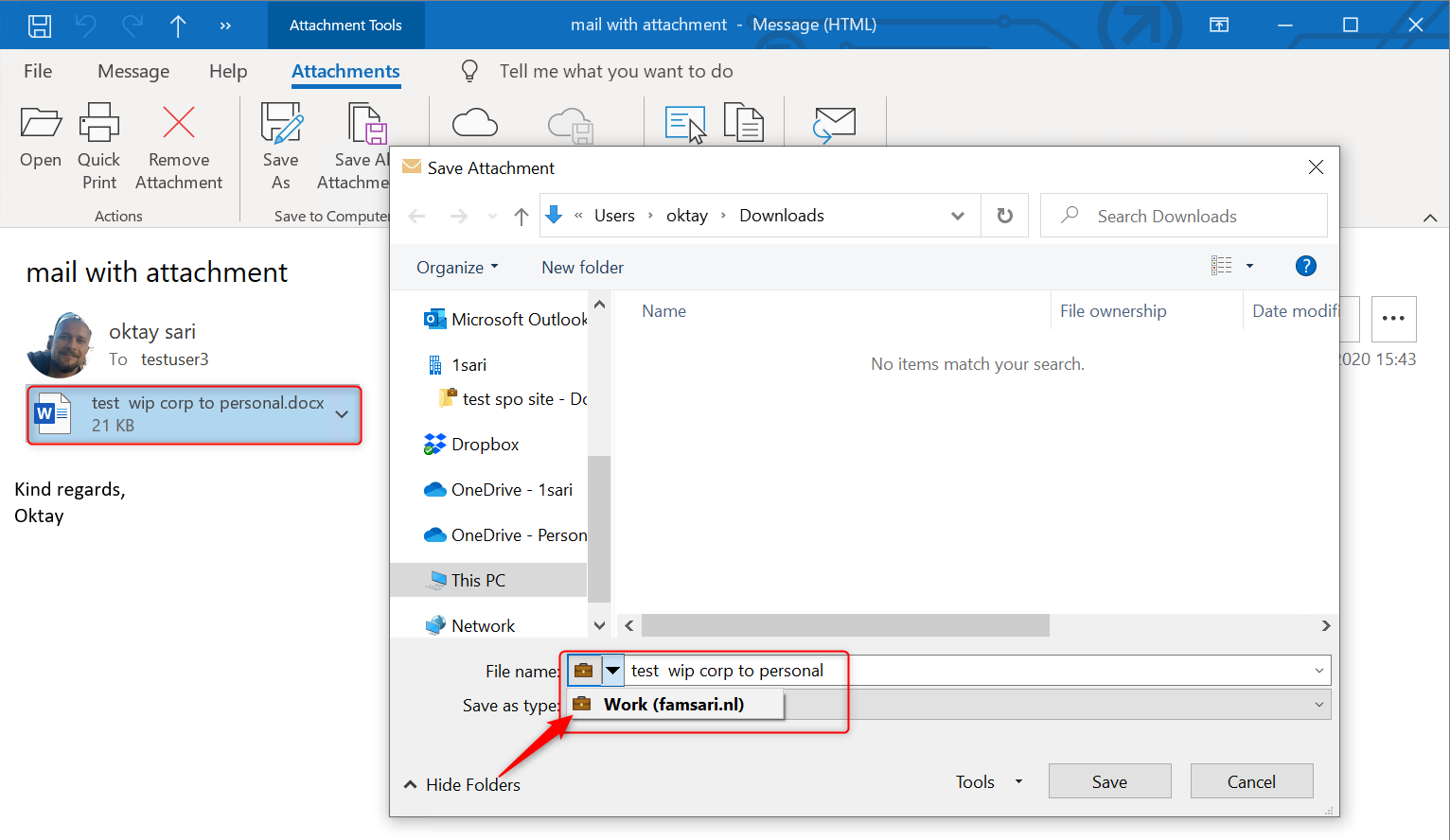
Saving attachments from e-mails
When I open an e-mail with an attachment, I can save it as usual, but the file will be protected with WIP wherever I save the file. If I had set the WIP Protection Mode to Allow Override, I would have the option to save this file as a personal file. With my WIP Protection Mode set to Block, I only have the option to save files in a corporate context.
Conclusion
WIP is a robust solution for protecting corporate data. Firstly, It can separate personal and work data. Secondly, WIP helps prevent unintentional information sharing. And this makes WIP a good choose for companies wanting to support a BYOD scenario. In addition, combined with AIP it adds an extra layer of security making it possible for your users to share data among each other.
As with other methods used to protect information and devices, you need to find a good balance between security and business productivity. If users set their mind on stealing information, they will find a way. Lucky for us admins, most users don’t have malicious intent.
H Otkay, I’m a big fan of your blog and find the articles really helpful when trying to deploy new Azure and Intune stuff onto the network I manage! I thought you might want to be aware (and perhaps draw awareness to) a serious limitation in Windows Information Protection that I’ve just come across: https://github.com/MicrosoftDocs/windows-itpro-docs/issues/6172 It appears that Windows Information Protection does not protect Outlook OST and PST files for remote wipe or encryption by default. This means if Outlook is used in Cached Exchange Mode (the default), any mailbox data downloaded by Outlook will not be removed as part… Read more »
Hi Chris, First of all, thank you for your kind words! Yeahhh, This one’s bothering me for quite some time. I’m aware of this and thought about writing a separate blog about it or mention it in the troubleshoot post for this series. I did do some research on it and I think I’ll add an extra post for this series about known issues and limitations. I posted a reply/comment on the uservoice and voted for it. The comment is the same like below: I have a WIP policy configured for devices without enrollment (WIP-WE) and WIP protection mode is… Read more »
Hi guys, a follow up on this would be much appriciated! I think WIP-WE is great in many ways, but you have to understand the limitations. What about all the different browsers on the BYOD for example. Cheers!
“WIP-WE works only when a device is Azure AD registered.”
Thanks you so much for this info , trying to find out why my policy wasn’t deploying
Is there any way to enforce this though? We are currently in testing phase and we have a couple of users who are never prompted to register their personal device in azure. They sign into the teams application and the devices is still unregistered and no account is added to access work or school. This also applies to the checkmark “Allow my organization to manage my device”. If the user removes this checkmark than app protection is not enforced but they still have full access to the applications. There is a policy for this in conditional access but only ios\android… Read more »
Hi Kim, have a look at conditional access & terms of use. It’s a workaround but get’s the job done. https://docs.microsoft.com/nl-nl/azure/active-directory/conditional-access/terms-of-use
Great article. Very helpful. One key limitation I’ve come across is WIP-WE only supports one managed identify. If the user has already enrolled their device with a different MDM/MAM provider from a different organization then WIP-WE won’t apply even if you force device registration via the conditional access + terms of use workaround. It would be nice if you could at least block access if WIP-WE isn’t applied.
It’s a shame they created this technology but it can’t be used to guarantee protection. I know they state that it’s not designed to guarantee protection. But why even create it then.
I’ve setup a test WIP policy without enrolment, it’s working fine in that englightened apps show their enterprise context correctly and I can’t copy/paste from them to non protected apps etc.. However, how do you prevent 3rd party browsers from accessing cloud resources that are defined under network boundaries? I have the boundaries configured per MS documentation, but using Chrome I’m able to access <company>.sharepoint.com without being blocked.. Ironically if I don’t add MsEdge – WIPMode-Allow – Enterprise AppLocker Policy File.xml as a protected app then it’s unable to access the cloud resources defined under network boundaries.. yet Firefox and… Read more »
Hi James, I’m getting the same issue. I’ve setup WIP-WE and have the cloud resources defined and this works for Edge and Office apps. However when using Chrome/Firefox I can also connect to portal.office.com, login, open OneDrive download files from the same account and they aren’t blocked. If I try to upload a file into O365 via Chrome I do get blocked as its treating the Chrome O365 as personal. However it doesn’t make sense to me that you can log into O365 and access/download files from OneDrive for Business and copy contents to WordPad etc. This seems to be… Read more »
Hi Carl, Thanks for your comments. Please see Eric’s comment below for my reply.
Thanks Oktay. As you have said below, the only options are to use the access restrictions within SharePoint and Exchange Online to limit file download etc. Otherwise with WIP-WE users can user firefox/chrome etc and access corporate data with no restriction. We have decided that there are too many limitations to WIP-WE for windows BYOD and have decided not to implement this. Here’s hoping Microsoft release something new in this are for App Protection on windows.
I to am having the same issue. I have gone through and looked into everything I can think of and I still can not get it to make the files from sharepoint to be corporate files from either Firefox or Chrome. I can get it to work correctly from the new version of Edge. The only option I can think of it to force the MAM users to use Edge. I dont know about anyone else but I am sure that will not go over in my company.
Hi Eric, there are a lot of thing that are good about WIP-WE but this one, is not so good. You cannot get Firefox or Chrome to mark files as corporate on a BYOD that is only registered in Azure AD without MDM. To better understand why, lets have a look at MDM enrolled devices: On a corporate device that is MDM enrolled in Intune, you can get it to work. But you have to understand that when unenlightened apps like Fireffox and Chrome are listed as allowed apps, everything you do in these browsers, is considered corporate. So reading… Read more »
Hi James, Thanks for sharing your thoughts. See Eric’s comment for my reply.
Thank you for information. WIP policies are working fine on my all users Workstations but one user is unable to log in to office 365 web apps from the chrome browser.also i want to allow users to access my company apps in Mozilla firefox.
I also ask for support to the Microsoft Azure support but i don’t think so that support can help me, can someone please tell me what exactly i can do for that single user.
Thank you for the great article. I have an issue with email attachments containing pdf files. Opening the pdf attachment, I am able to copy paste content to unprotected app – i.e. notepad. With Word attachments the Block policy works. Can you please advise?
Hi Nick,
Could you share a little more info about your config? I’ve tested this with the following setup: Protection Mode set to Block. send e-mail from hotmail account with PDF to account in protected e-mail domain.
Tried to open PDF with Foxit and Adobe (both not in my allowed apps list). I got an access denied immediately.
When I try to save the attachment from Outlook, it saves the PDF as protected work data. Opened the PDF attachment with Edge browser. I was able to copy/past only to allowed apps. Same thing for word documents.
With your help, I was able to get this up and running, but I hit a snag later. Users were unable to open any files on their desktops and in their Documents folders (both of which are backed up to OneDrive). The error said that these locations weren’t work locations. Closing Onedrive made the files accessible again. I thought Desktop and Documents are supposed to be work locations by default. Am I missing something?
Hi Noel, Check your configured network boundaries. Did you include:domainname.sharepoint.com|domainname-my.sharepoint.com|domainname-files.sharepoint.com? When you sync Desktop and Documents to OdB, alle files are marked as corporate if you include -my.sharepoint.com with your network boundaries. When files are marked corporate, they stay encrypted on the local machine. So I don’t get why closing ObD would fix your problem. Also check the enterprise context of OdB in your taskmanager. It should show Enterprise context.
Thanks for the reply, Oktay. Sorry for not responding earlier. After giving up for a while, I tried creating a new policy, this time targeting enrolled devices only. I have conducted limited testing with a test group consisting of one user and, so far, it seems to be working as expected. I think you were right about the network boundaries being the issue. Originally, I configured the network boundaries based on the template you provided on one of your other pages in the series. I basically copied and pasted them, changing only contoso to my domain name. What probably happened… Read more »
[…] WIP-WE User Experience – WIP Without MDM enrollment […]
[…] WIP-WE User Experience – WIP Without MDM enrollment […]
[…] WIP-WE User Experience – WIP Without MDM enrollment […]
[…] WIP-WE User Experience – WIP Without MDM enrollment […]
Hi Oktay, I’m trying to work out how to stop people proceeding from the “This app only” stage. It looks like if you press that button, then you have a workaround and your device isn’t registered with Azure AD and no MAM policy is applied, and there is no encryption or separation of work and personal documents.
This seems like a security loophole.
Is there a setting or a Conditional Access Policy that can stop users getting around the MAM registration? (without forcing them to join the device to MDM)
Hi Jonti, You’re right. I have to say that Windows Information Protection has never ment to be impenetrable. There are ways to stop this on BYOD. Have a look at my latest blog post: https://allthingscloud.blog/blocking-byod-based-on-unsupported-os-versions/ in particular, the CA policy 2 is what you need. Maurice Daly also did a complete blog on just this topic: https://msendpointmgr.com/2022/03/11/securing-windows-mam-only-access-with-conditional-access/ Hope this helps
[…] WIP-WE User Experience – WIP Without MDM enrollment […]